Group Behind Cisco Device Hijackings Changes Tactics to Evade
Por um escritor misterioso
Last updated 24 fevereiro 2025

Evidence is emerging that the hacking group has updated its techniques to better conceal which Cisco devices have been hijacked.

Bad password policies and how to avoid them

The many vulnerabilities Talos discovered in SOHO and industrial wireless routers post-VPNFilter

Validated Solution: Wireless Automation Deployment Using Cisco DNA Center - Cisco

CyberWatch - June 21, 2023
Cisco Catalyst 9800 Series Configuration Best Practices - Cisco

How a hacking group hijacks Cisco devices., James G. posted on the topic

How supply chain attacks work and 7 ways to mitigate them

Critical Flaw Leads Hackers to Hijack Thousands of Cisco Devices

Cisco Talos Says a Nation State Is Behind Sea Turtle DNS Hijacking Attacks

Red & Blue Team
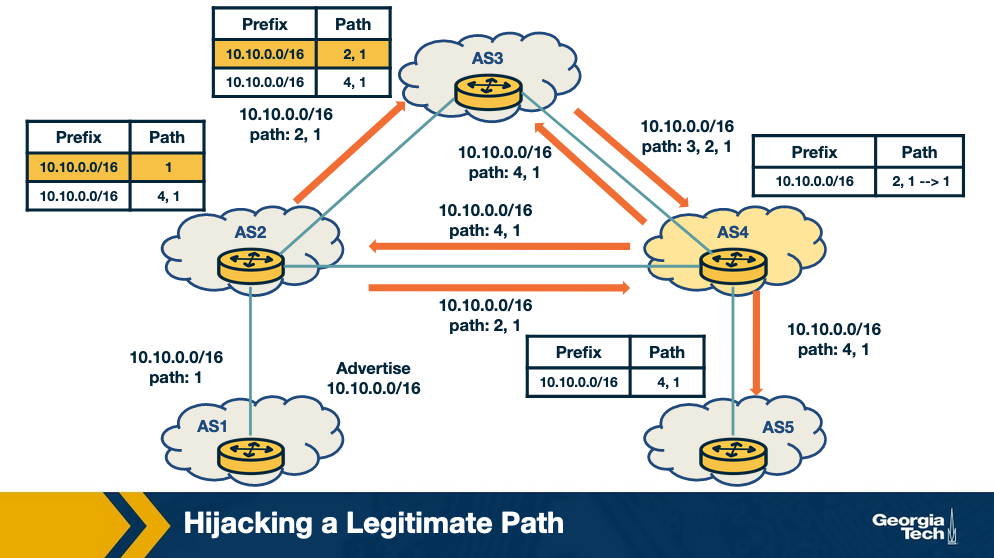
Internet Security - OMSCS Notes

BlueCharlie changes attack infrastructure in response to reports on its activity

Threat Source newsletter (Jan. 7, 2021)

APT groups target journalists and media organizations since 2021