Cryptographic Keys 101: What They Are & How They Secure Data - Hashed Out by The SSL Store™
Por um escritor misterioso
Last updated 15 março 2025

Cryptographic keys, in combination with an encryption algorithm, disguise data (encryption) so only a special key can access it (decryption).

cryptography security

What is a Pass-the-Hash Attack? - CrowdStrike
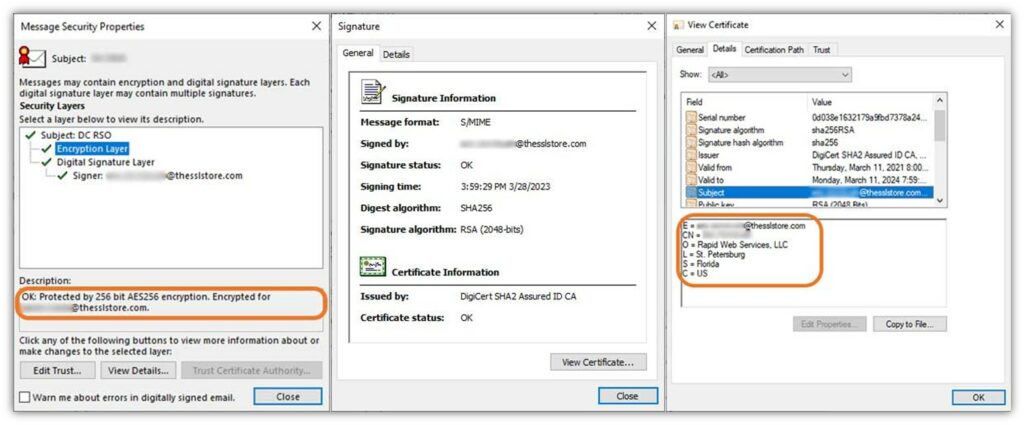
Cryptographic Keys 101: What They Are & How They Secure Data
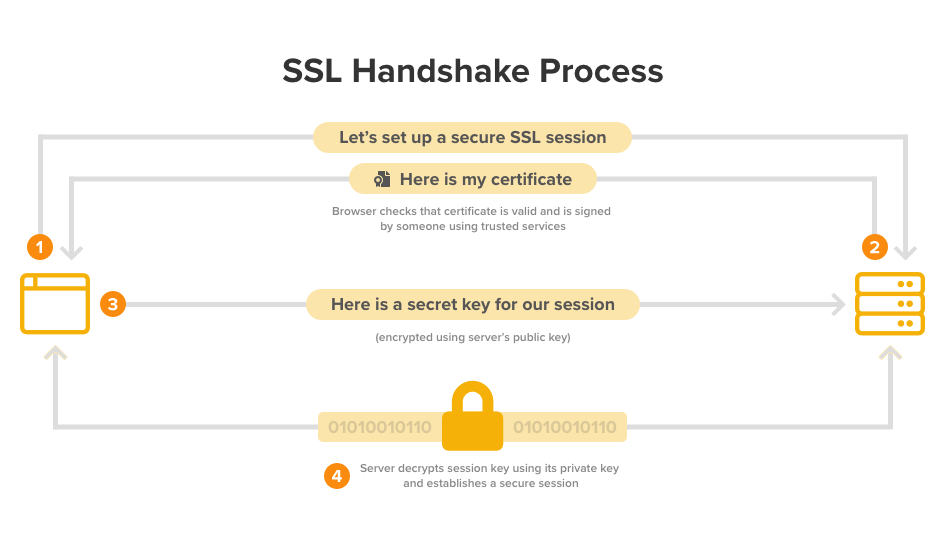
Cryptography 101
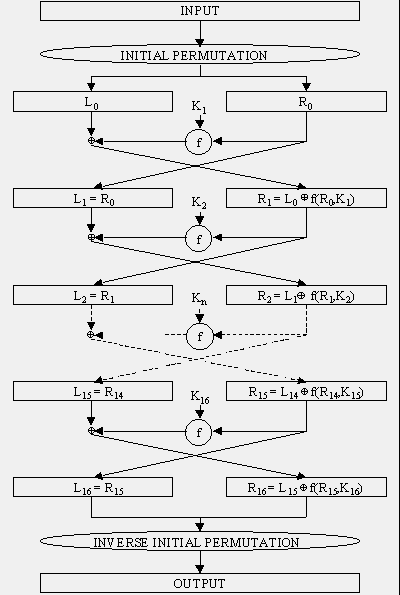
An Overview of Cryptography

An Overview of Cryptography

An Overview of Cryptography
The SSL Store: What Is a TPM in Security? Trusted Platform Modules

An Overview of Cryptography


















