Hackers Target Gamers With Microsoft-Signed Rootkit
Por um escritor misterioso
Last updated 26 abril 2025

Kernel mode driver can download second-stage payload directly to memory, allowing threat actors to evade endpoint detection and response tools.

Netfilter Rootkit Malware Targets the Gaming Community: Microsoft

Microsoft Signed Rootkit Malware That Spreads Through Gaming

Gamer Cheater Hacker Spy
Chinese hacking group uses new 'Fire Chili' Windows rootkit

Cuba ransomware group used Microsoft developer accounts to sign

How to detect & prevent rootkits
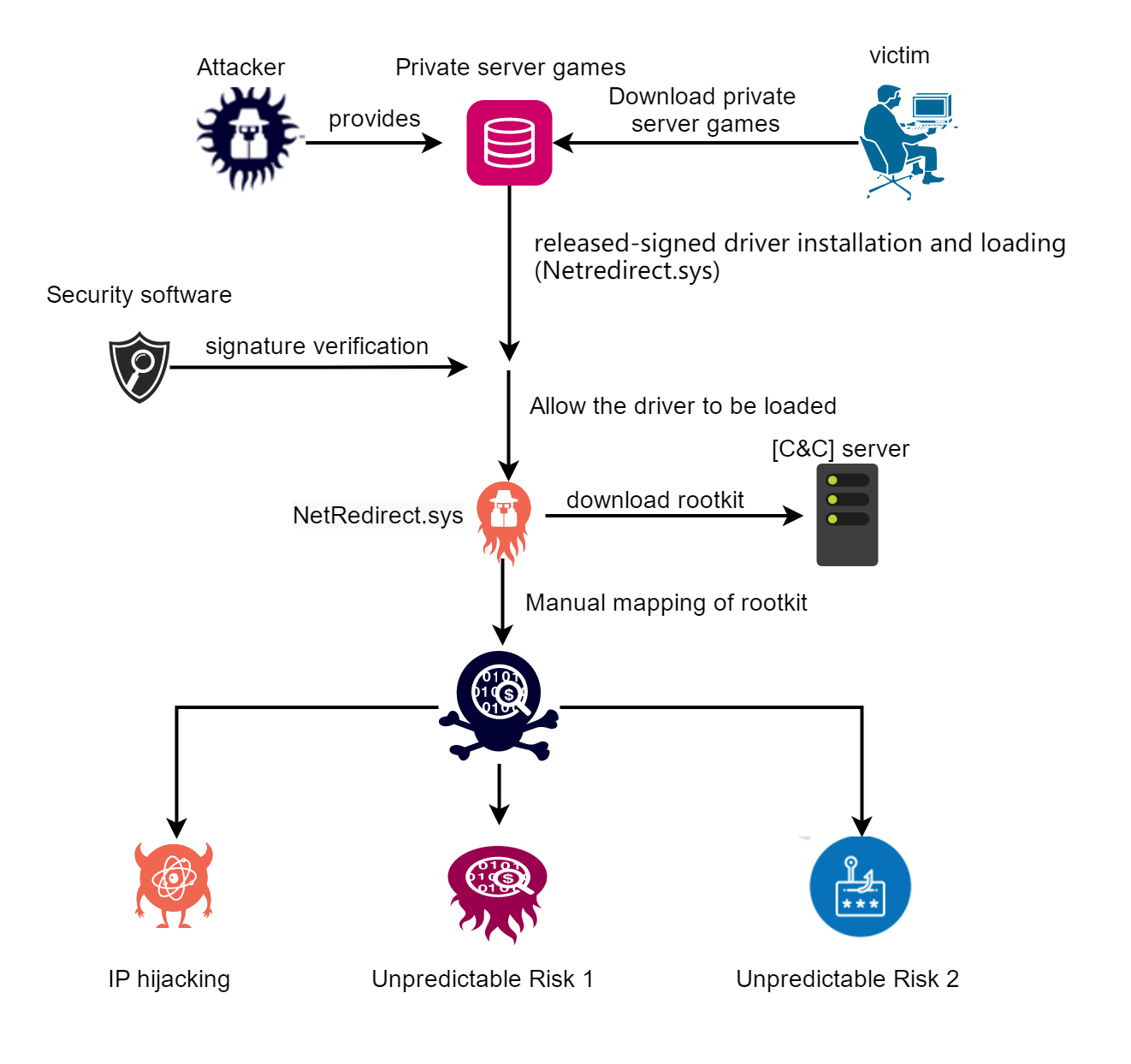
netfilter-rootkit-ii-continues-to-hold-whql-signatures

Researchers Discover Microsoft-Signed FiveSys Rootkit in the Wild

Hackers Deploy Microsoft Digital Signature in Rootkit Attack

Netfilter Rootkit Malware Targets the Gaming Community: Microsoft

What is a Rootkit and How to Detect It? - Shiksha Online

Chinese hacking group uses new 'Fire Chili' Windows rootkit

Cisco Talos Reports Windows Policy Loophole Exploited by Threat Actor

Hackers Target Gamers With Microsoft-Signed Rootkit







:quality(70)/cloudfront-eu-central-1.images.arcpublishing.com/irishtimes/PXUOVU2WNZN2DTHRE7BHHBPYXU.jpg)











