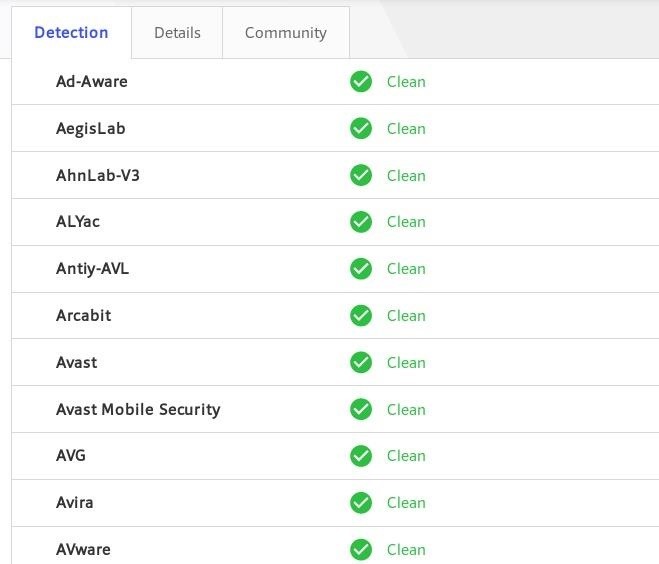
Hackers Using New Obfuscation Mechanisms to Evade Detection
Por um escritor misterioso
Last updated 25 abril 2025
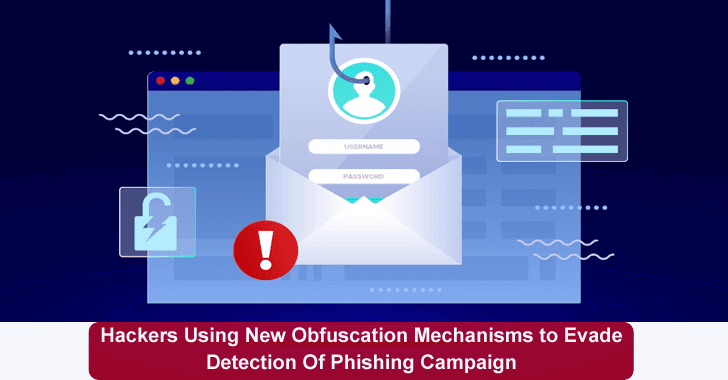
Recently, Microsoft has unveiled details of a deceptive social engineering campaign, in which the operators proceeded to change their obfuscation

How To Utilize AI As A Key Defense Mechanism In Cybersecurity

Locky Ransomware Actors Turning To XORed JavaScript
Hackers Using New Obfuscation Mechanisms to Evade Detection
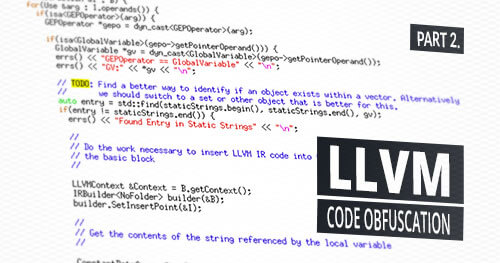
Extending LLVM for Code Obfuscation (2 of 2)

New JSSLoader Trojan Delivered Through XLL Files

Researchers Uncover Packer Used by Several Malware to Evade

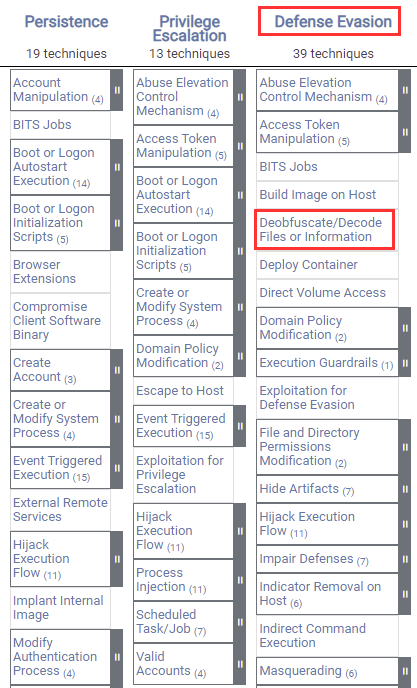
Code Obfuscation: A Comprehensive Guide Against Reverse

This Obfuscation Tool Can Evade Most Security Software: Report
Layered obfuscation: a taxonomy of software obfuscation techniques

Hackers Turn to OpenDocument Format to Avoid AV Detection

Code obfuscation - Cybersecurity ASEE

US, Japanese agencies issue cybersecurity advisory on BlackTech

BGP Hijacking: How Hackers Circumvent Internet Routing Security

How Hackers Use Binary Padding to Outsmart Sandboxes

Building coping mechanisms to deal with ransomware attacks across