Malware analysis Malicious
Por um escritor misterioso
Last updated 24 fevereiro 2025

10 Best Malware Analysis Tools - Updated 2023! (Paid & Free)

Malware Analysis 101: Techniques & Tools, by Luis Soares
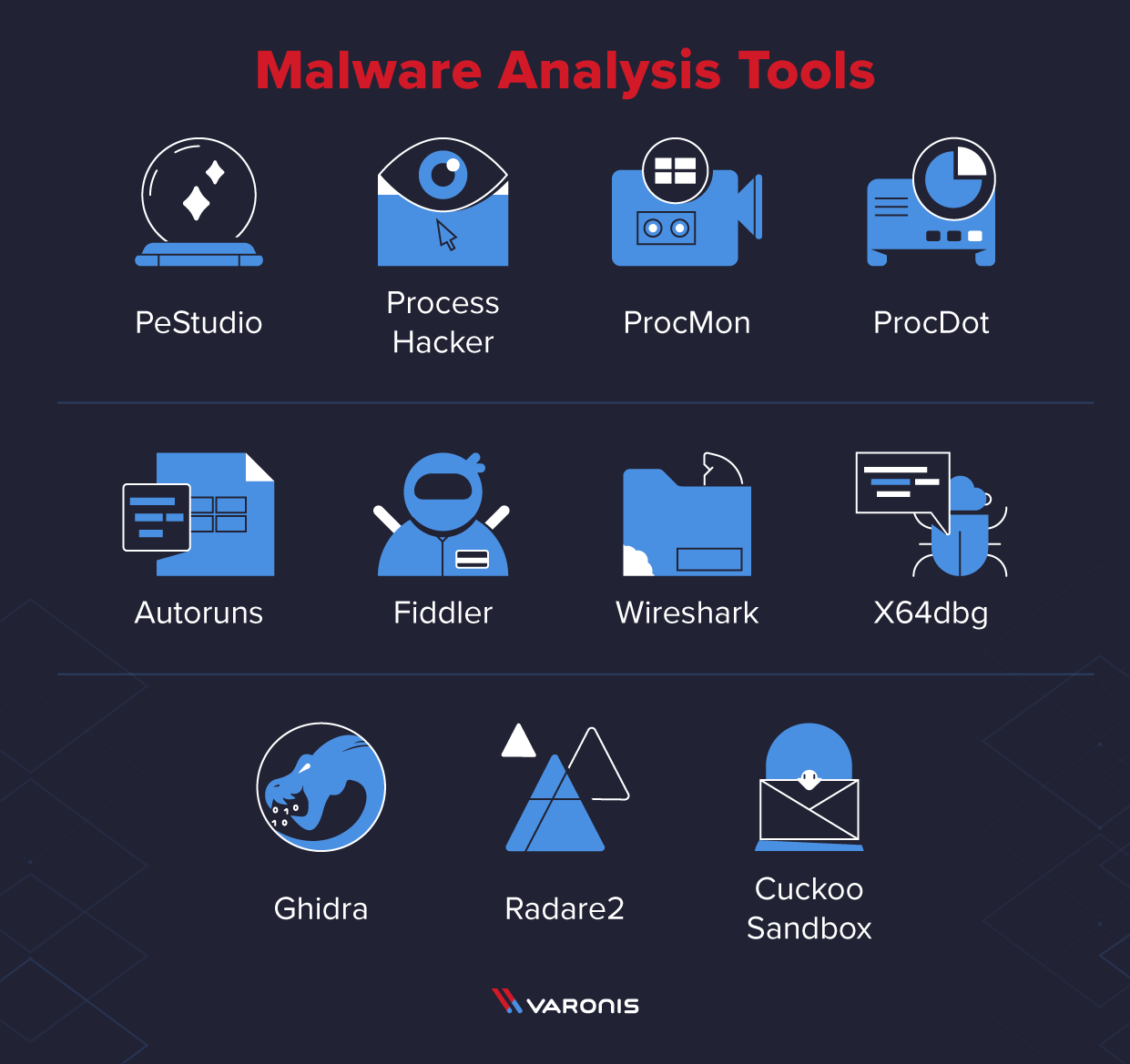
11 Best Malware Analysis Tools and Their Features
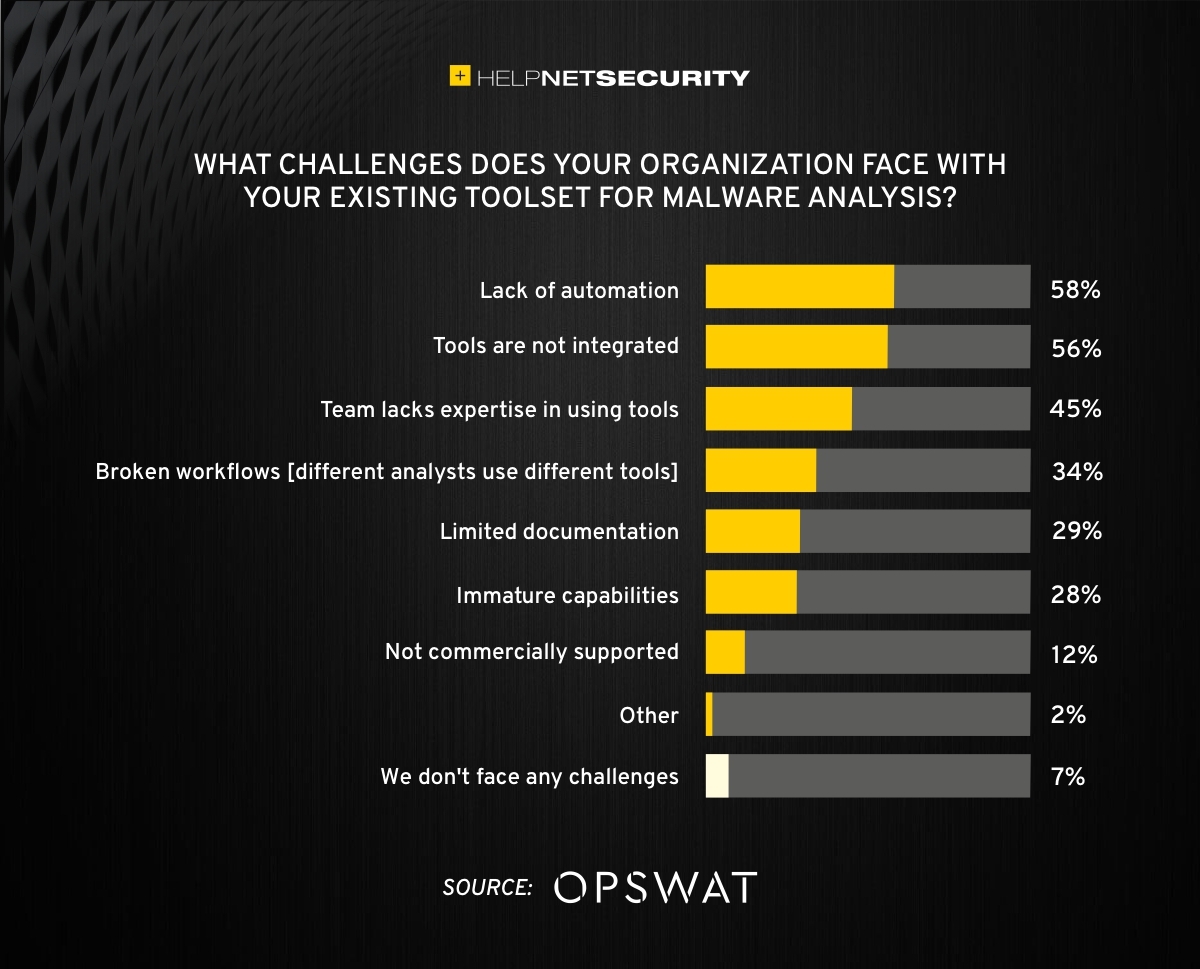
What is challenging malware analysis? - Help Net Security

Security Orchestration Use Case: Automating Malware Analysis

Dynamic malware analysis [34]

Intro to Malware Analysis: What It Is & How It Works - InfoSec

Intro to Malware Analysis: What It Is & How It Works - InfoSec
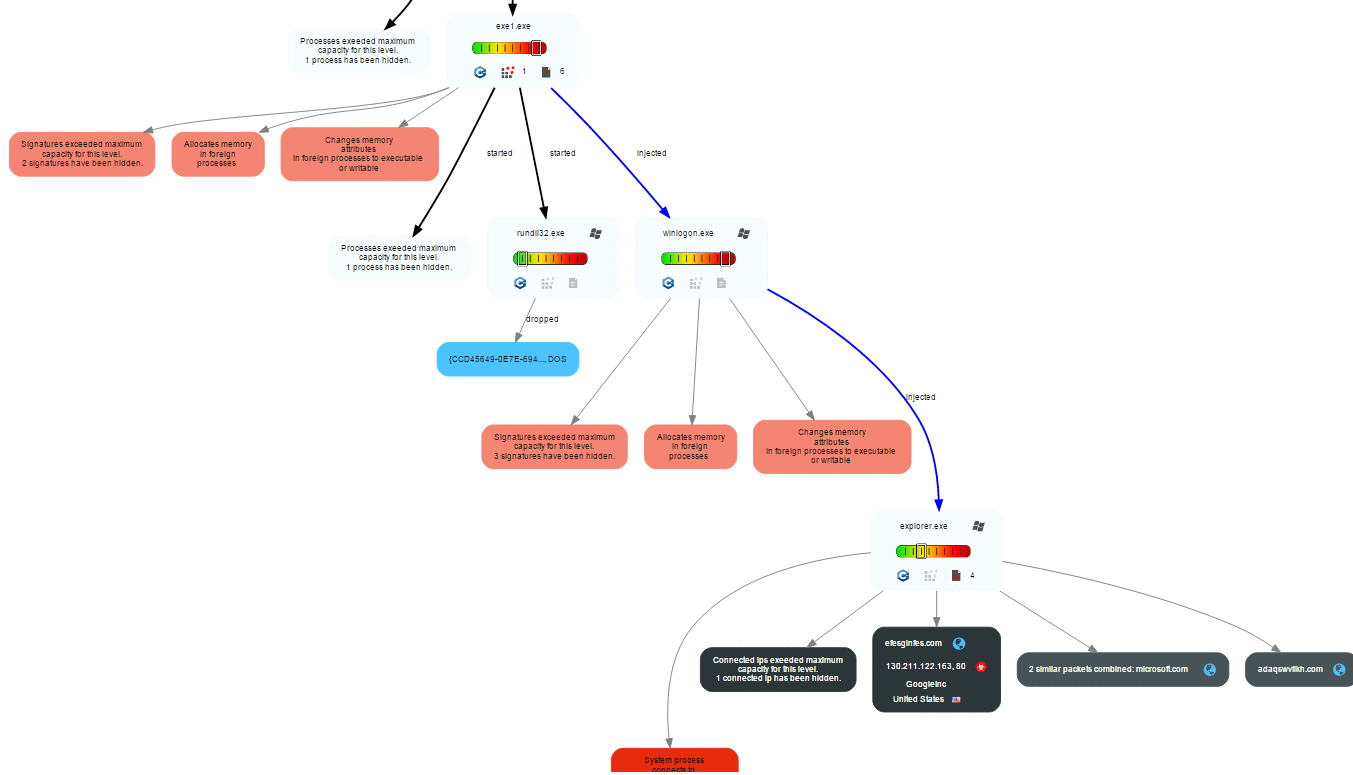
Deep Malware Analysis - Behavior Graph 2.0

What is Malware Analysis? Benefits, Types, and Tools

Practical Malware Analysis : The Hands-On Guide to Dissecting
Top static malware analysis techniques for beginners

What is Malware Analysis? Types and Stages of Malware Analysis
Practical Malware Analysis : The Hands-On Guide to Dissecting Malicious Software By Michael Sikorsky and Andrew Honig Like new condition ISBN

Practical Malware Analysis : The Hands-On Guide to Dissecting Malicious Softw

PDF] A Survey on Malware Detection and Analysis Tools