Towards an Automated Process to Categorise Tor's Hidden Services
Por um escritor misterioso
Last updated 26 abril 2025
Hidden service search engine and naming strategy

Can you trust Tor's hidden service directories? – Sophos News
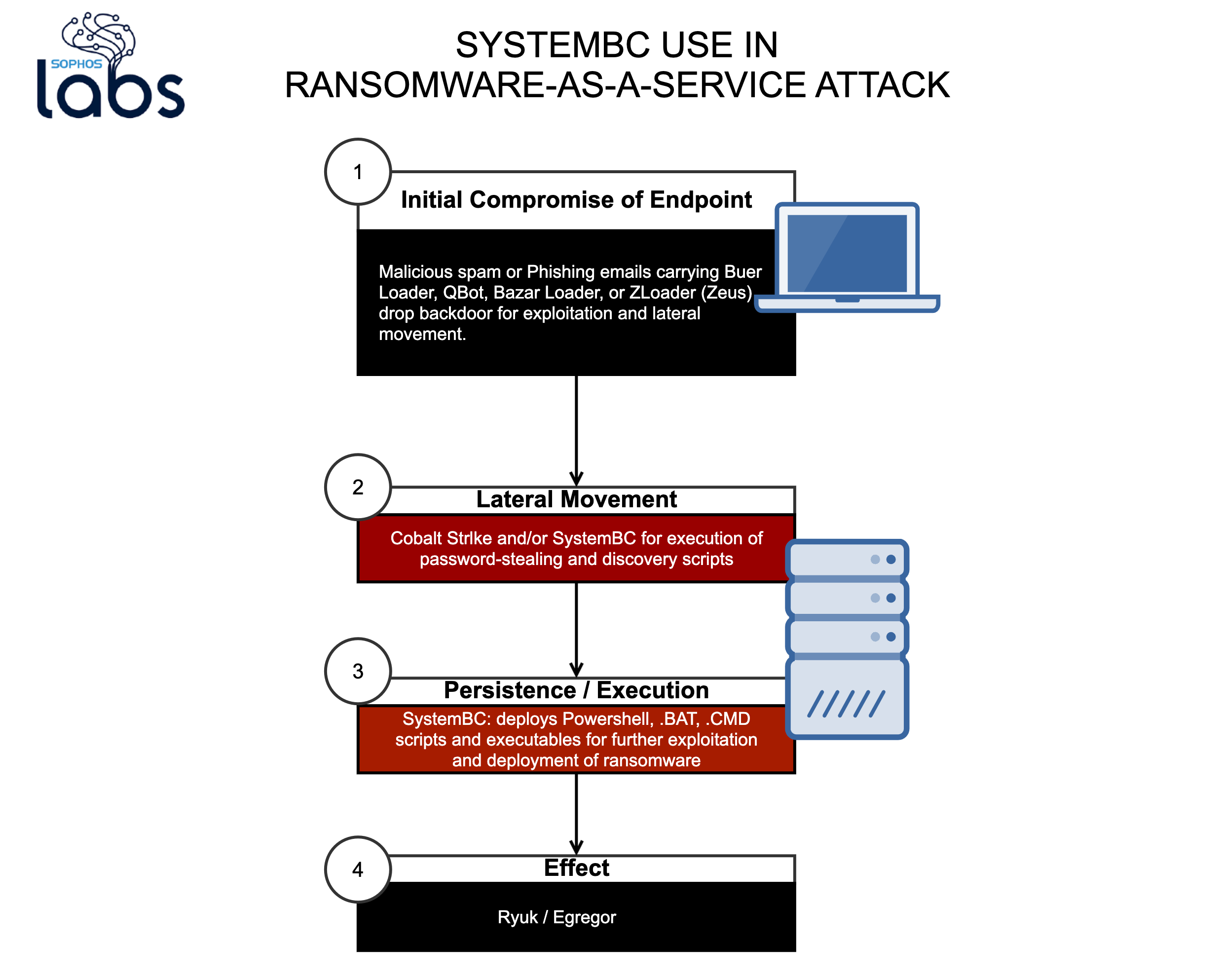
Ransomware operators use SystemBC RAT as off-the-shelf Tor backdoor – Sophos News

A deep learning‐based framework to identify and characterise heterogeneous secure network traffic - Islam - 2023 - IET Information Security - Wiley Online Library

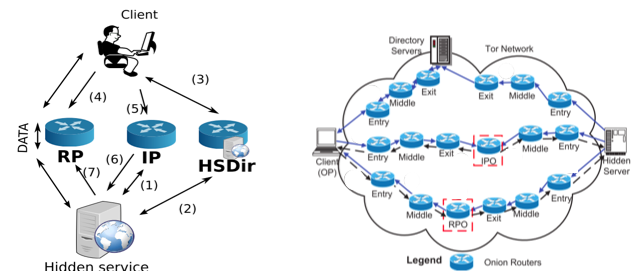
Figure 1 from Application-level attack against Tor's hidden service

Web 3.0 Explained: A Comprehensive Guide

JCP, Free Full-Text

The rise of website fingerprinting on Tor: Analysis on techniques and assumptions - ScienceDirect

The Art of Invisibility: The World's Most by Mitnick, Kevin

COMP4337 - Tor Flashcards

E-Book: HOW TO SETUP TOR HIDDEN SERVICES

Towards an Automated Process to Categorise Tor's Hidden Services













/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/y/H/pTSO8DQU6VgejC38Dr5w/2014-10-01-41.jpg)
