Origin browser protocol exploit shown to execute malicious software with a single click
Por um escritor misterioso
Last updated 15 março 2025

A security flaw has surfaced in the browser protocol Origin uses to launch games through custom links using the
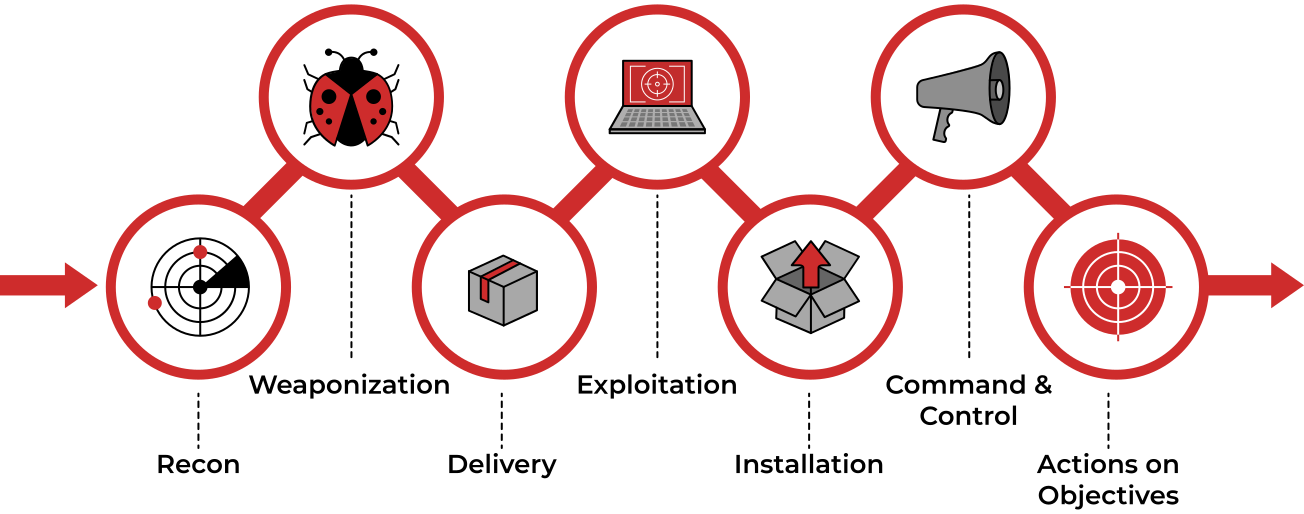
TryHackMe Cyber Kill Chain Room. The Cyber Kill Chain framework is
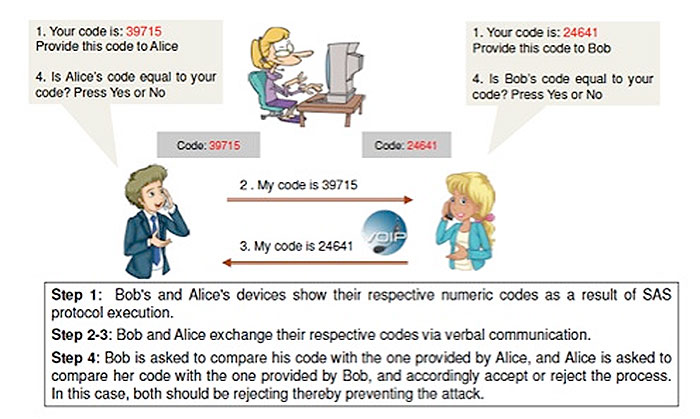
Wiretapping via Mimicry: UAB Research Highlights a Fundamental

Researchers Warn of Unpatched DogWalk Microsoft Windows
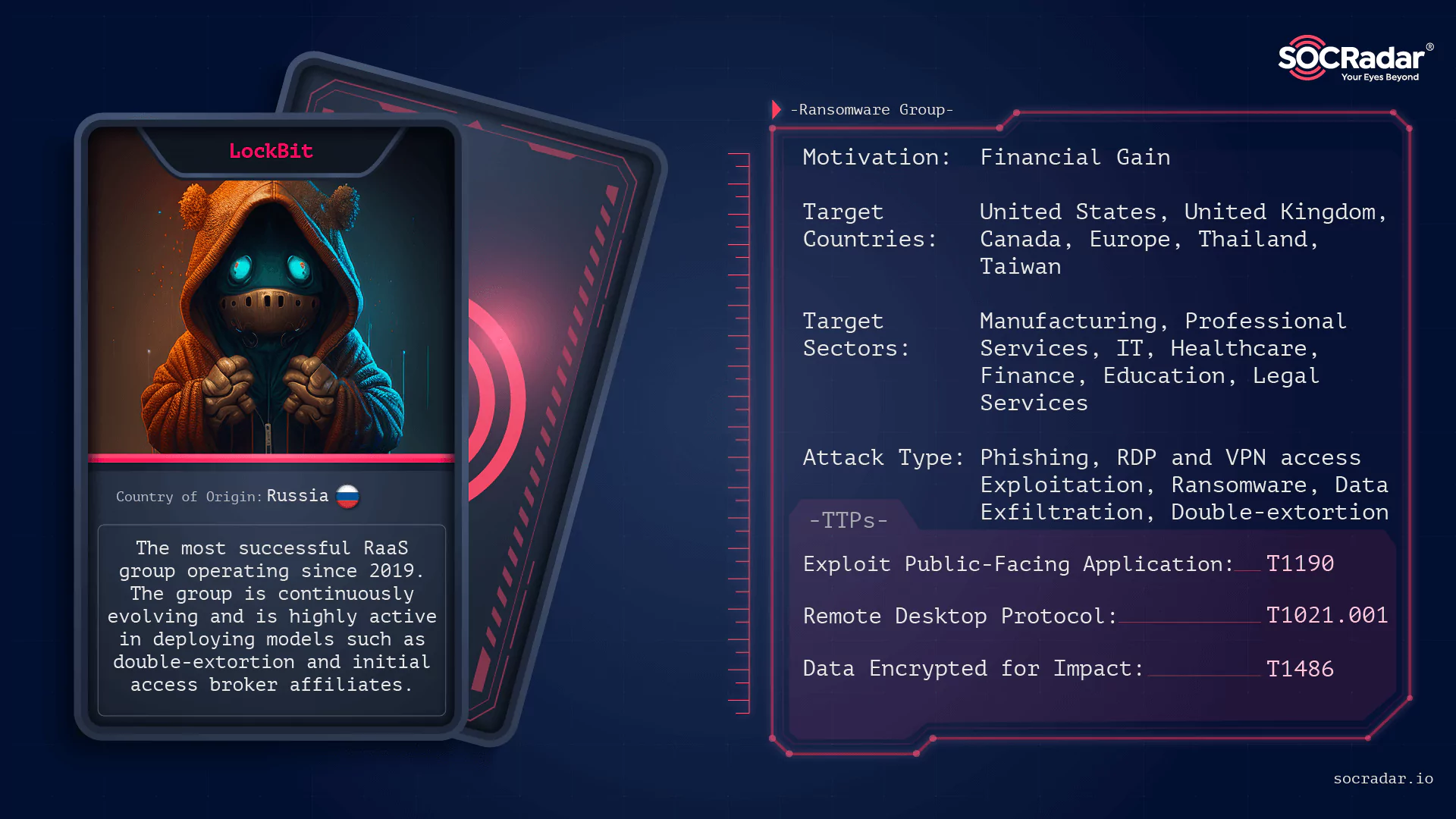
Dark Web Profile: LockBit 3.0 Ransomware - SOCRadar

Exploit the Fuzz – Exploiting Vulnerabilities in 5G Core Networks

Open redirects: real-world abuse and recommendations

DDoS threat report for 2023 Q2

7 Common Authorization Vulnerabilities

Apple Bug Exposed Chat History With a Single Click - The Intercept

Valve Steam Platform Exploit Exposed, Remote Code Execution
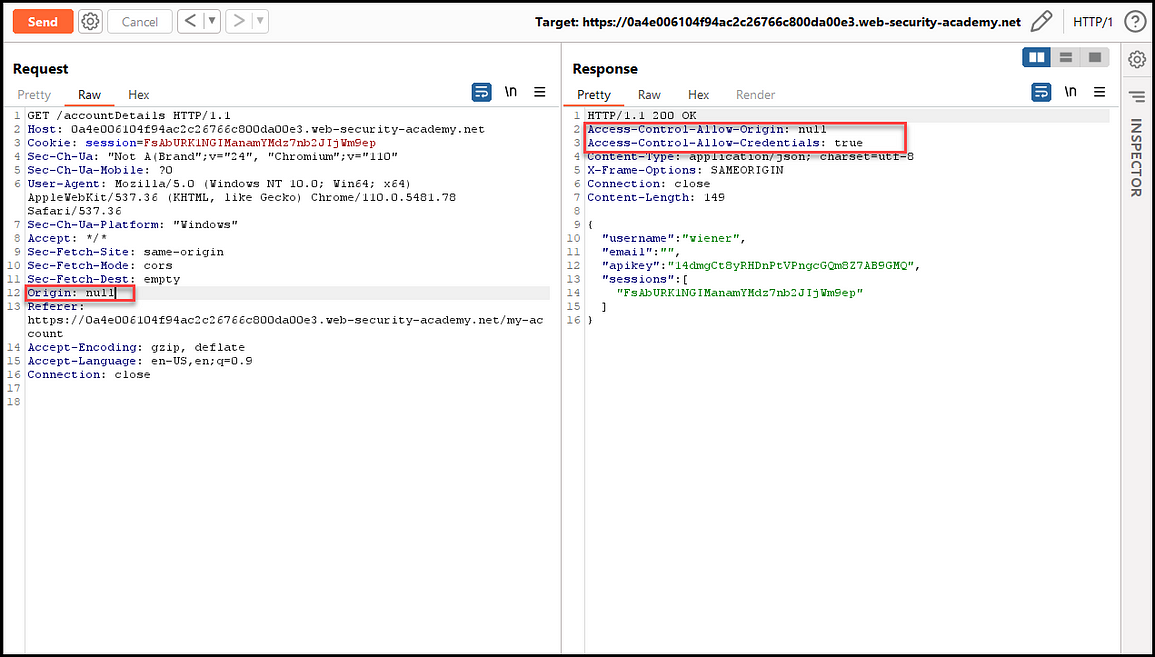
Exploiting CORS – How to Pentest Cross-Origin Resource Sharing

Exploring Cross-Site Request Forgery (CSRF) vulnerabilities: Still

Dark Web Profile: NoEscape Ransomware

WhatsApp flaws could have allowed hackers to hack mobile devices


















![EA SPORTS FC 24 Standard - Steam PC [Online Game Code] : Everything Else](https://m.media-amazon.com/images/W/MEDIAX_792452-T2/images/I/71ItxRgZ6hL._AC_UF1000,1000_QL80_.jpg)