Bad Browser Plug-ins Gone Wild: Malvertising, Data Exfiltration
Por um escritor misterioso
Last updated 26 abril 2025

This post was authored by Fred Concklin, William Largent, Martin Rehak, Michal Svoboda, and Veronica Valeros. During an average day of surfing the web via computer, smartphones, and tablets, we
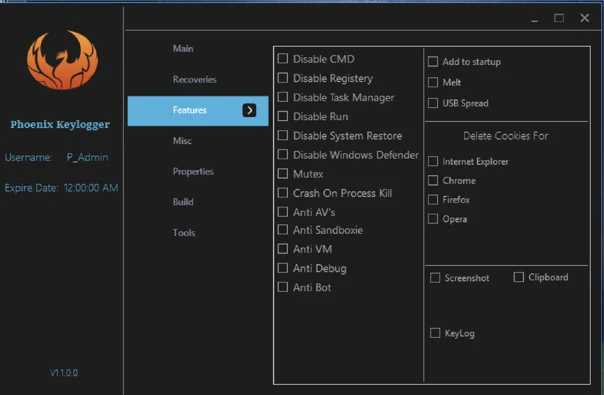
Phoenix: The Tale of the Resurrected Keylogger

Amadey Info-Stealer: Exploiting N-Day Vulnerabilities to Launch Information Stealing Malware
Risky Biz News: Gmail will warn users when their email address appears on the dark web
Bad Browser Plug-ins Gone Wild: Malvertising, Data Exfiltration, and Malware, Oh my! - Cisco Blogs
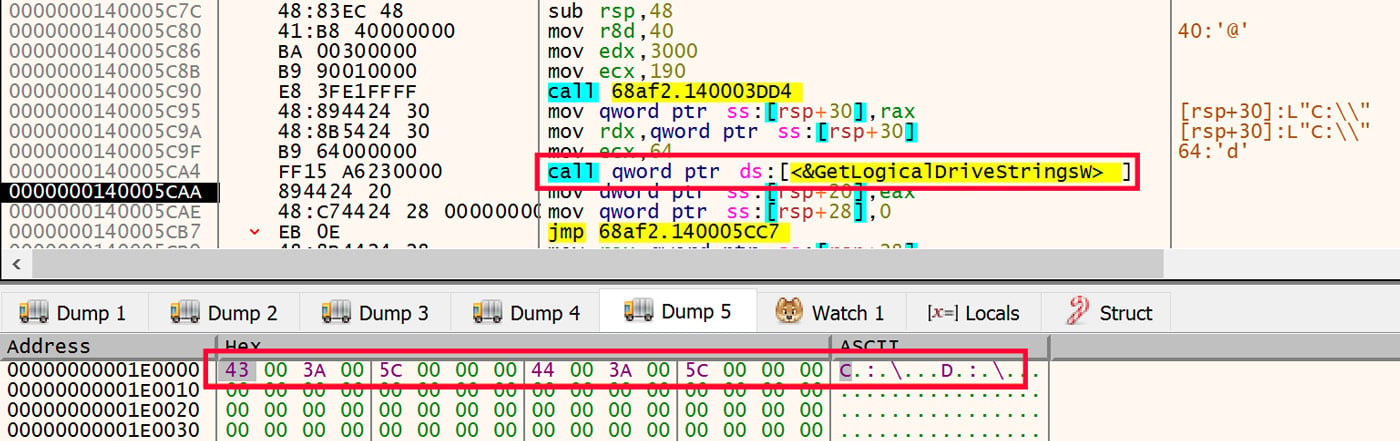
Data Exfiltrator

Bad Browser Plug-ins Gone Wild: Malvertising, Data Exfiltration, and Malware, Oh my! - Cisco Blogs

Bad Browser Plug-ins Gone Wild: Malvertising, Data Exfiltration, and Malware, Oh my! - Cisco Blogs

Google Chrome Under Active Attack, Exploiting New Vulnerability - Vina Aspire

LLM meets Malware: Starting the Era of Autonomous Threat
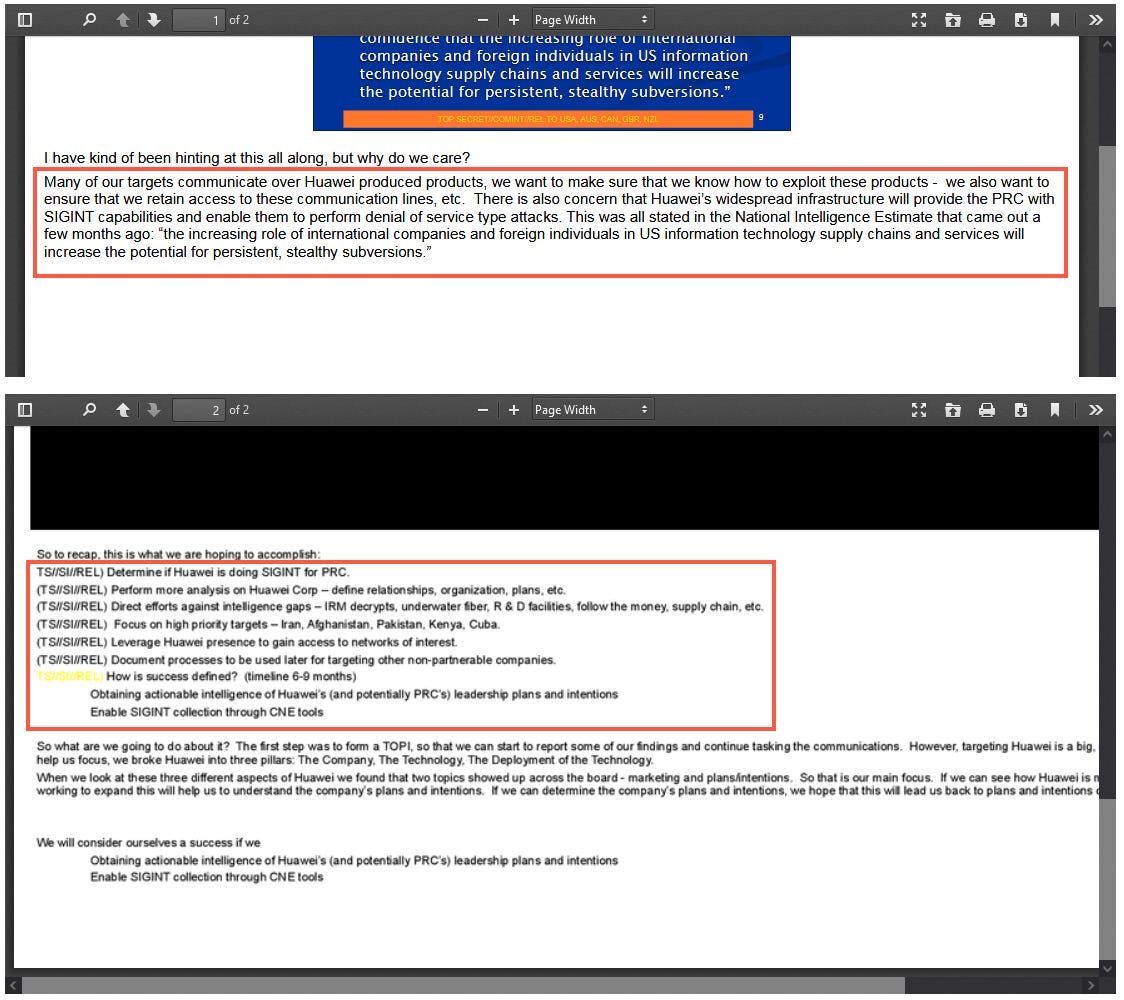
Risky Biz News: China admits NSA hacked Huawei
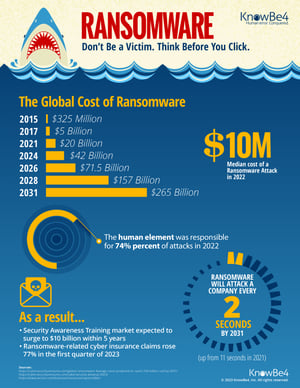
What is Ransomware?

Everything you need to know about the LummaC2 stealer: leveraging IDA Python and Unicorn to deobfuscate Windows API hashing - Outpost24

I2CE3: A dedicated and separated attack chain for ransomware offenses as the most infamous cyber extortion - ScienceDirect
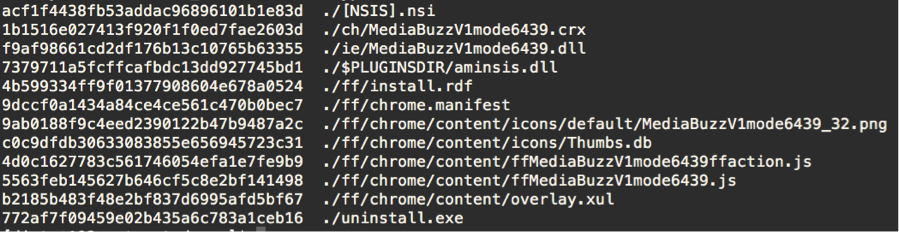
Bad Browser Plug-ins Gone Wild: Malvertising, Data Exfiltration, and Malware, Oh my! - Cisco Blogs
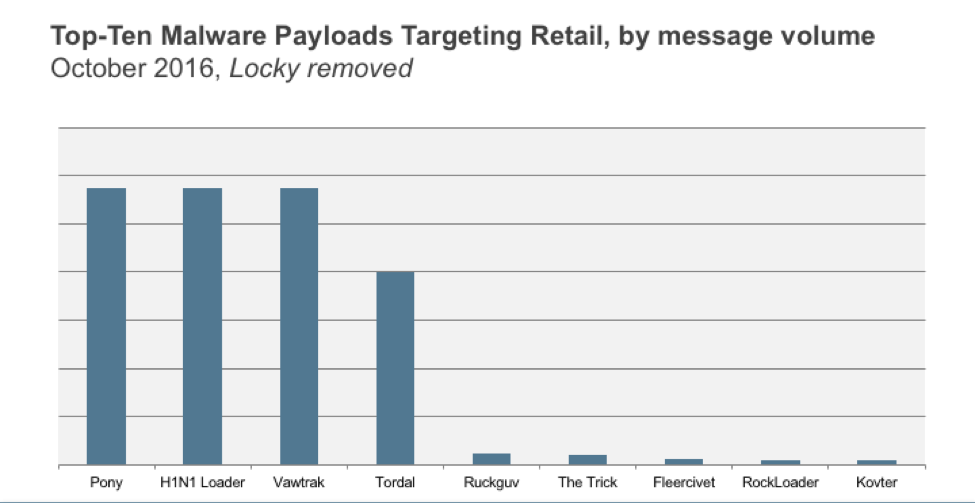
ZeusPOS and NewPOSthings Point-of-Sale Malware Traffic Quadruples For Black Friday







![DoomSpire Modded [Walk on Walls!] - Roblox](https://tr.rbxcdn.com/ba4042e06dd4d5ef6e974fb2fa3dd3d7/768/432/Image/Png)


/cdn.vox-cdn.com/uploads/chorus_image/image/59928033/SPAdore20Years_Getty_Ringer.0.jpg)