TROJ_UPATRE.YYMV - Threat Encyclopedia
Por um escritor misterioso
Last updated 24 fevereiro 2025

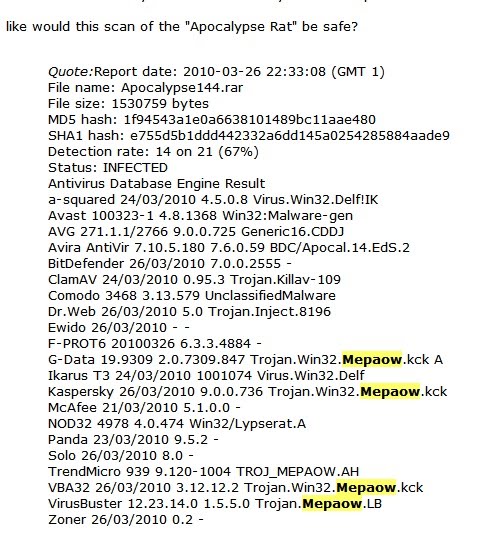
This malware was used in a spam campaign that uses Dropbox as a social engineering lure in order for users to click the related links. To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
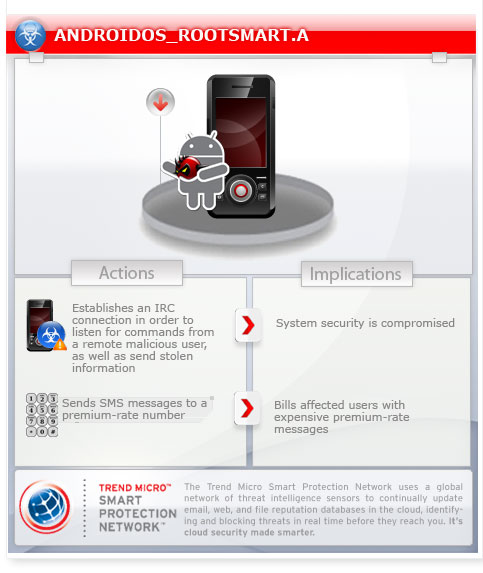
ANDROIDOS_ROOTSMART.A - Threat Encyclopedia

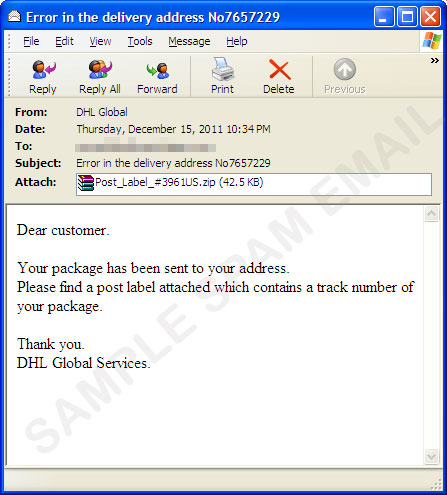
TROJ_UPATRE.YYMV - Threat Encyclopedia
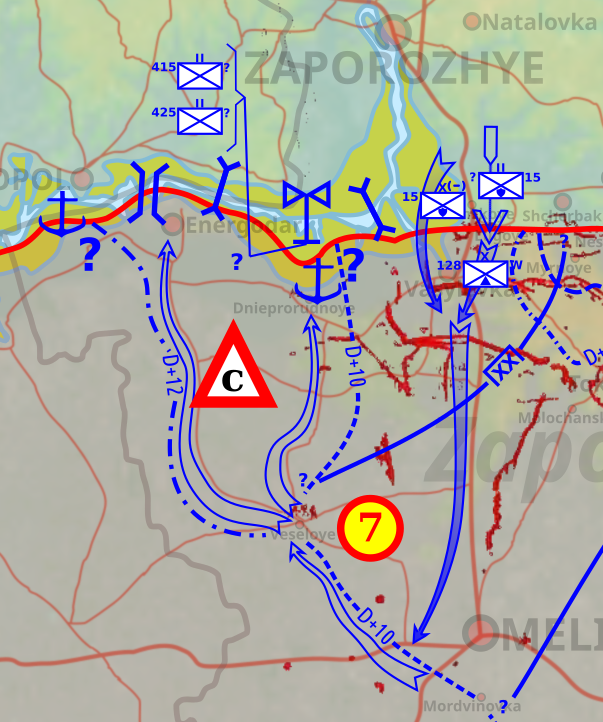
🧵 UKRAINE'S ZAPOROZHYE OFFENSIVE Operations Order (OPORD): 'General Outline of Operations / Commander's Summary' It seems clear the Russian Army h - Thread from Matt Davies @MNormanDavies - Rattibha

Metasploit Meterpreter Malware Detection: New Phishing Cyber-Attack on Ukrainian Government Entities Linked to UAC-0098 and TrickBot Groups - SOC Prime
TROJ_FAKEAV.ESY - Threat Encyclopedia
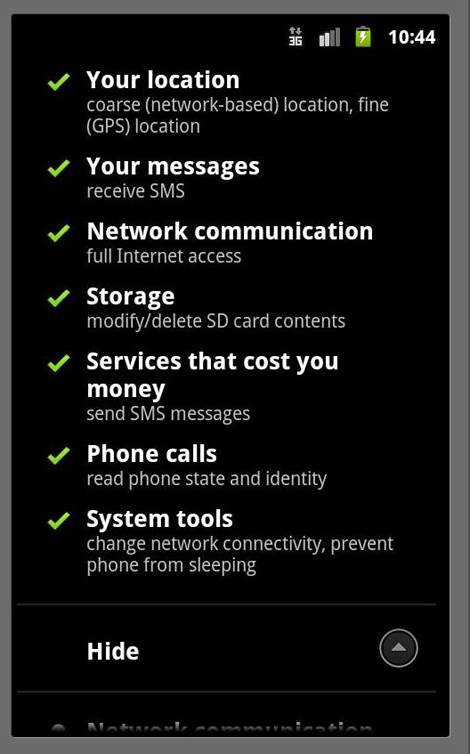
ANDROIDOS_GHOTELS.A - Threat Encyclopedia
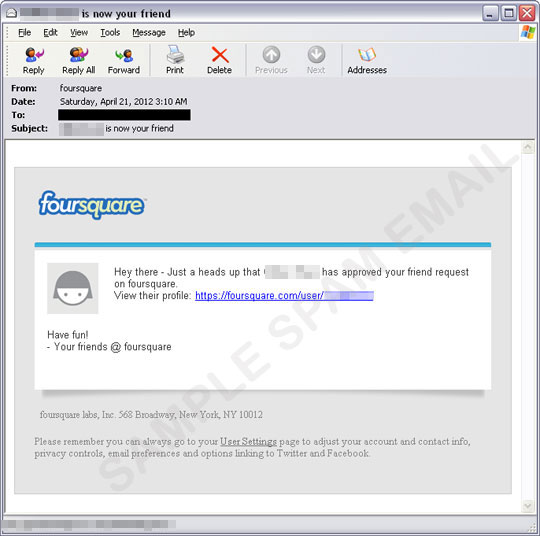
Foursquare Now Used As Lure for Spam Run - Threat Encyclopedia
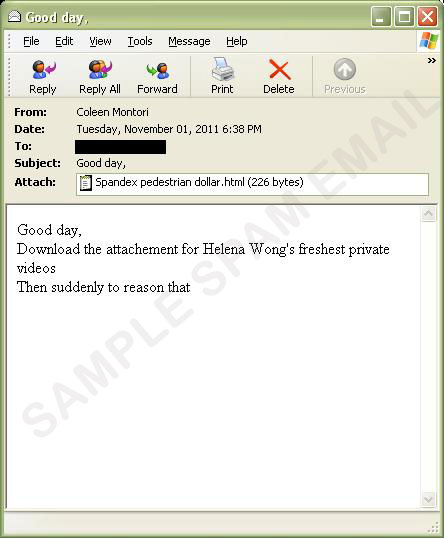
Scammers Use Names of Popular Personalities in Spam - Threat Encyclopedia
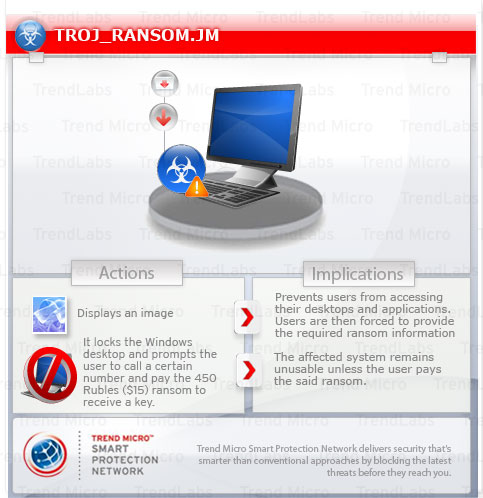
TROJ_RANSOM.JM - Threat Encyclopedia
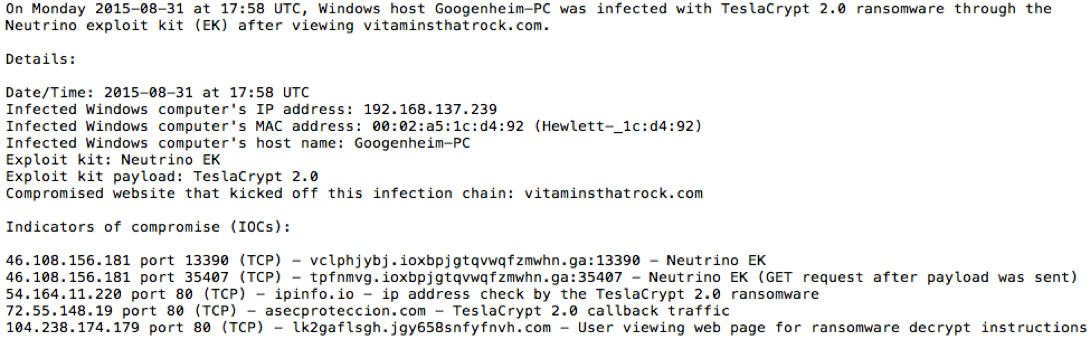
2015-08-31 - Traffic analysis exercise - answers
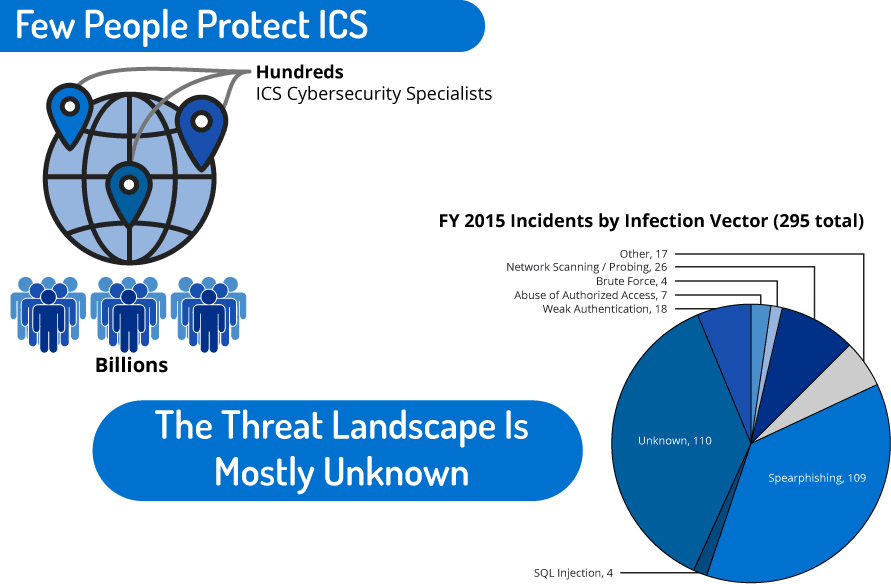
How Dragos Protects Industrial Control Systems With Threat Hunting