Blunder (Easy)
Por um escritor misterioso
Last updated 15 março 2025
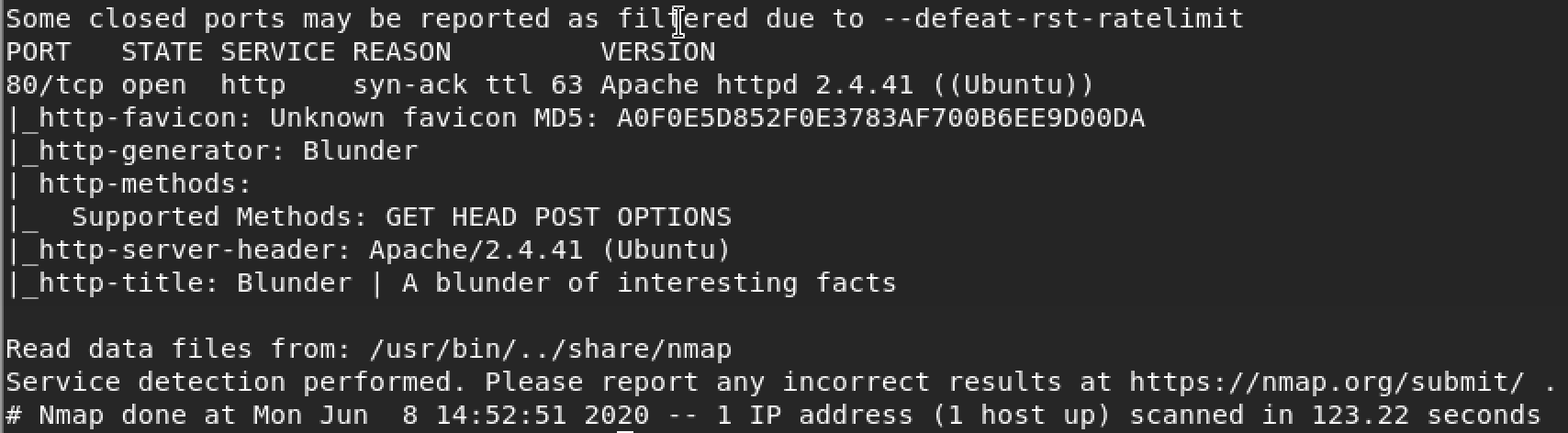
Blunder is an Easy difficulty Linux machine that features a Bludit CMS instance running on port 80. The website contains various facts about different genres. Using GoBuster, we identify a text file that hints to the existence of user fergus, as well as an admin login page that is protected against brute force. An exploit that bypasses the brute force protection is identified, and a dictionary attack is run against the login form. This attack grants us access to the admin panel as fergus. A GitHub issue detailing an arbitrary file upload and directory traversal vulnerability is identified, which is used to gain a shell as www-data. The system is enumerated and a newer version of the Bludit CMS is identified in the /var/www folder. The updated version contains the SHA1 hash of user hugo's password. The password can be cracked online, allowing us to move laterally to this user. Enumeration reveals that the user can run commands as any system user apart from root using sudo. The sudo binary is identified to be outdated, and vulnerable to CVE-2019-14287. Successful exploitation of this vulnerability returns a root shell.

Hair Off Instant Eyebrow Shapers - Fast, Easy, & Mistake Proof Waxing Strips - Natural & Pain-Free Eyebrow Waxing Kit -Wax Strips for Hair Removal for All Skin Types (18
Jerome K. Jerome quote: It is easy enough to say that poverty is no

Hack the Box: Blunder. This is the first machine I've done on…, by Samantha

Sochi and Akhmat's goalkeepers horrendeus blunder gifts the easy goal - Soccer - OneFootball on Sports Illustrated

chess mate on X: “The blunders are all there on the board, waiting to be made.” – Savielly Tartakower Follow on Insta/ FB/ Twitter for more: @chessomate #chessomate #cheerstochess . . . #

Major cryptography blunder in Java enables “psychic paper” forgeries
hackthebox.eu: Blunder Walkthrough —

Easy Holiday Makeup Monika Blunder
Common Opening Traps and Blunders 1. e4 - Part 3