A fuzzer and a symbolic executor walk into a cloud
Por um escritor misterioso
Last updated 13 março 2025

Finding bugs in programs is hard. Automating the process is even harder. We tackled the harder problem and produced two production-quality bug-finding systems: GRR, a high-throughput fuzzer, and PySymEmu (PSE), a binary symbolic executor with support for concrete inputs. From afar, fuzzing is a dumb, brute-force method that works surprisingly well, and symbolic execution is…

A Survey of Symbolic Execution Tools

How We Fared in the Cyber Grand Challenge

Breaking Obfuscated Programs with Symbolic Execution
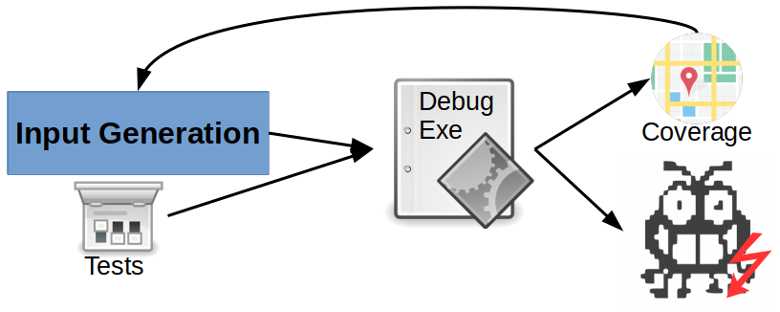
Random ramblings of a security nerd - Security
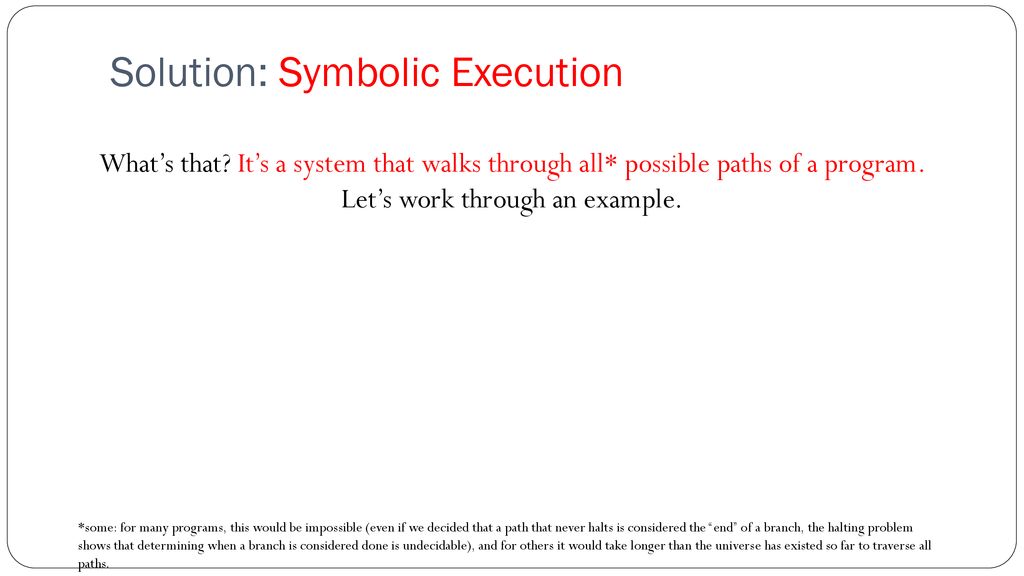
Fuzzing and Symbolic Execution - ppt download

Enhancing Symbolic Execution with Veritesting, June 2016

A Systematic Review of Search Strategies in Dynamic Symbolic Execution - ScienceDirect

Fuzz testing - Automated Injection of Invalid Data

Fuzzing: Hack, Art, and Science, February 2020

Fuzzing Against the Machine: Automate vulnerability research with emulated IoT devices on QEMU 1, Nappa, Antonio, Blazquez, Eduardo, Bassen, Nikias, Lopez-Gomez, Dr. Javier, eBook

What is AI fuzzing? And why it may be the next big cybersecurity threat
GitHub - julieeen/kleefl: Seeding fuzzers with symbolic execution
Why symbolic execution is the leading-edge method for generating test values - DEV Community
fuzzing/docs/afl-based-fuzzers-overview.md at master · google/fuzzing · GitHub

FUZZING HARD-TO-COVER CODE



![Source] Save & Get All Server Triggers ( Executor Source )](https://i.imgur.com/cEjHuCg.png)




![Romance is a Bonus Book [Dorama] - Na Nossa Estante](https://i0.wp.com/3.bp.blogspot.com/-_zMIvL3IQk4/XLj8dtmZ0ZI/AAAAAAAAZQo/Fo37Zdlkz1g9JY7SOCatqISGDBgU6bYQQCLcBGAs/s1600/romance%2Bis%2Ba%2Bbook.jpg?ssl=1)







/i.s3.glbimg.com/v1/AUTH_da025474c0c44edd99332dddb09cabe8/internal_photos/bs/2023/V/n/H0mOLfRFytAtjQRm0Q9Q/334299766-215329534401453-3962671493572446007-n.jpg)