Tricks and COMfoolery: How Ursnif (Gozi) Evades Detection
Por um escritor misterioso
Last updated 25 abril 2025

In February we saw a resurgence of Ursnif (also known as Gozi), a credential-stealing Trojan. Learn how Ursnif bypasses an attack surface reduction rule.
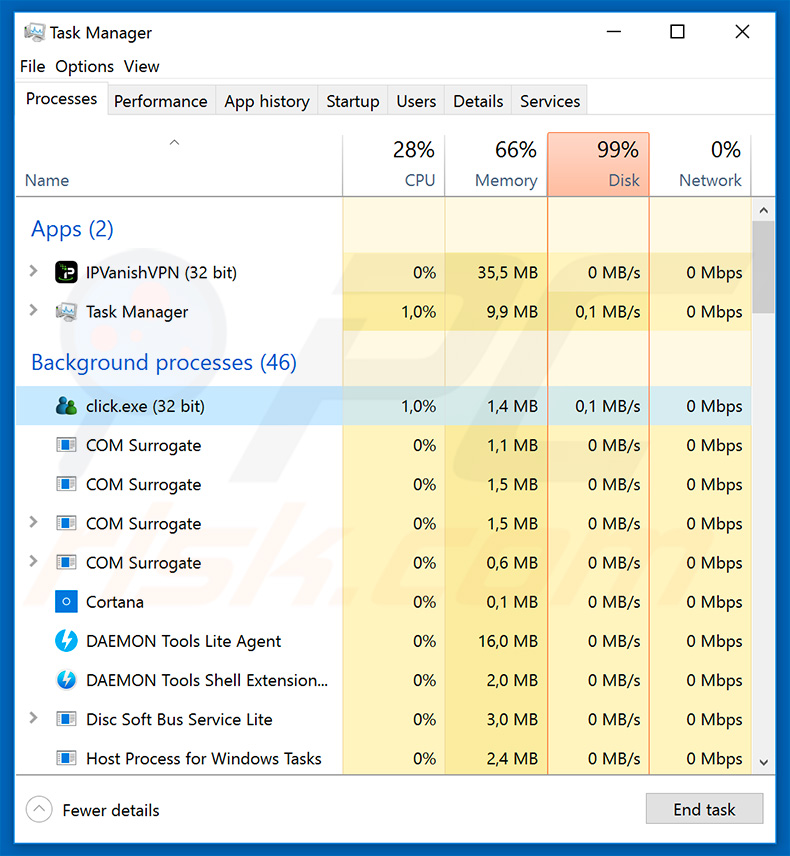
Ursnif Trojan - Malware removal instructions (updated)
Gozi: The Malware with a Thousand Faces - Check Point Research
Malware Analysis — Gozi/Ursnif Downloader, by ka1d0
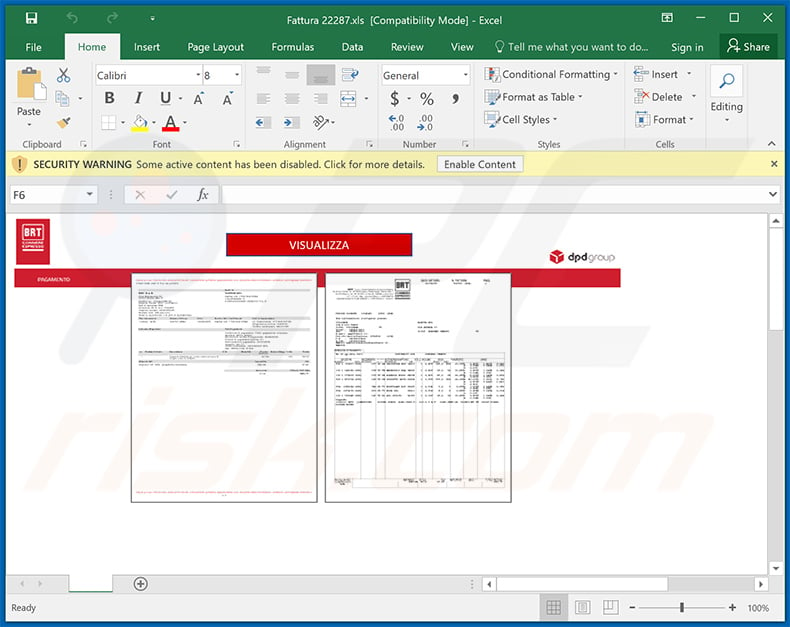
Ursnif Trojan - Malware removal instructions (updated)
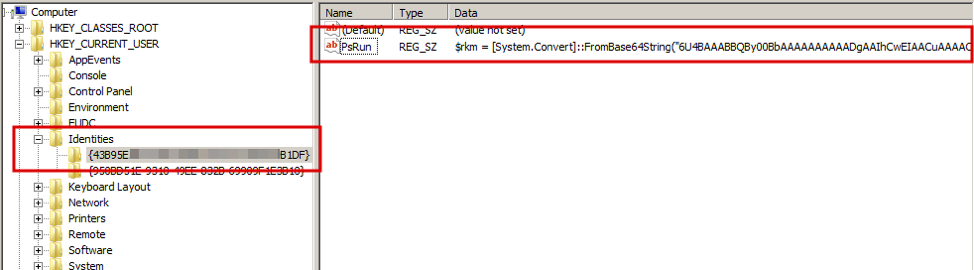
SAIGON, the Mysterious Ursnif Fork

Use behavioral analysis to detect a new Ursnif banking Trojan campaign in Japan
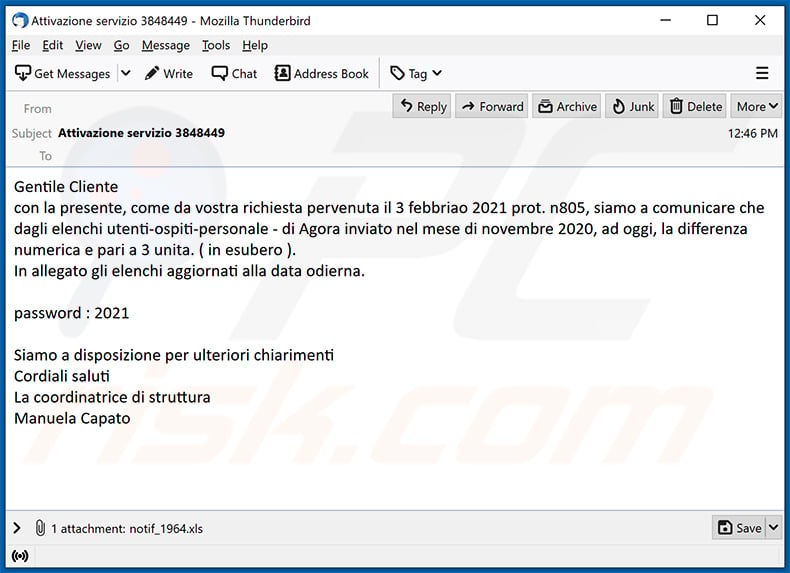
Ursnif Trojan - Malware removal instructions (updated)
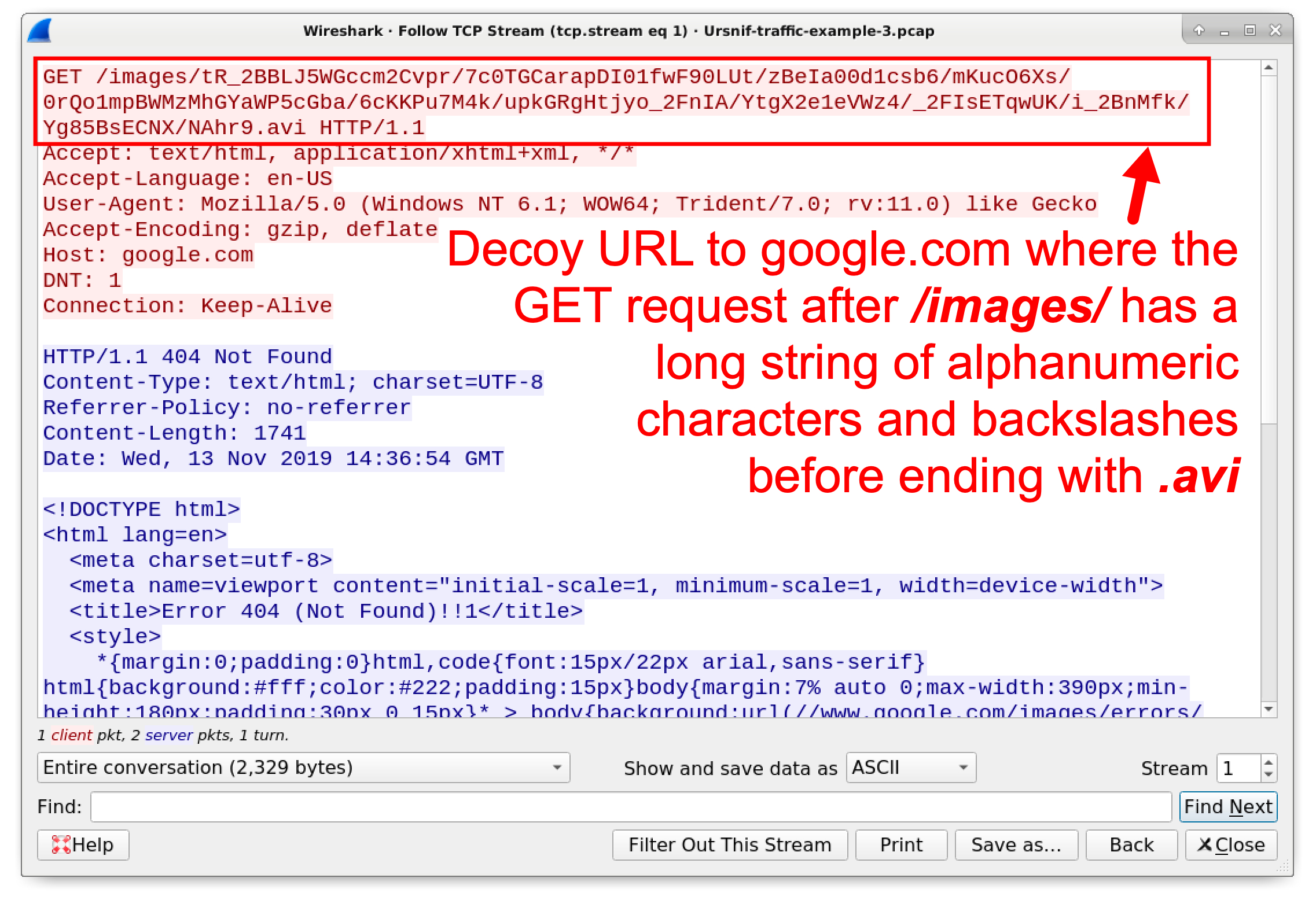
Wireshark Tutorial: Examining Ursnif Infections
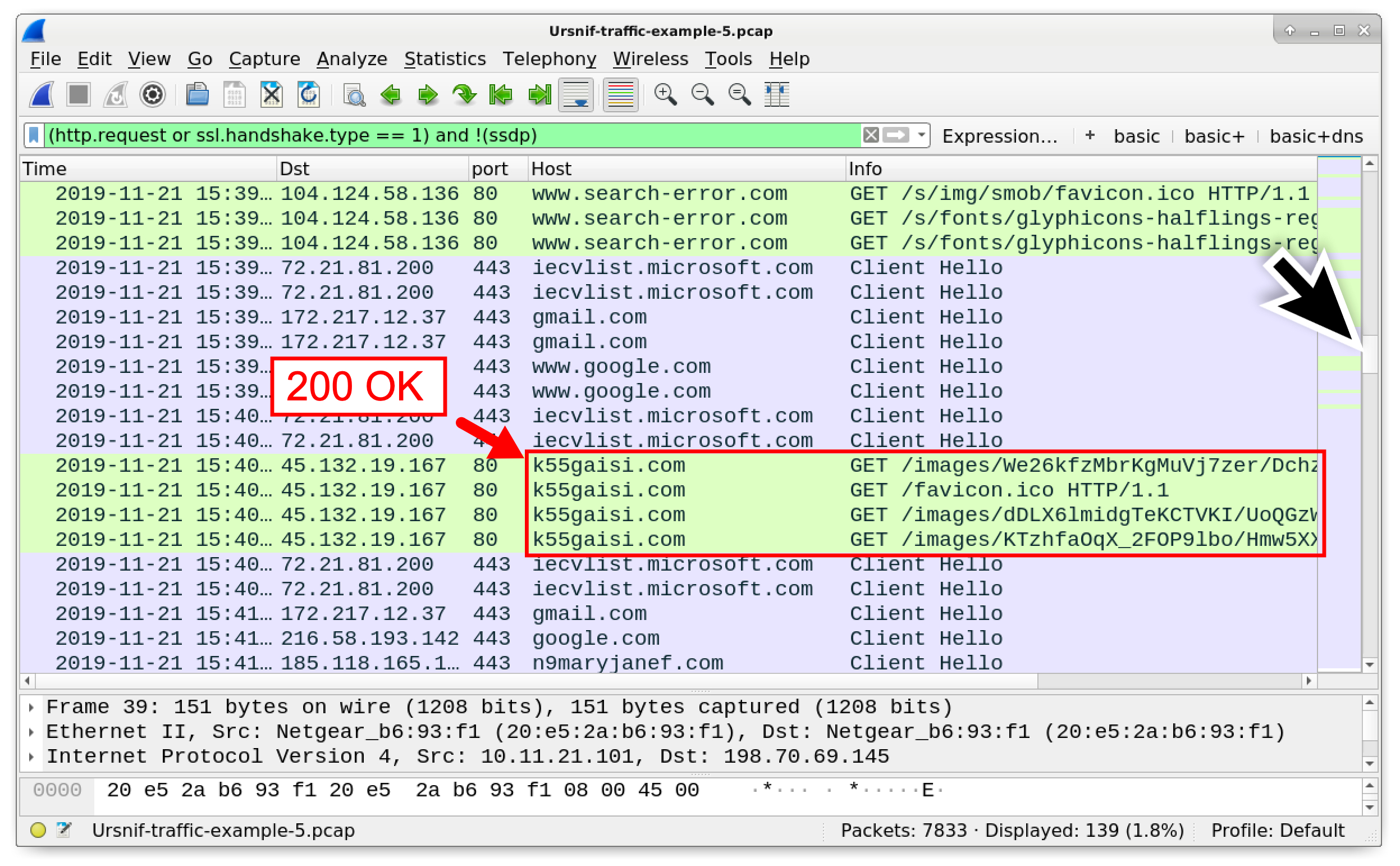
Wireshark Tutorial: Examining Ursnif Infections
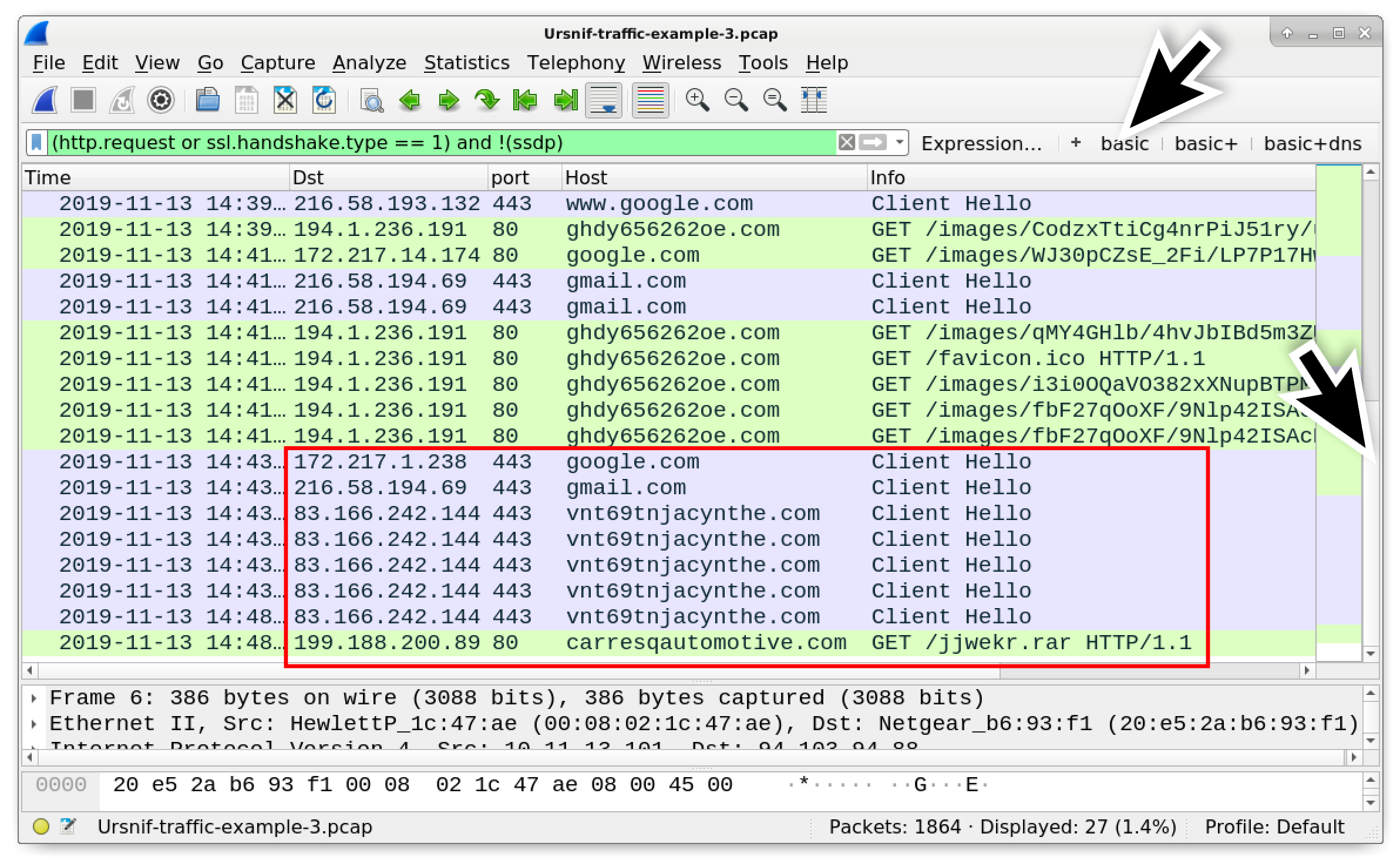
Wireshark Tutorial: Examining Ursnif Infections

Tricks and COMfoolery: How Ursnif (Gozi) Evades Detection

Tricks and COMfoolery: How Ursnif (Gozi) Evades Detection
Use behavioral analysis to detect a new Ursnif banking Trojan campaign in Japan