Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Last updated 26 abril 2025

This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this

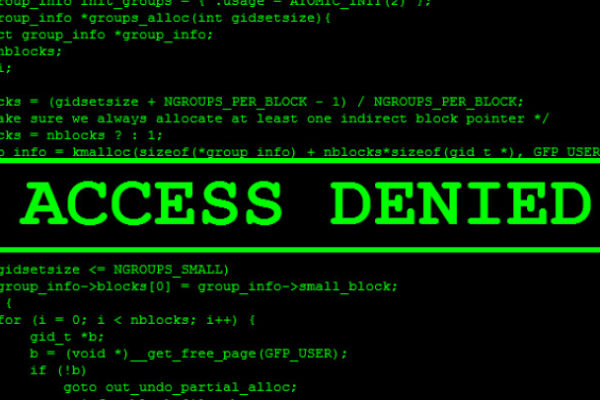
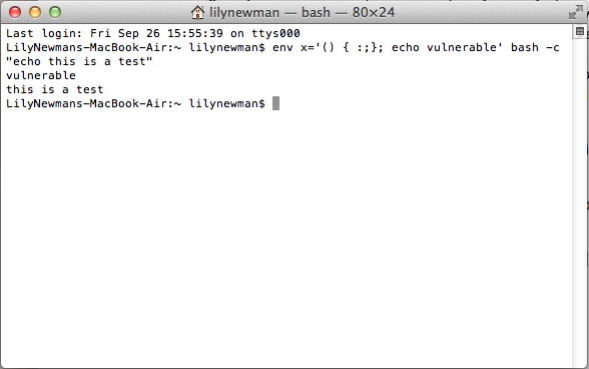
Linux Exploitation – Shellshock exploit and privilege escalation

TryHackMe Advent of Cyber 2 [2020]

Exploiting Blind SSRF - Passion

Blind SSRF Attack with Shellshock Exploitation [Research Paper]

ABHISHEK KUMAR SINGH on LinkedIn: Lab17: Blind SQL injection with

Server-Side Request Forgery (SSRF) - Intigriti
Solving PortSwigger SSRF Labs - Final Part - ::: re:search + re

SSRF(服务器跨站请求伪造)基础知识- lca

翻译]盲SSRF利用链术语表-腾讯云开发者社区-腾讯云