Malware analysis
Por um escritor misterioso
Last updated 24 fevereiro 2025

Advanced Malware Analysis Platform
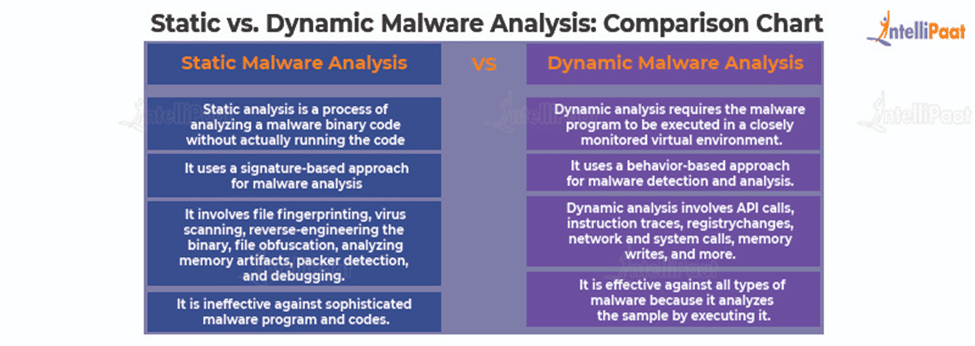
Malware Analysis - What is, Benefits & Types (Easily Explained)

Malware Analysis Fundamentals

Malware Analysis: SharkBot

The different types of Malware Analysis, by Dunst Consulting

CosmicDuke Malware Analysis - CYFIRMA

Malware Analyst – Job Description and How to Become - Security Boulevard

Malware Detection Using Machine Learning Techniques

TryHackMe Malware Analysis

Malware Analysis: Tips, Tools, and Techniques
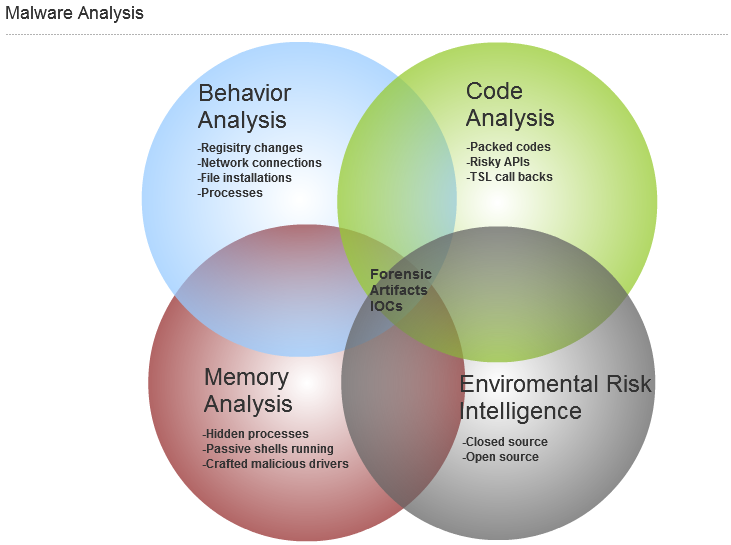
SANS Digital Forensics and Incident Response Blog, Four Focus Areas of Malware Analysis









/cdn.vox-cdn.com/uploads/chorus_image/image/63699754/screen-shot-2014-02-08-at-12-37-45-pm.0.1467738969.0.png)