Malware analysis Malicious activity
Por um escritor misterioso
Last updated 24 fevereiro 2025

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis: Protecting Your Network from Cyber Attacks

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

The Guide to Ransomware Solutions in 2023 - Security Boulevard
Malware analysis index.html Malicious activity

AlienVault - Open Threat Exchange

Overview

Cybersecurity Search Engine
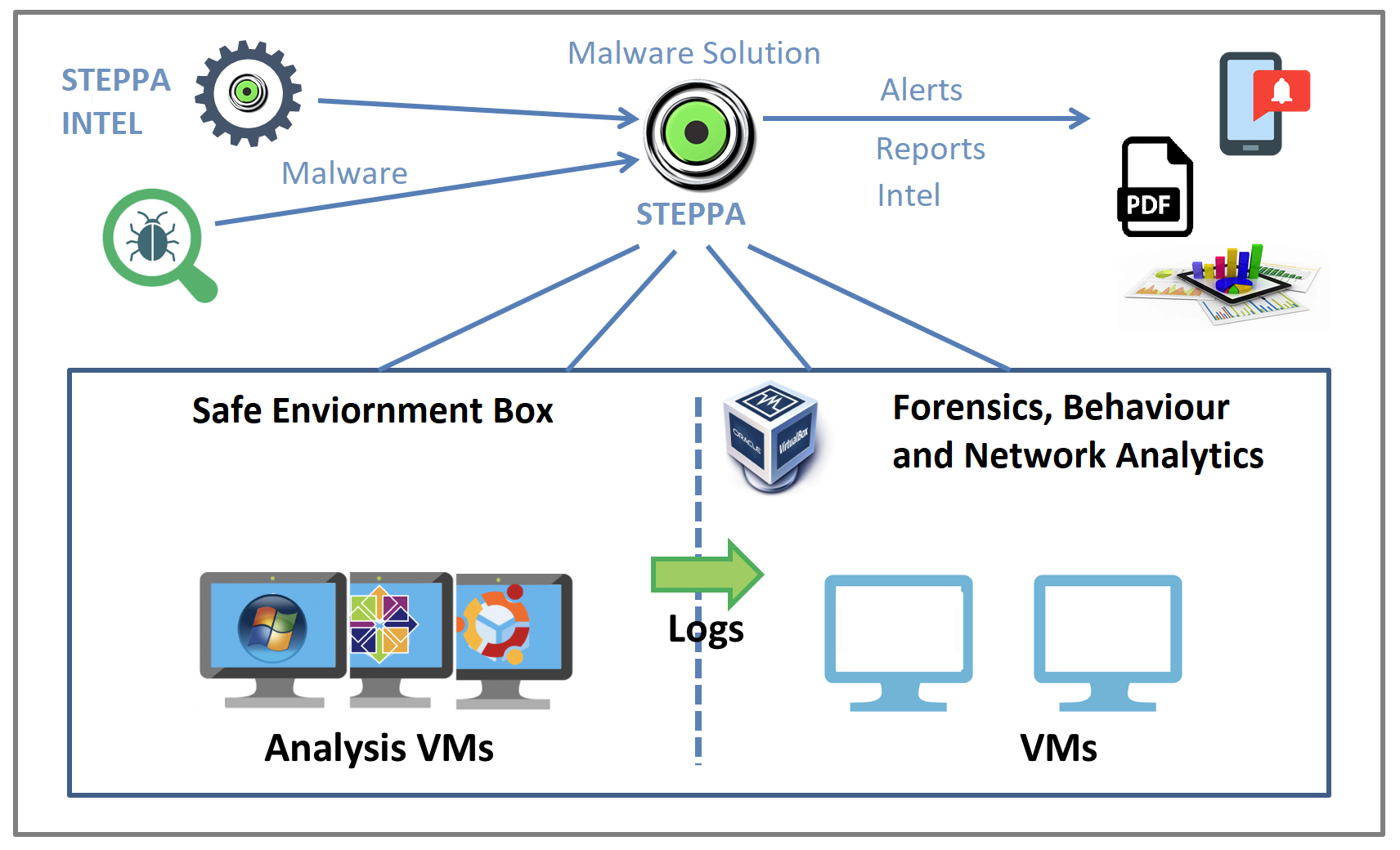
Malware Analysis Solution: Analyze, Detect, and Protect

Malware Analysis: Steps & Examples - CrowdStrike
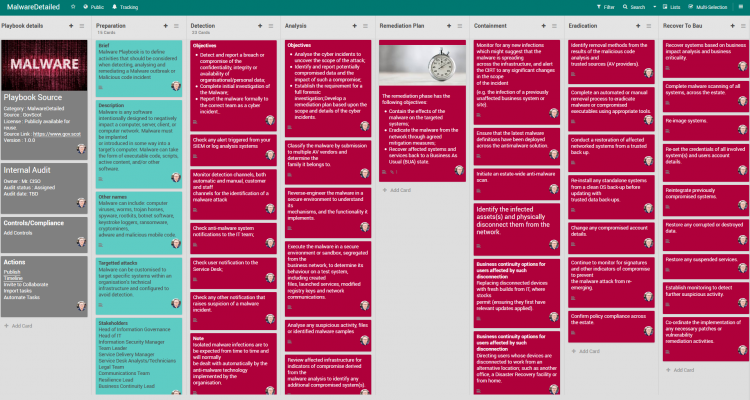
Playbook for Malware outbreak

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Malware Analysis: Steps & Examples - CrowdStrike
TryHackMe Hacktivities

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus