IoT Botnets: Advanced Evasion Tactics and Analysis – Part 2
Por um escritor misterioso
Last updated 24 fevereiro 2025

Nozomi Networks Labs analyzes new modification techniques malware authors use to evade detection and analysis tools.

ACM: Digital Library: Communications of the ACM
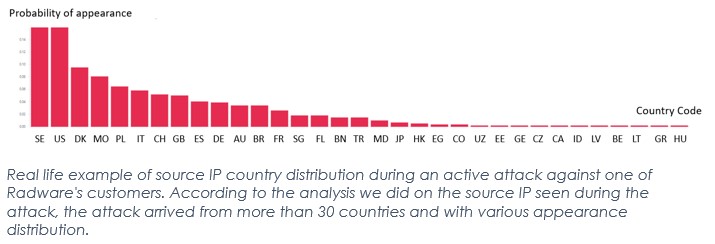
4 Ways To Categorize Web DDoS Tsunami Attacks — Part 2 – Radware Blog

February 2020's Most Wanted Malware: Increase in Exploits Spreading the Mirai Botnet to IoT Devices - Check Point Blog
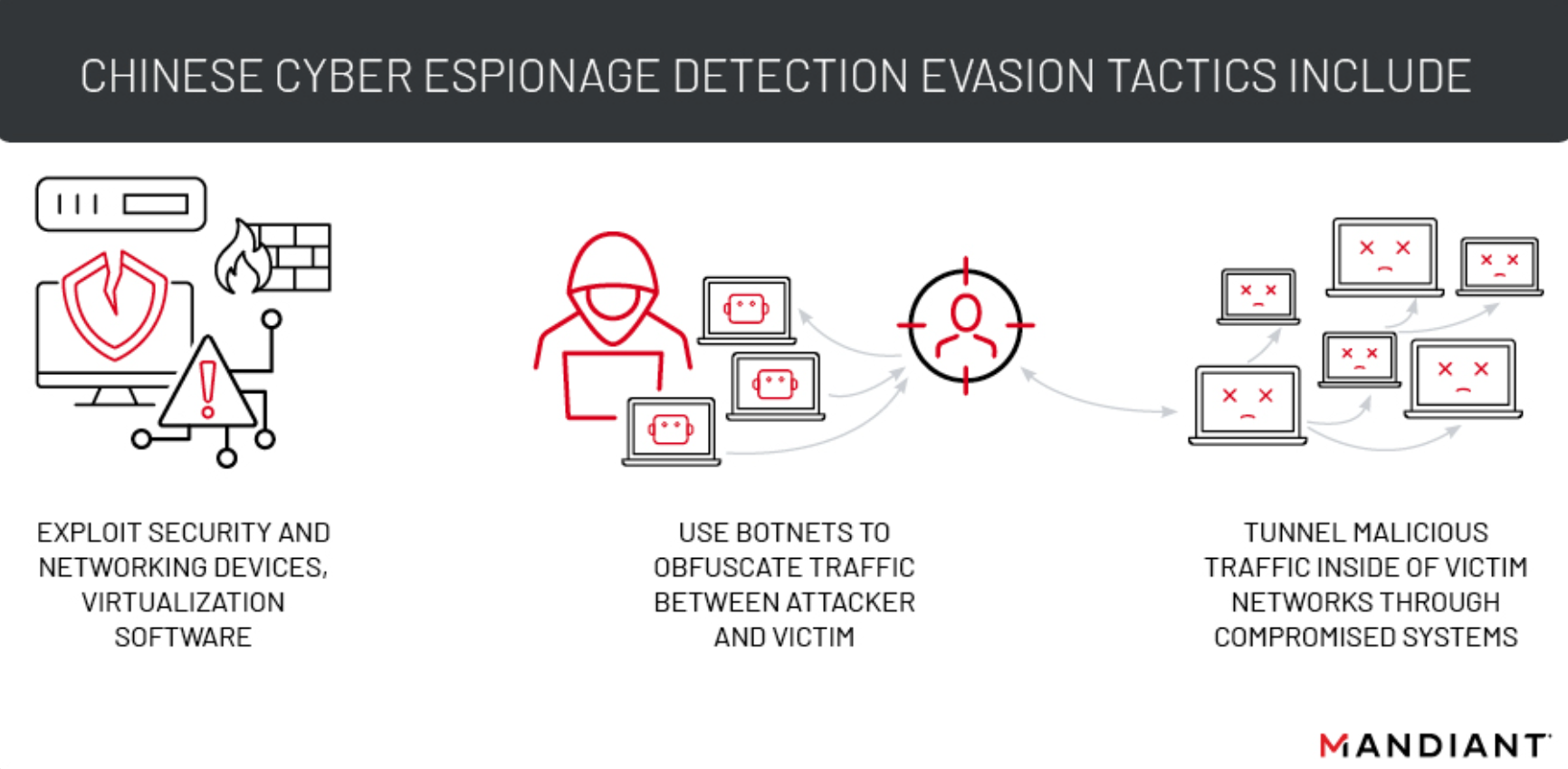
Stealth Mode: Chinese Cyber Espionage Actors Continue to Evolve Tactics to Avoid Detection

DDoS 2.0: IoT Sparks New DDoS Alert
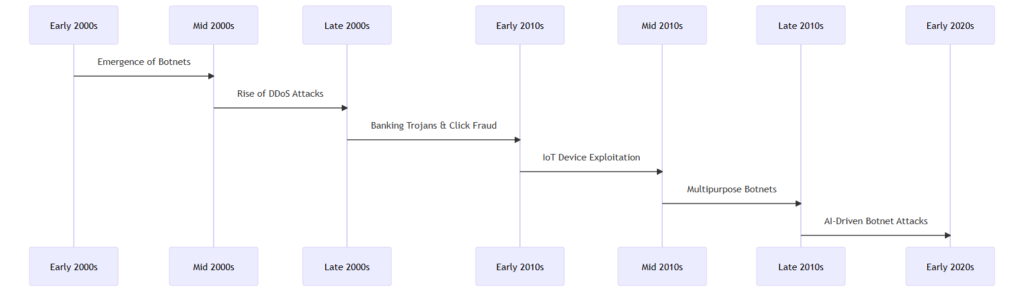
Botnet Detection in 2023: What You're Missing Out On! - Security Boulevard
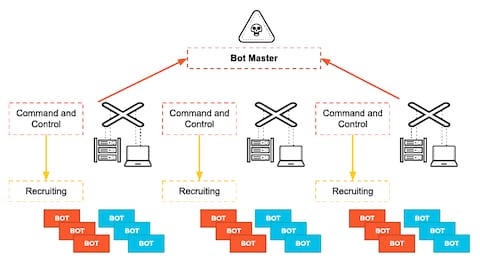
What is a Command and Control Attack? - Palo Alto Networks

IoT Botnets: Advanced Evasion Tactics and Analysis – Part 2
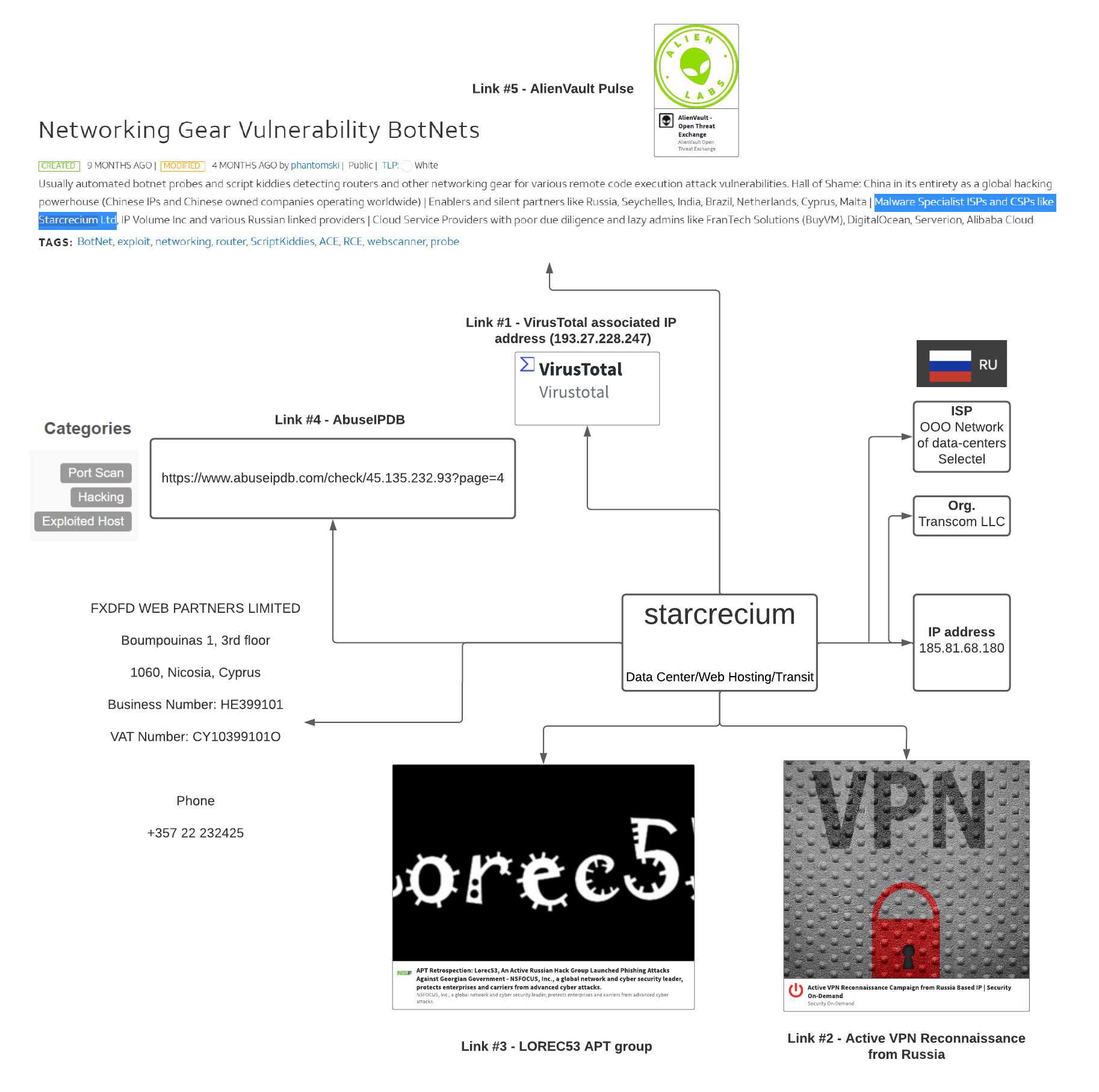
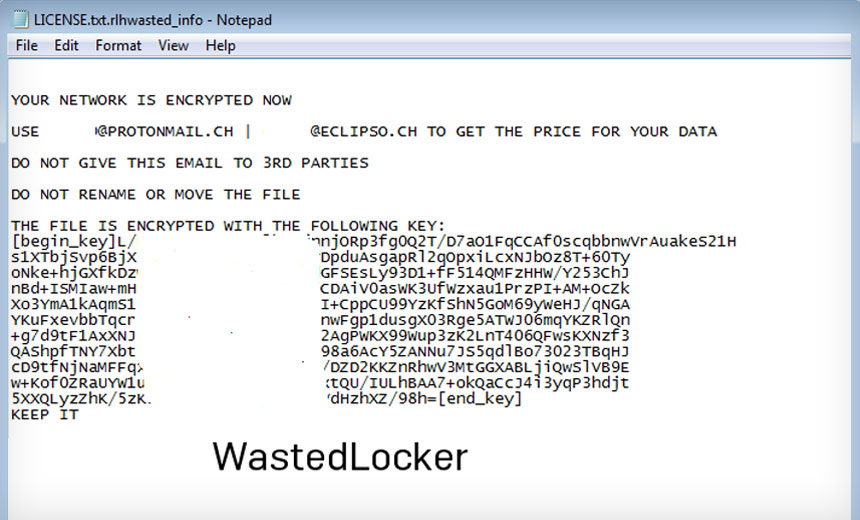
THREAT ANALYSIS REPORT: LockBit 2.0 - All Paths Lead to Ransom

IoT Botnets: Advanced Evasion Tactics and Analysis – Part 2
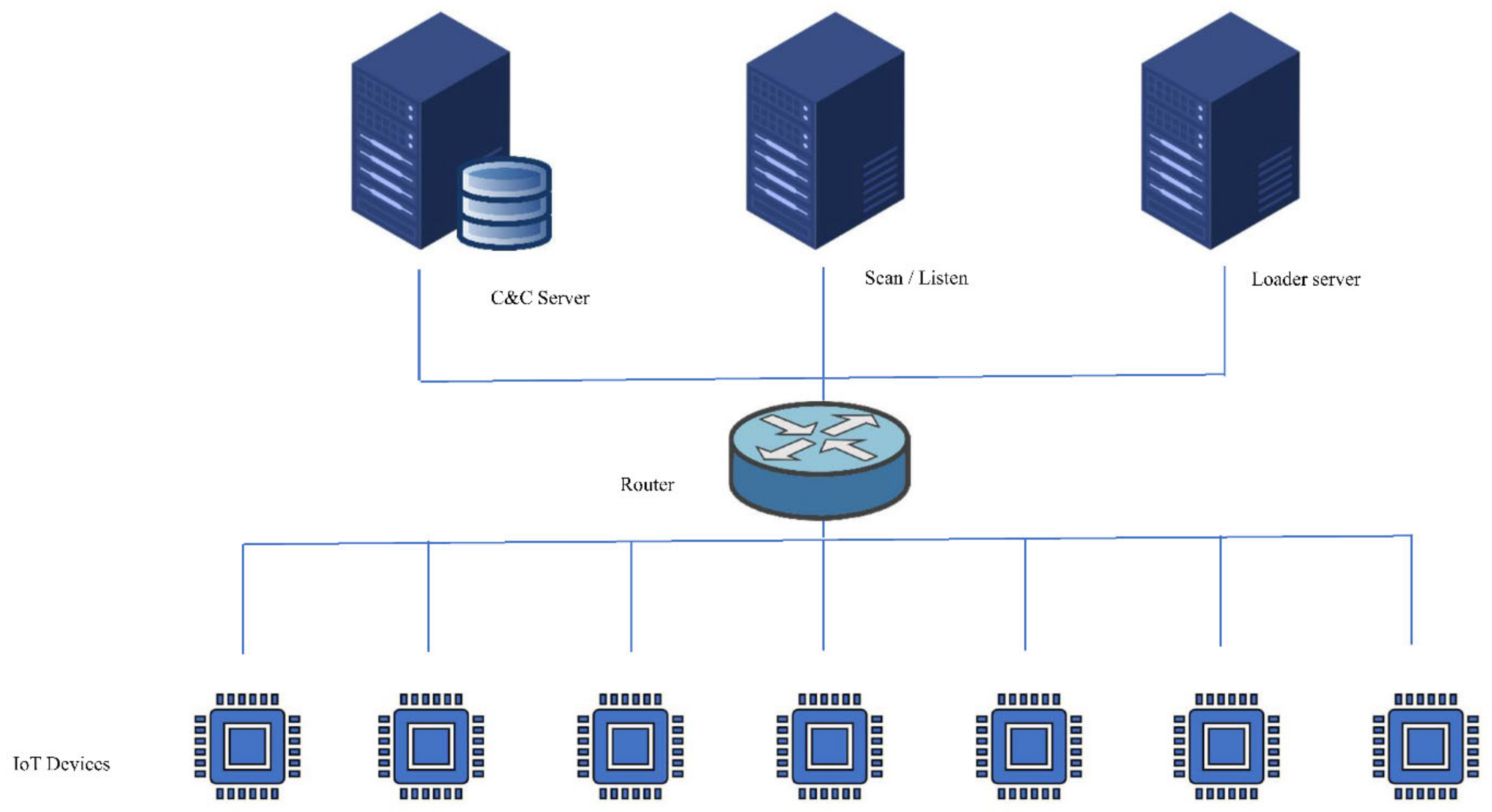
Sensors, Free Full-Text
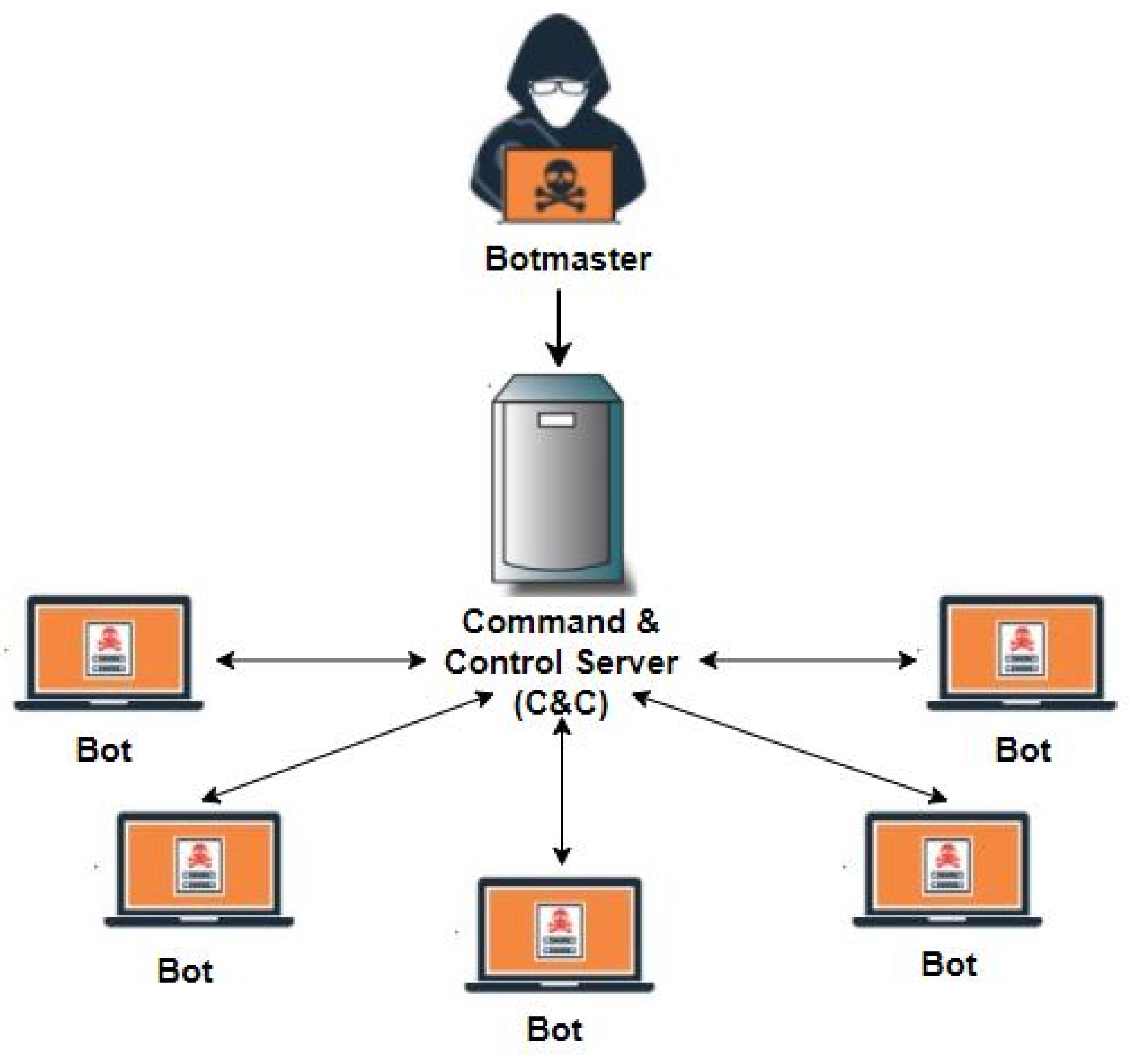
Symmetry, Free Full-Text