PDF] Power Consumption-based Detection of Sabotage Attacks in
Por um escritor misterioso
Last updated 26 abril 2025
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://d3i71xaburhd42.cloudfront.net/d81c8d2816032b4abc1798383f88d5a376d17a75/4-Figure1-1.png)
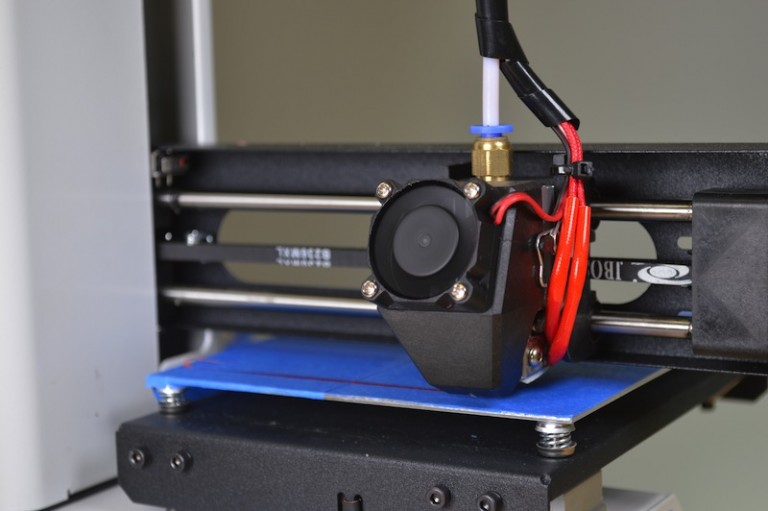
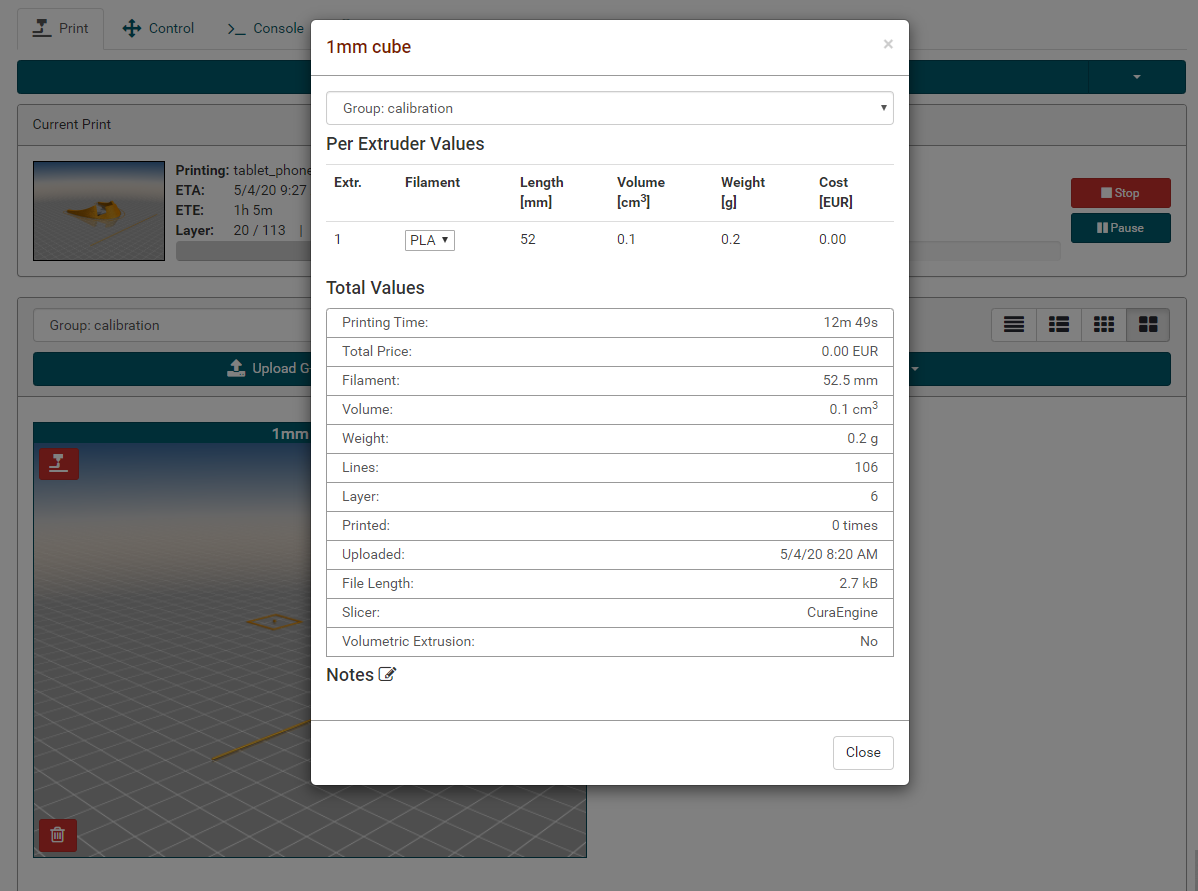
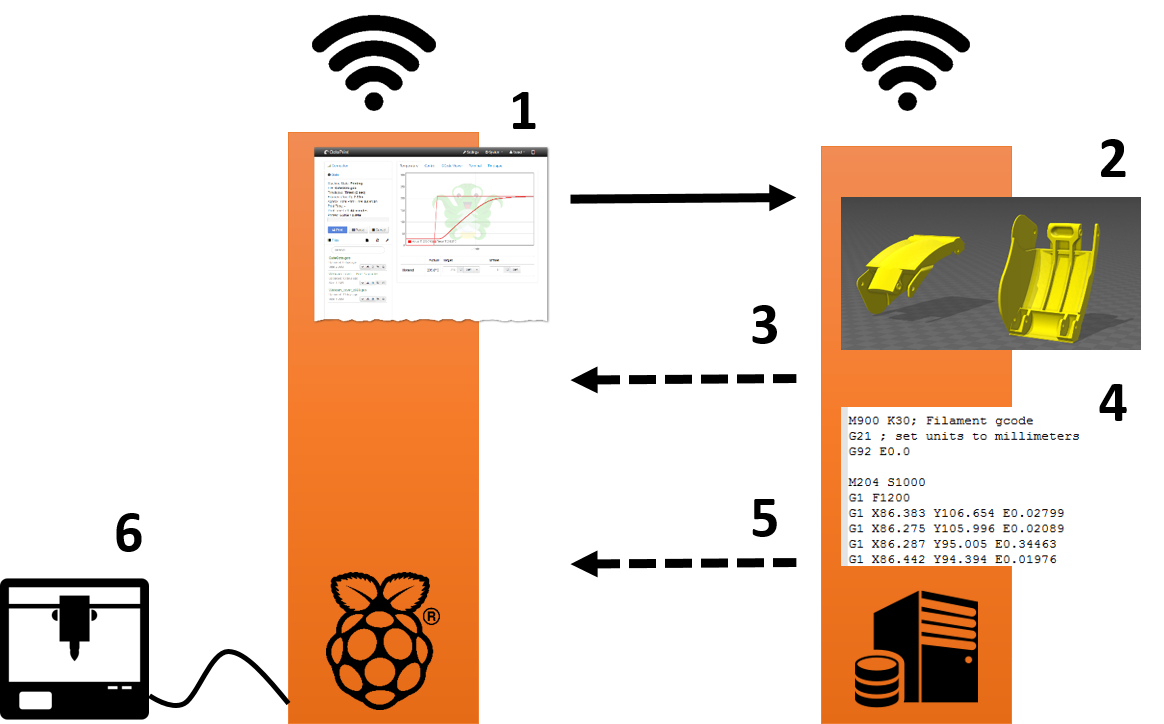
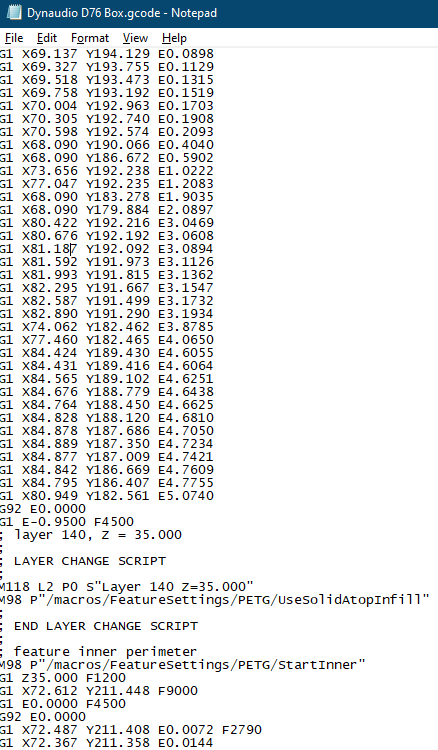
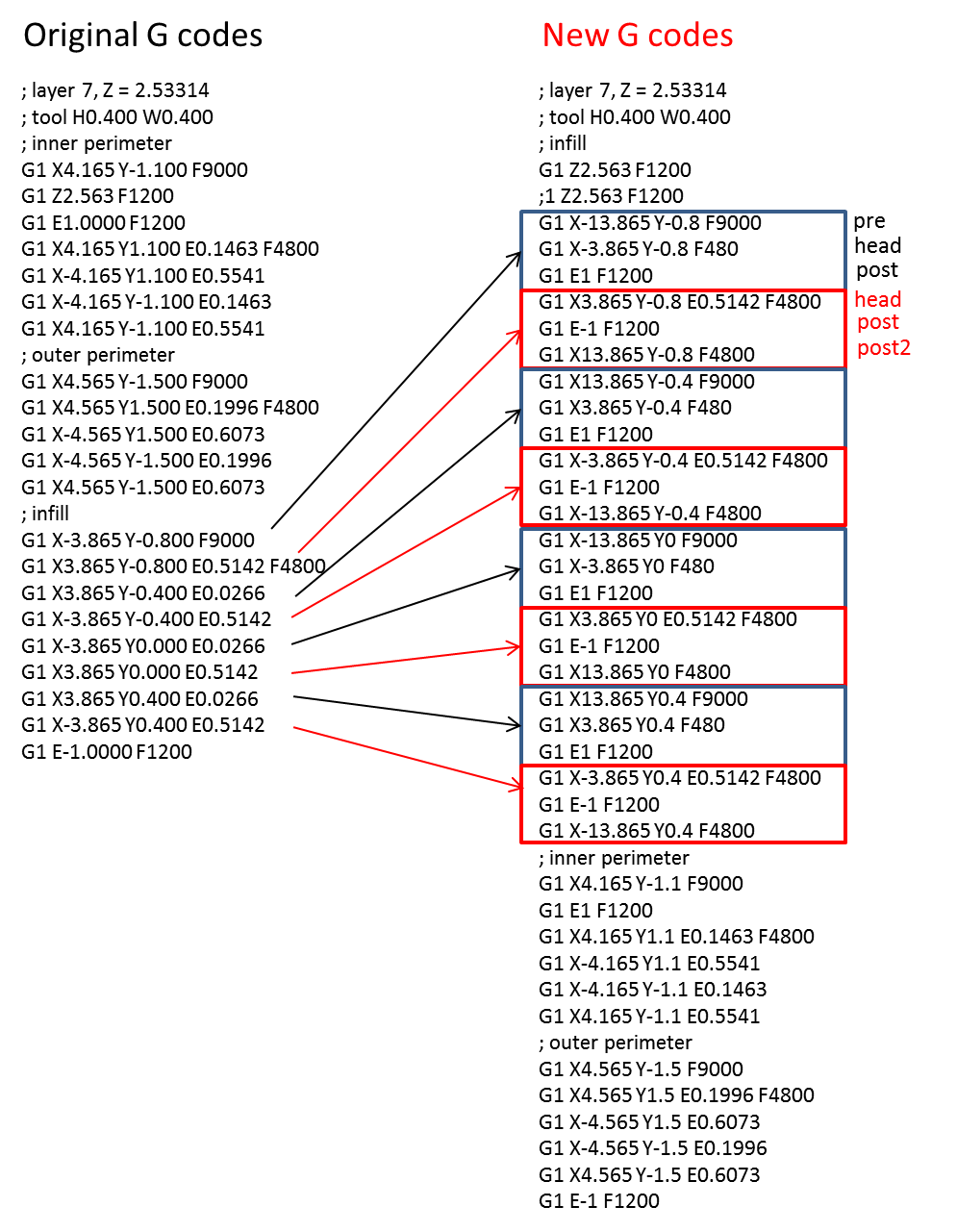
This work proposes a novel approach for detecting sabotage attacks in additive Manufacturing, based on continuous monitoring of the current delivered to all actuators during the manufacturing process and detection of deviations from a provable benign process. Additive Manufacturing (AM), a.k.a. 3D Printing, is increasingly used to manufacture functional parts of safety-critical systems. AM's dependence on computerization raises the concern that the AM process can be tampered with, and a part's mechanical properties sabotaged. This can lead to the destruction of a system employing the sabotaged part, causing loss of life, financial damage, and reputation loss. To address this threat, we propose a novel approach for detecting sabotage attacks. Our approach is based on continuous monitoring of the current delivered to all actuators during the manufacturing process and detection of deviations from a provable benign process. The proposed approach has numerous advantages: (i) it is non-invasive in a time-critical process, (ii) it can be retrofitted in legacy systems, and (iii) it is airgapped from the computerized components of the AM process, preventing simultaneous compromise. Evaluation on a desktop 3D Printer detects all attacks involving a modification of X or Y motor movement, with false positives at 0%.
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://www.researchgate.net/profile/Mark-Yampolskiy/publication/319524597/figure/fig1/AS:535794353356802@1504754736685/Considered-Threat-Model_Q320.jpg)
PDF) Power Consumption-based Detection of Sabotage Attacks in Additive Manufacturing
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://www.tandfonline.com/cms/asset/df6e38b5-c80d-4264-8c5d-ee36045dbe67/tsma_a_1972914_uf0001_oc.jpg)
Full article: IoT-Based Intrusion Detection Systems: A Review
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://image.slidesharecdn.com/lightsecforutilitiesandcriticalinfrastructurewhitepaper-160912065753/85/light-sec-for-utilities-and-critical-infrastructure-white-paper-1-320.jpg?cb=1670704168)
Light sec for utilities and critical infrastructure white paper
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://i1.rgstatic.net/publication/364259078_Cyber_Security_of_Smart_Metering_Infrastructure_Using_Median_Absolute_Deviation_Methodology/links/6341721c9cb4fe44f3119eb2/largepreview.png)
PDF) Cyber Security of Smart Metering Infrastructure Using Median Absolute Deviation Methodology
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://www.mandiant.com/sites/default/files/inline-images/hacktivist-ot-fig5.png)
We (Did!) Start the Fire: Hacktivists Increasingly Claim Targeting of OT Systems
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://media.springernature.com/m685/springer-static/image/art%3A10.1038%2Fs41598-023-40273-8/MediaObjects/41598_2023_40273_Fig9_HTML.png)
A cluster-based trusted routing method using fire hawk optimizer (FHO) in wireless sensor networks (WSNs)
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://engineering.jhu.edu/magazine/wp-content/uploads/2022/05/carousel-3.jpg)
Thwarting Cyberattacks - JHU Engineering Magazine
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://ars.els-cdn.com/content/image/1-s2.0-S2666546821000495-fx1.jpg)
Data-driven approaches for cyber defense of battery energy storage systems - ScienceDirect
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://www.frontiersin.org/files/Articles/850056/fsens-03-850056-HTML/image_m/fsens-03-850056-g006.jpg)
Frontiers Hardware Security in Sensor and its Networks
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://www.researchgate.net/publication/334407323/figure/fig1/AS:779804655747073@1562931326870/Power-Traces-of-X-Y-Z-and-Extruder-motors-top-to-bottom_Q320.jpg)
PDF) Detecting Sabotage Attacks in Additive Manufacturing Using Actuator Power Signatures
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://www.researchgate.net/profile/Shih-Yuan-Yu/publication/339059143/figure/fig2/AS:855393395806208@1580953086899/Attack-vectors-on-the-AM-process-chain_Q320.jpg)
PDF) Sabotage Attack Detection for Additive Manufacturing Systems
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://d3i71xaburhd42.cloudfront.net/507897340a3d52a6f4426e18dbe154e521a65802/77-Figure10-1.png)
PDF] Comparing Insider IT Sabotage and Espionage: A Model-Based Analysis
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://pub.mdpi-res.com/computers/computers-12-00256/article_deploy/html/images/computers-12-00256-g005.png?1702023399)
Computers, Free Full-Text
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://d3i71xaburhd42.cloudfront.net/d81c8d2816032b4abc1798383f88d5a376d17a75/13-Figure9-1.png)
PDF] Power Consumption-based Detection of Sabotage Attacks in Additive Manufacturing
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://imgv2-1-f.scribdassets.com/img/document/21008921/298x396/355aedba87/1642624460?v=1)
Simple Sabotage Field Manual, PDF, Project Gutenberg