Malware analysis Malicious activity
Por um escritor misterioso
Last updated 24 fevereiro 2025
Malware analysis lockysample.bin.zip Malicious activity

StopRansomware: Rhysida Ransomware
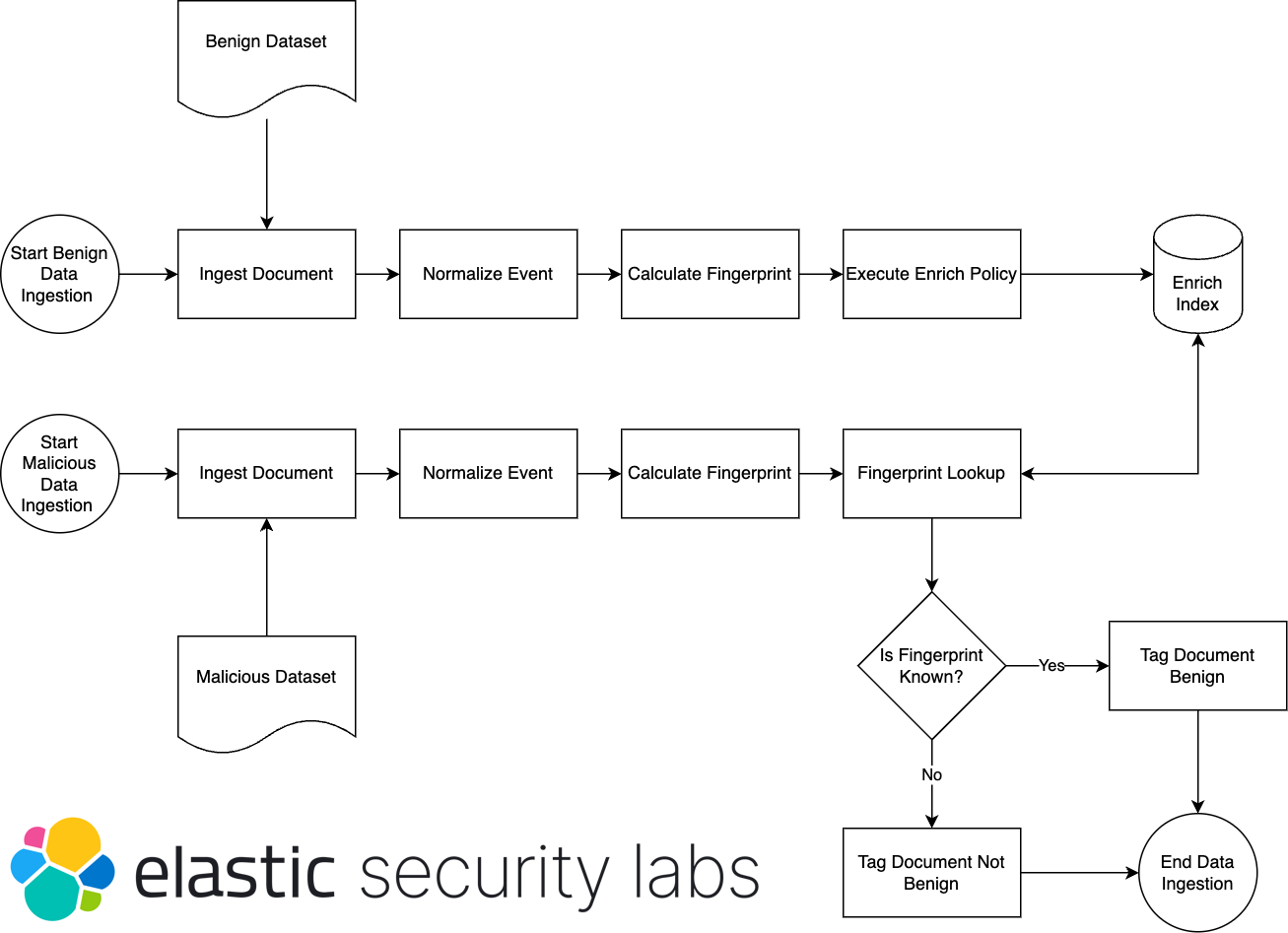
An Elastic approach to large-scale dynamic malware analysis — Elastic Security Labs
Malicious URL Scanner, Scan URLs for Malware
Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware: 9781788392501: A,

Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware

ReversingLabs Malware Lab: Detect, classify, analyze, and respond to malicious files - Help Net Security
Malware analysis Pixelus Deluxe.zip Malicious activity

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

Playbook of the Week: Malware Investigation and Response - Palo Alto Networks Blog