The Hidden Threat to Your SecOps: Tampered Log Data
Por um escritor misterioso
Last updated 26 abril 2025
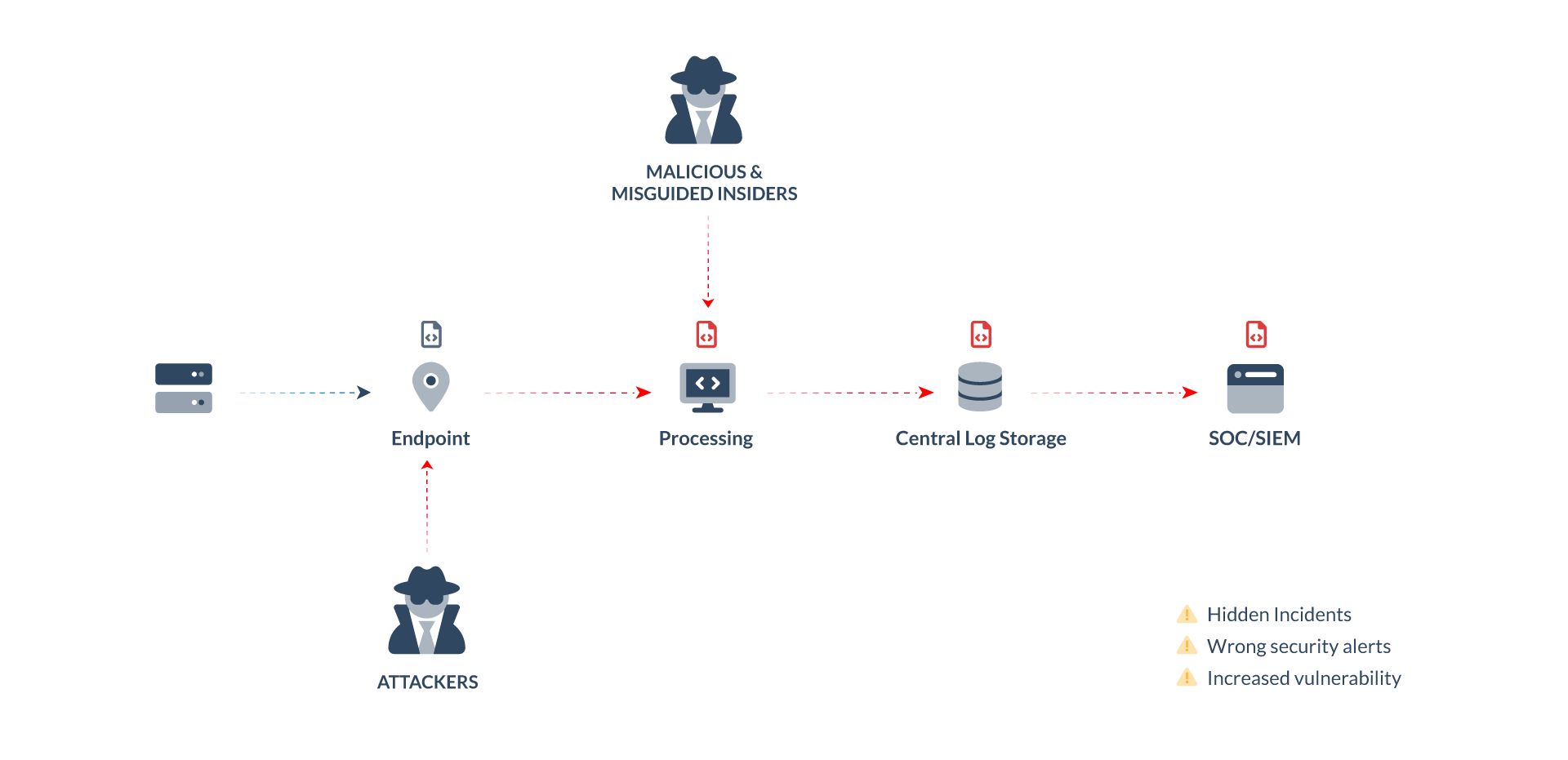
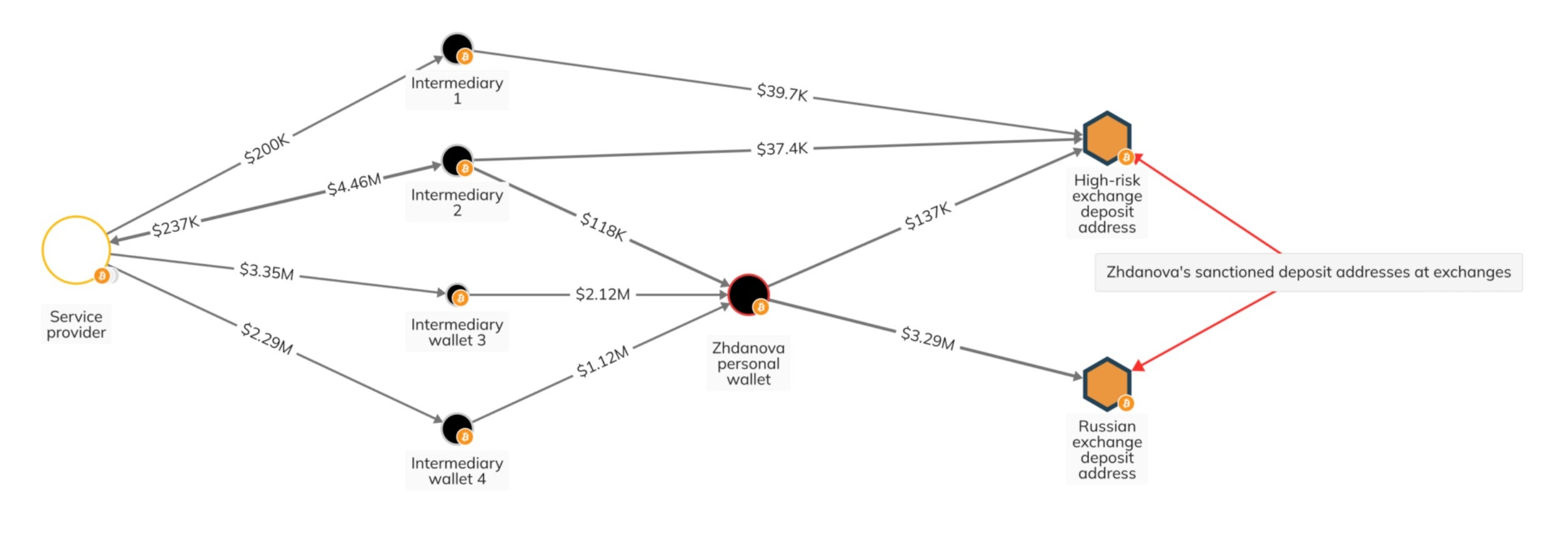
Log data plays a critical role in SecOps by providing insights into systems. This makes log data a popular target for cybercriminals.

Detect – SEC-LABS R&D
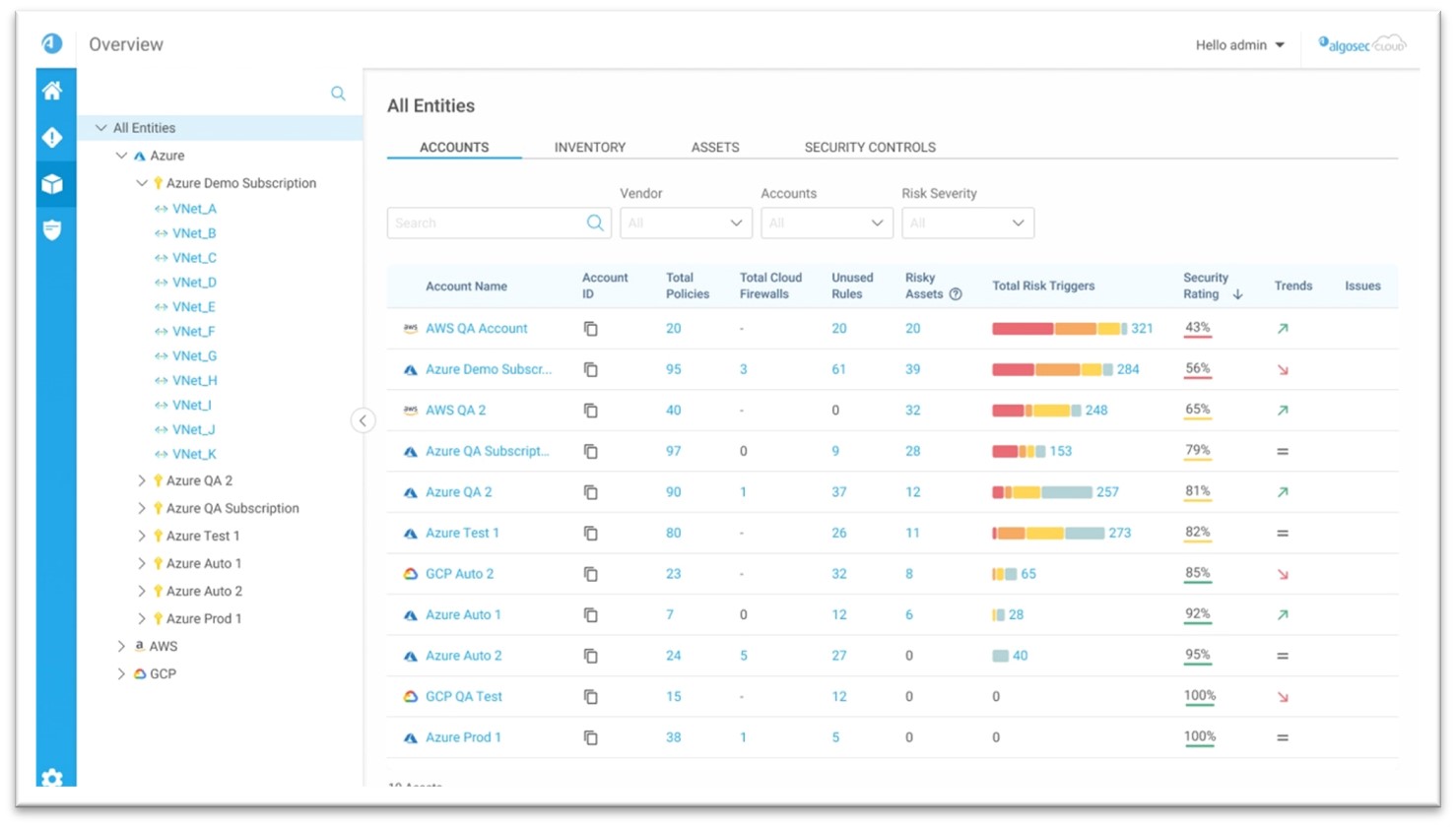
How to keep cyber safe this holiday season - AlgoSec
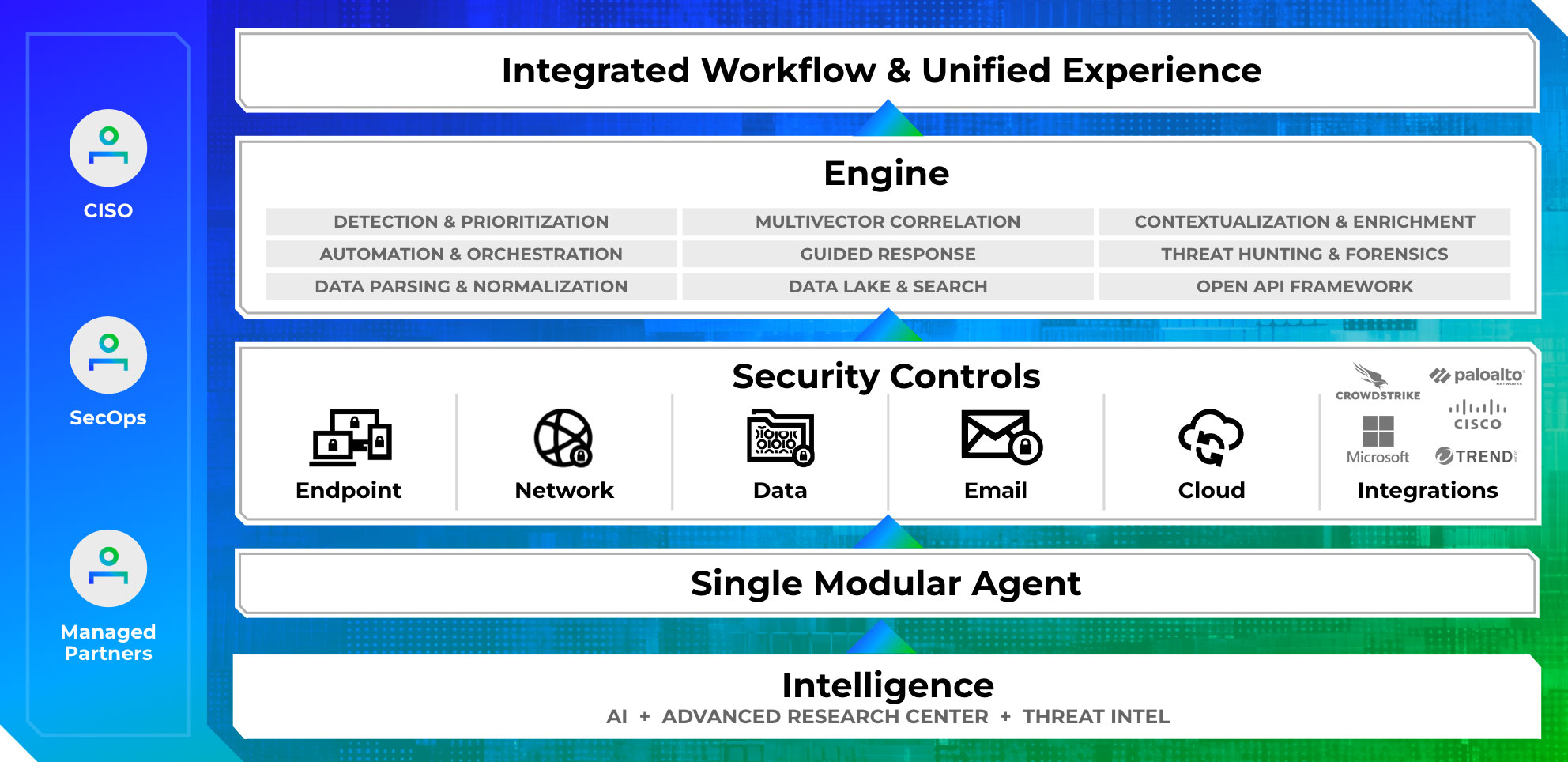
Ransomware Detection and Response

Detect – SEC-LABS R&D

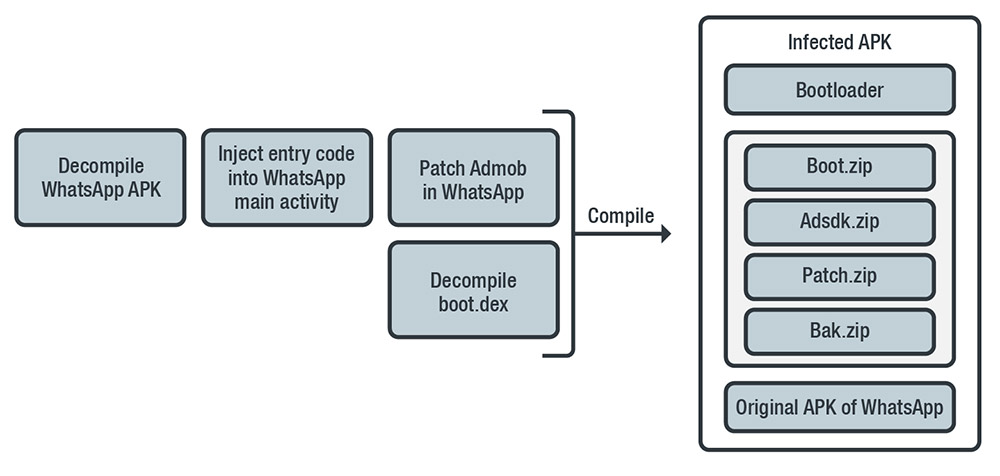
What is Log Tampering? - GeeksforGeeks
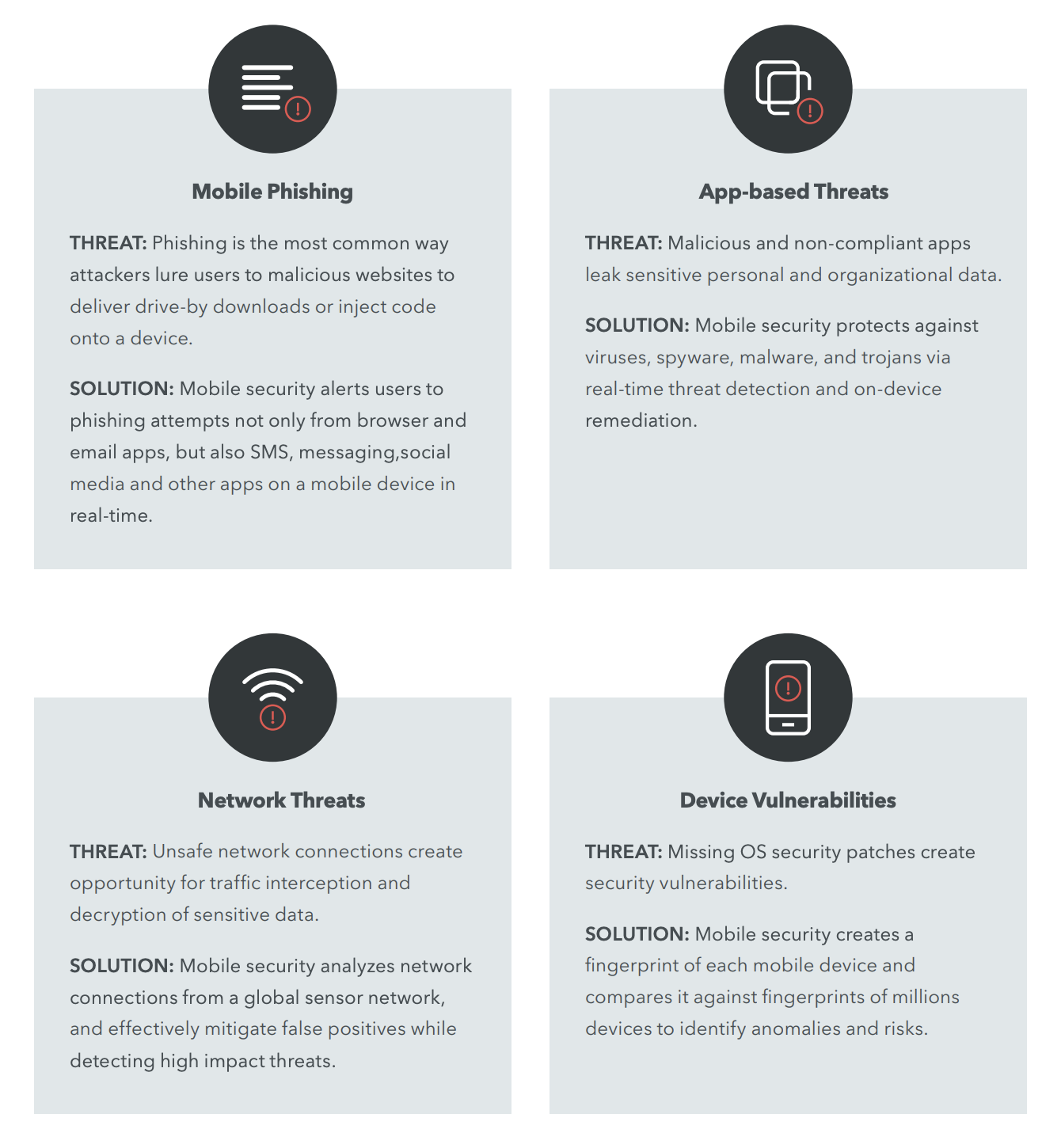
How VMware can Secure Mobile Endpoints with Threat Defense (MTD)

6 Important Best Practices for Preparing for Data Breaches and Security Incidents - Storcom, Lombard, Illinois, United States of America

10 IAM Best Practices for 2023
The Good, the Bad and the Ugly in Cybersecurity - Week 45 - SentinelOne
Review, Refocus, and Recalibrate: The 2019 Mobile Threat Landscape - Security Roundup

CISO Archives - Apex Assembly

Beginners Guide to SAP Security: Why is it Important and How Does it Work?



![FM21] Entering the Mysterious Paths of the 4231 DM Wide - Help Needed - Tactics, Training & Strategies Discussion - Sports Interactive Community](https://content.invisioncic.com/Msigames/monthly_2022_04/image.png.8064ecf731e324279c554984921b1550.png)






/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/R/8/NqkIB9QQekQaVl0Jy89w/2013-08-28-xbox-360-pendrive-usb-storage.jpg)




