Malware analysis Malicious activity
Por um escritor misterioso
Last updated 24 fevereiro 2025

Malware Analysis: Steps & Examples - CrowdStrike

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Malware Analysis: Protecting Your Network from Cyber Attacks

Malware analysis index.html Malicious activity
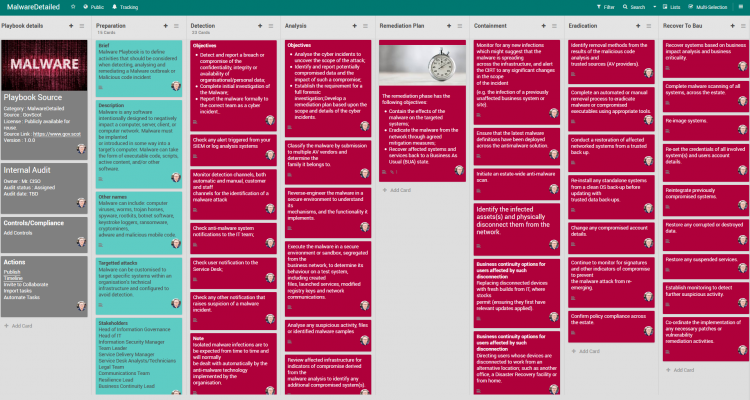
Playbook for Malware outbreak

Mastering Malware Analysis
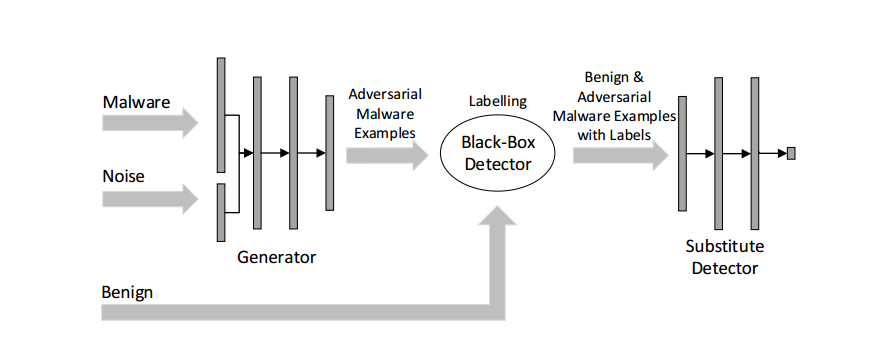
Malware Detection

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable

StopRansomware: Rhysida Ransomware

10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac

Cybersecurity Search Engine

Brute Force Attacks: Password Protection
Interactive Online Malware Sandbox

![Bonzi Buddy Donkey Kong [Super Smash Bros. (Wii U)] [Mods]](https://images.gamebanana.com/img/ss/mods/576fa9cbc90f3.jpg)




![Detail] Creeper Wall Face : r/Minecraft](http://i.imgur.com/mrUcs.png)