Cybercriminals are circumventing email security with image-based
Por um escritor misterioso
Last updated 27 abril 2025
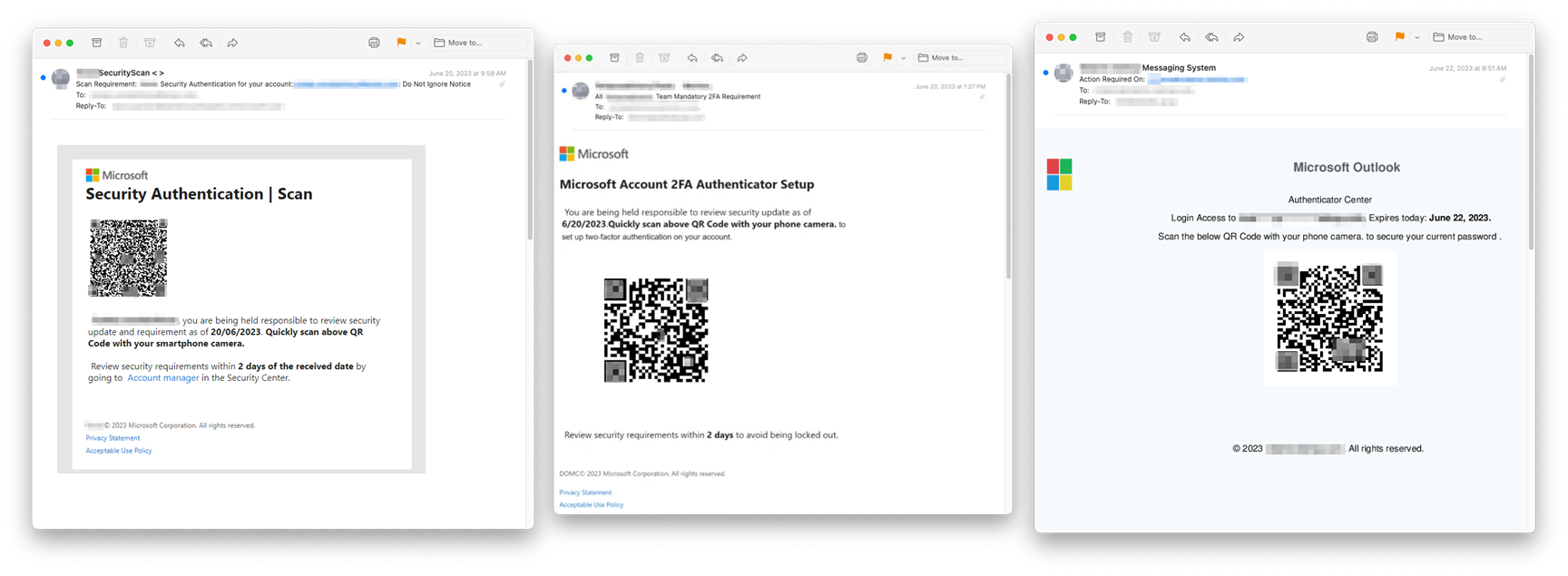
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
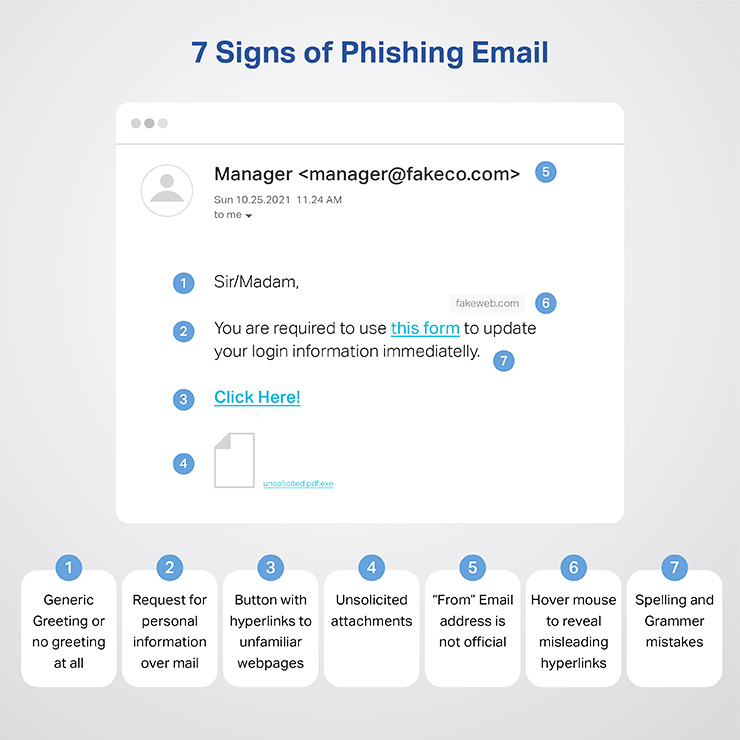
What is Phishing Email: Examples, Types, Techniques & more

Threat Actors Using Google AMP To Evade Phishing Attacks

Understanding Phishing Emails: Why They Slip Through Spam Filters

Microsoft report shows increasing sophistication of cyber threats - Microsoft On the Issues

Cybercriminals are circumventing email security with image-based scams

LLMs lower the barrier for entry into cybercrime - Help Net Security

Novel SMTP Smuggling Technique Slips Past DMARC, Email Protections

Applying OSINT to Cyber Crime Investigations - Blackdot Solutions

New Report Finds 25% of Phishing Attacks Circumvent Office 365 Security - Security News