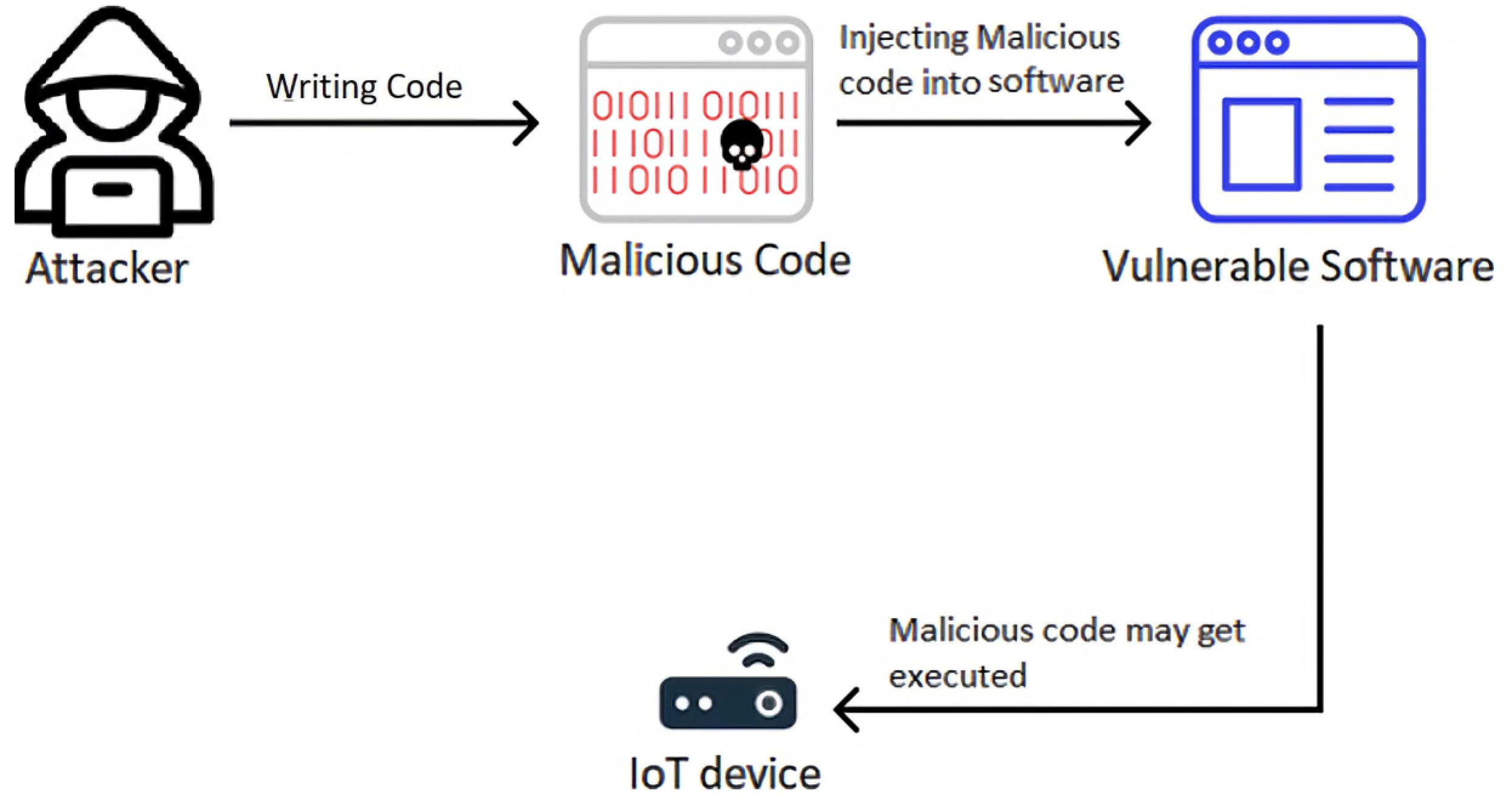
Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Last updated 26 abril 2025

Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store
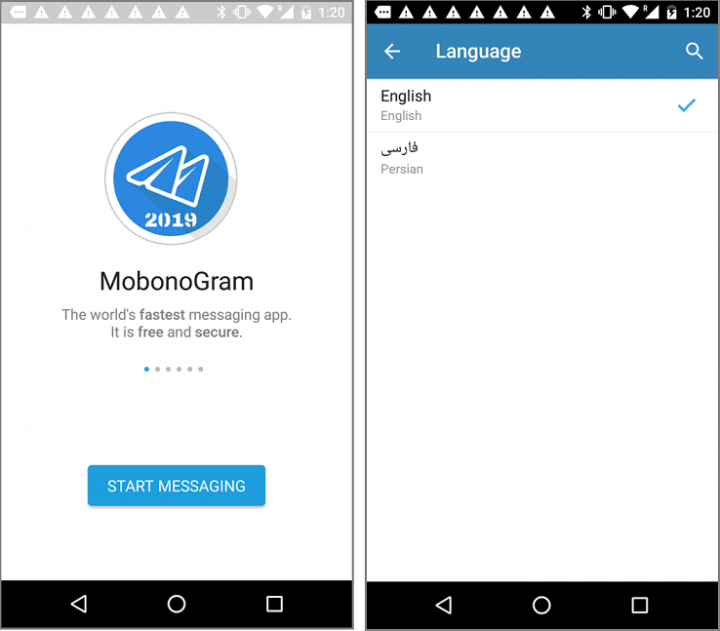
Unofficial Telegram App Secretly Loads Infinite Malicious Sites
Dynamic analysis and tampering

Basic principle of code reuse attacks. For simplicity, we
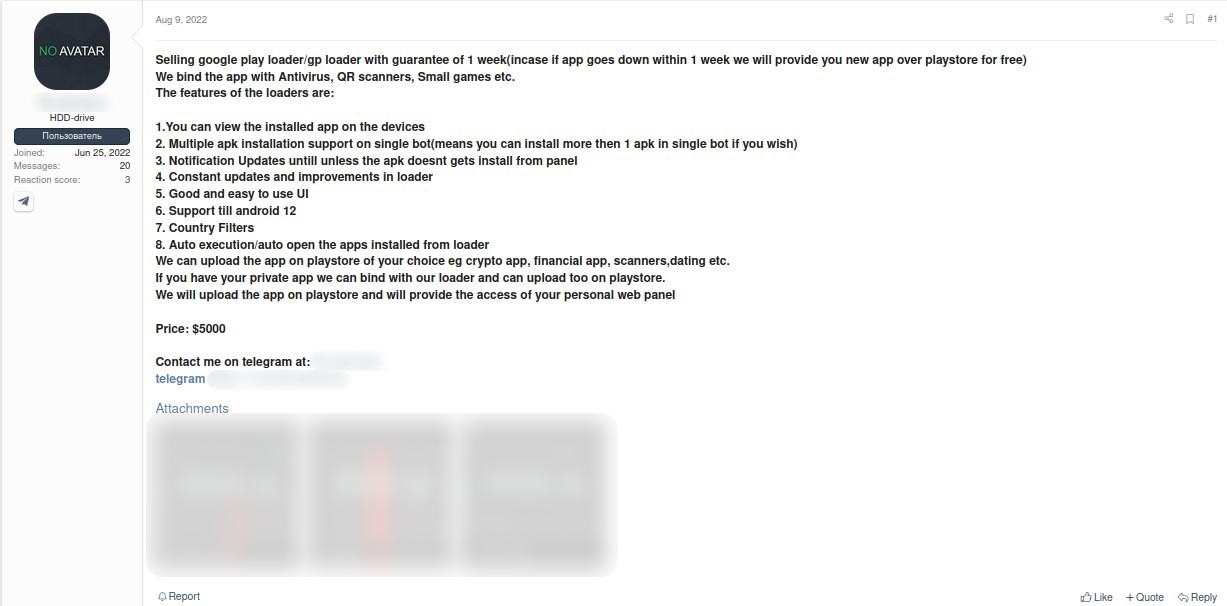
Google Play threat market: overview of dark web offers

Malicious Apps Use Sneaky Versioning Technique to Bypass Google
Sensors, Free Full-Text

Dynamic analysis and tampering
Google Chrome - Wikipedia
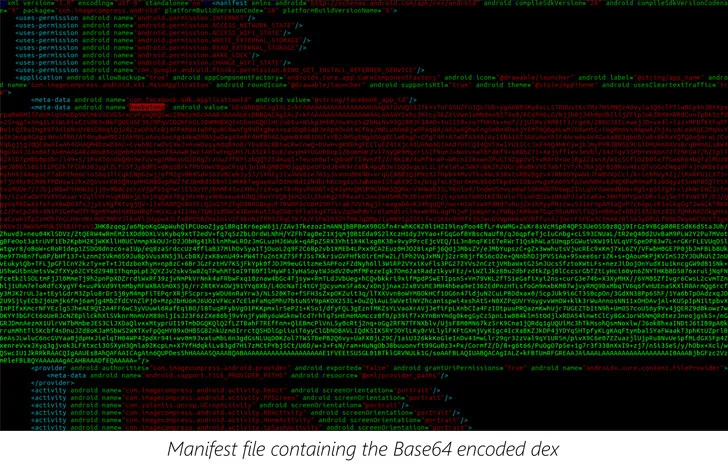
Bypass malware detection in Google Play Store with Dynamic Code
Joker Malware Apps Once Again Bypass Google's Security to Spread