Detecting Linux Anti-Forensics: Timestomping
Por um escritor misterioso
Last updated 26 abril 2025
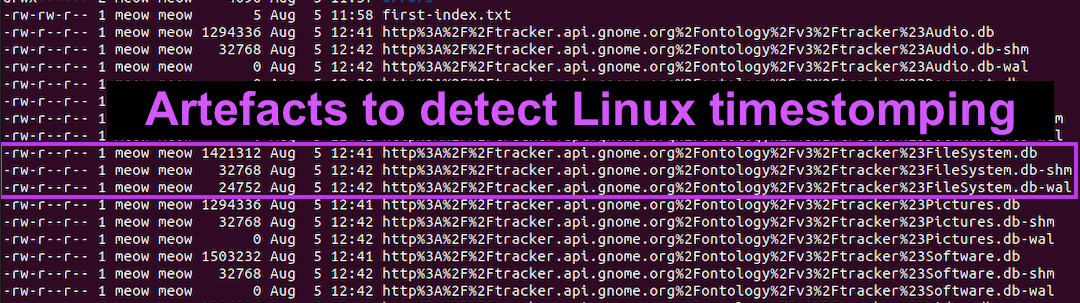
#160; Threat actors can modify the timestamps on malicious files to evade detection. This technique has been used time and time again across va

Detecting Linux Anti-Forensics: Timestomping
Anti-Forensics Techniques - Cynet

Anti-forensics: Furthering digital forensic science through a new

Anti-forensics in ext4: On secrecy and usability of timestamp

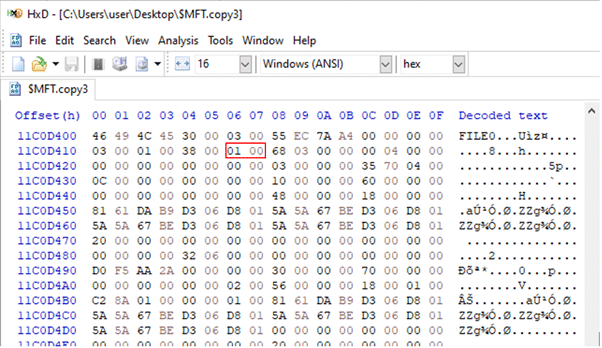
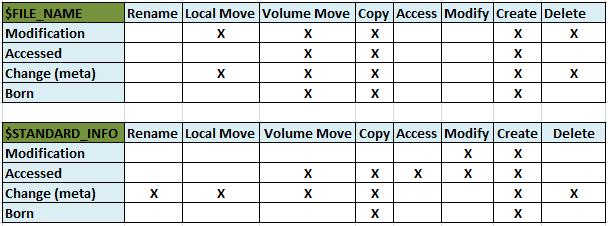
Windows MACB Timestamps (NTFS Forensics)

Lina L. en LinkedIn: Detecting Linux Anti-Forensics: Timestomping

Defence Evasion Technique: Timestomping Detection – NTFS Forensics

Anti-forensics: Furthering digital forensic science through a new

Detecting Linux Anti-Forensics: Timestomping

Anti-forensics: Furthering digital forensic science through a new
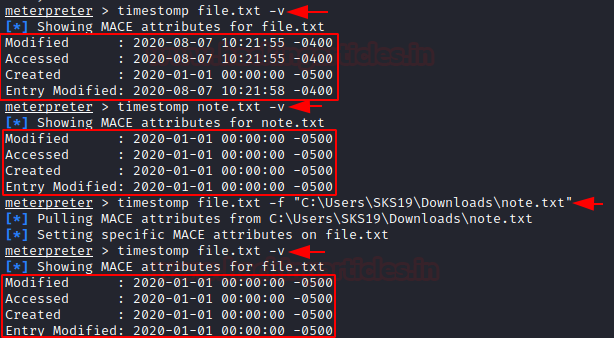
Anti-Forensic: Swipe Footprint with Timestomp - Hacking Articles

Windows MACB Timestamps (NTFS Forensics)
SANS Digital Forensics and Incident Response Blog

PDF) Detection and Mitigation of Anti-Forensics
![Lol Hack] Script De Graça - Evade/Skillshot/Autofarm + - League Of](https://cdn.dfg.com.br/itemimages/935620138-lol-hack-script-de-graca-evade-skillshot-autofarm-TRH2.webp)




![Desapego Games - League of Legends (LOL) > [PROMOÇÃO] SCRIPT COMPLETO KITE, ORBWALKER, EVADE +](https://desapegogames.com.br/assets/site/imagens/anuncios/2022/11/01/a69fefbdd4d72ba0922dbaaa065f39fa.jpg)







:max_bytes(150000):strip_icc()/PDX_OaksAmusementPark2WEB-3ac969ec01d04140858a67cce80a2f92.jpg)
