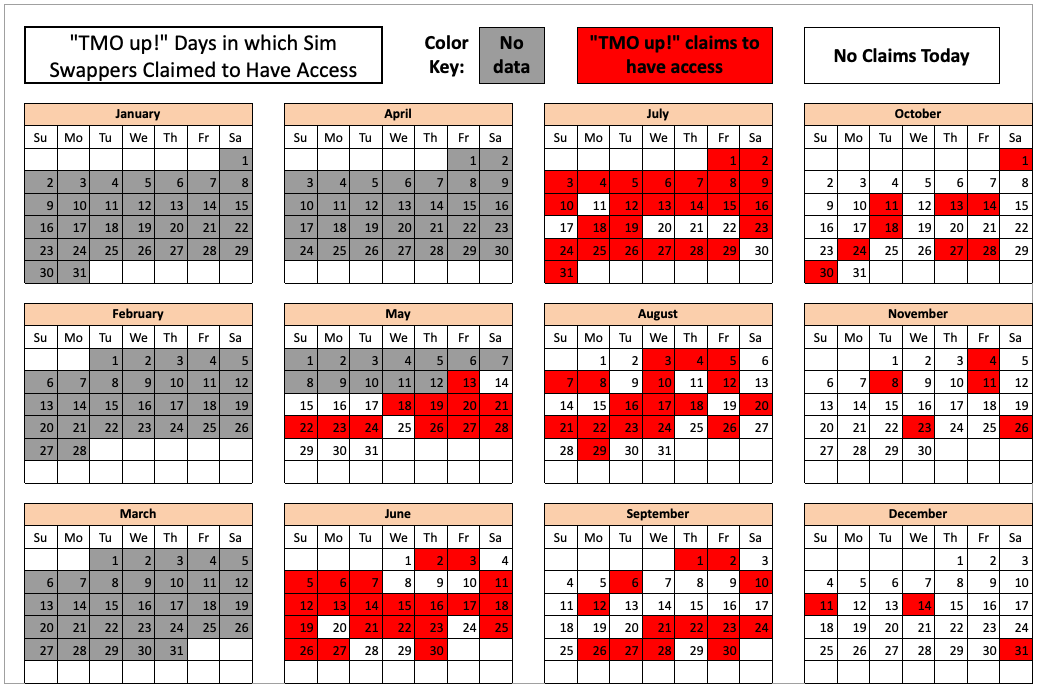
Windows JavaScript zero-day, Iran-based hack-and-leak, METRO
Por um escritor misterioso
Last updated 26 abril 2025

Exploited Windows zero-day lets JavaScript files bypass Mark of the Web security warnings According to Bleeping Computer, this has already been seen in ransomware attacks. Windows includes a security feature called Mark-of-the-Web (MoTW) that flags a file as having been downloaded from the Internet
Exploited Windows zero-day lets JavaScript files bypass security warnings

Twitter - Wikipedia
Risky Biz News: China cracks down on the SE Asia scam call center problem

Microsoft Patched Actively Exploiting Zero-day Vulnerability in Windows CLFS

Ransomware Attack List and Alerts - Cloudian

Threat Trends: DNS Security, Part 1 - Storcom, Lombard, Illinois, United States of America

Ethical hacking for IoT: Security issues, challenges, solutions and recommendations - ScienceDirect
Windows JavaScript zero-day, Iran hack-and-leak, METRO retailer attack

Cybersecurity News & Articles
Applied Sciences, Free Full-Text

PDF) SoK: Anatomy of Data Breaches





:strip_icc()/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2022/N/A/rGnDDlShSvLFpK0odRBw/iphone-13-vermelho-thassius-veloso-techtudo-08.jpg)