Cybercriminals are shapeshifting to evade security controls
Por um escritor misterioso
Last updated 26 abril 2025


Polymorphic Malware Using #AI

Cyber Defense eMagazine March Edition for 2022

Microsoft Teams Phishing Used By Ransomware Access Broker
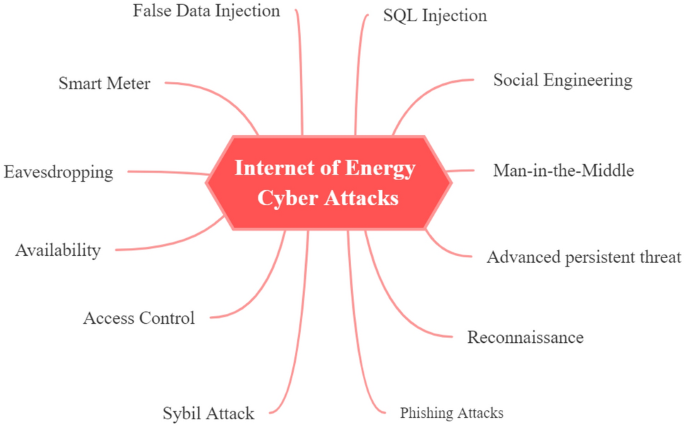
A survey on internet of energy security: related fields, challenges, threats and emerging technologies

Surge in malware & encrypted traffic reveals shape-shifting tactics of hackers - Tech Monitor

What is Emotet? A Simple Guide to the Malware Threat
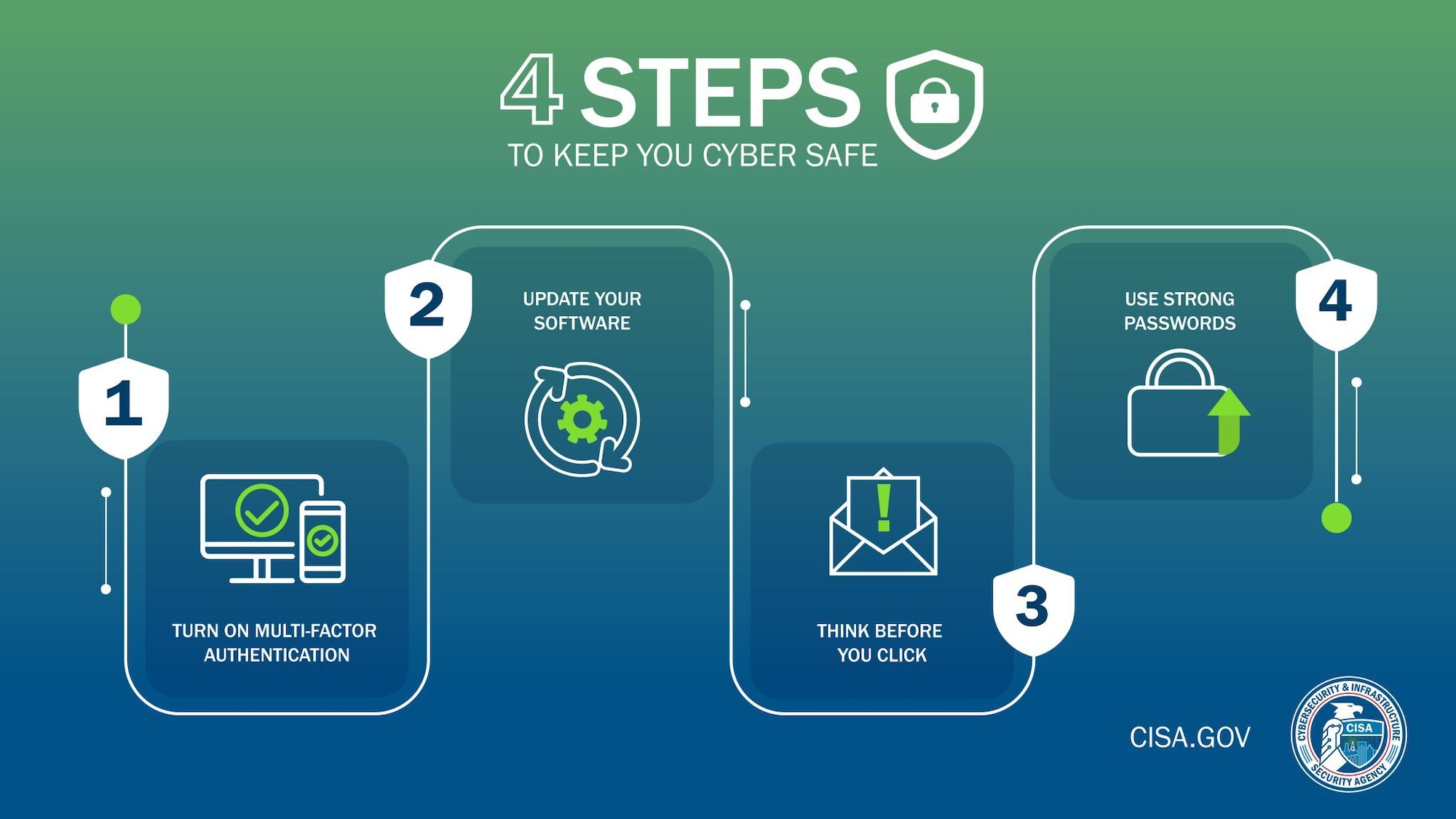
See Yourself in Cyber- a call to action from CISA > Air Force Global Strike Command AFSTRAT-AIR > Article Display

What Are The Different Types of Computer Viruses?

Ransomware Attacks: You Can't Protect What You Can't See

Overview of the Overall Technical Flow for the Malicious Websites
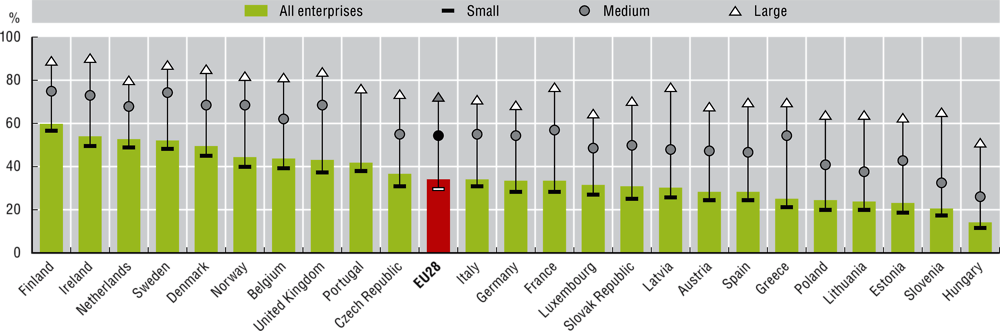
Chapter 7. Digital security, OECD Digital Economy Outlook 2020

![OP Evade Script GUI [FREE]](https://vapouryt.co.uk/wp-content/uploads/2022/09/evade-script.jpg)







/origin-imgresizer.eurosport.com/2023/09/21/3789696-77083848-2560-1440.jpg)



![Darth Vader : Star Wars Battlefront 2 [4KTextures][Add-on]](https://img.gta5-mods.com/q75/images/darth-vader-star-wars-battlefront-2-4ktextures-add-on/2997c4-MAININMA.png)




