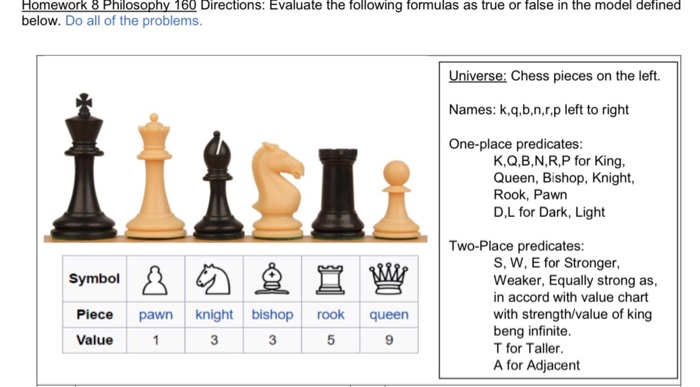
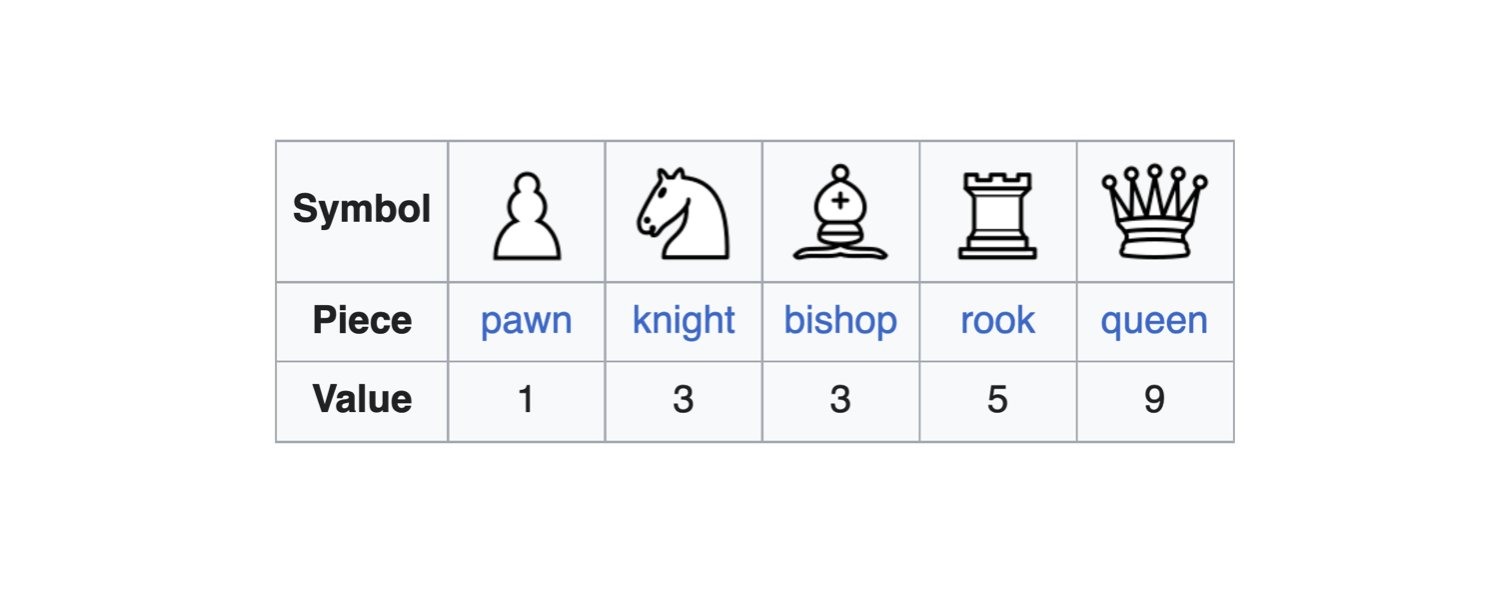
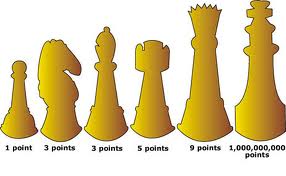
Playing Chess with the Adversary: Value in Security Controls
Por um escritor misterioso
Last updated 26 abril 2025


You Need Deception Technology. And It's Not Why You Think

Attack attribution: It's complicated
An Introduction to AI Model Security - WWT

America Is in a New Cold War With China

Using a Red Team To Boost Your Cyber Defences

Square Off Grand Kingdom Set, Automated Chessboard for Adults & Kids, World's Smartest Electronic Chess Board

DVIDS - News - JBB Chess Tournament tests decision-making skills

DVIDS - News - JBB Chess Tournament tests decision-making skills

The Art of Cybersecurity Strategy - Lessons from a Chess Master 🤝

Moving Risk Management From Fear and Avoidance to Performance and Value

Together, We Cultivate Doubt in Our Adversaries - National Defense Transportation Association

Forget the rules. Cyber Security is like playing chess with a pigeon

A Beginner's Guide to Cyber War, Cyber Terrorism and Cyber Espionage - Security Boulevard










![Update] Changes to Asset Privacy for Audio - #1034 by GazilionGrandGadgets - Announcements - Developer Forum](https://devforum-uploads.s3.dualstack.us-east-2.amazonaws.com/uploads/optimized/4X/1/a/a/1aa4a7fbdd8b1ac8e7e707e52caa2bf64b6ceb53_2_690x325.png)

